
In computing, BIOS is firmware used to provide runtime services for operating systems and programs and to perform hardware initialization during the booting process. The BIOS firmware comes pre-installed on an IBM PC or IBM PC compatible's system board and exists in some UEFI-based systems to maintain compatibility with operating systems that do not support UEFI native operation. The name originates from the Basic Input/Output System used in the CP/M operating system in 1975. The BIOS originally proprietary to the IBM PC has been reverse engineered by some companies looking to create compatible systems. The interface of that original system serves as a de facto standard.

A floppy disk or floppy diskette is a type of disk storage composed of a thin and flexible disk of a magnetic storage medium in a square or nearly square plastic enclosure lined with a fabric that removes dust particles from the spinning disk. Floppy disks store digital data which can be read and written when the disk is inserted into a floppy disk drive (FDD) connected to or inside a computer or other device.
Malware is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types.

This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.

Brain is the industry standard name for a computer virus that was released in its first form on 19 January 1986, and is considered to be the first computer virus for the IBM Personal Computer and compatibles.
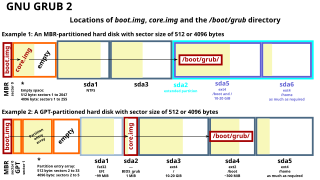
A boot sector is the sector of a persistent data storage device which contains machine code to be loaded into random-access memory (RAM) and then executed by a computer system's built-in firmware.
A boot disk is a removable digital data storage medium from which a computer can load and run (boot) an operating system or utility program. The computer must have a built-in program which will load and execute a program from a boot disk meeting certain standards.
Disk formatting is the process of preparing a data storage device such as a hard disk drive, solid-state drive, floppy disk, memory card or USB flash drive for initial use. In some cases, the formatting operation may also create one or more new file systems. The first part of the formatting process that performs basic medium preparation is often referred to as "low-level formatting". Partitioning is the common term for the second part of the process, dividing the device into several sub-devices and, in some cases, writing information to the device allowing an operating system to be booted from it. The third part of the process, usually termed "high-level formatting" most often refers to the process of generating a new file system. In some operating systems all or parts of these three processes can be combined or repeated at different levels and the term "format" is understood to mean an operation in which a new disk medium is fully prepared to store files. Some formatting utilities allow distinguishing between a quick format, which does not erase all existing data and a long option that does erase all existing data.

Scareware is a form of malware which uses social engineering to cause shock, anxiety, or the perception of a threat in order to manipulate users into buying unwanted software. Scareware is part of a class of malicious software that includes rogue security software, ransomware and other scam software that tricks users into believing their computer is infected with a virus, then suggests that they download and pay for fake antivirus software to remove it. Usually the virus is fictional and the software is non-functional or malware itself. According to the Anti-Phishing Working Group, the number of scareware packages in circulation rose from 2,850 to 9,287 in the second half of 2008. In the first half of 2009, the APWG identified a 585% increase in scareware programs.

The Rainbow 100 is a microcomputer introduced by Digital Equipment Corporation (DEC) in 1982. This desktop unit had a monitor similar to the VT220 and a dual-CPU box with both 4 MHz Zilog Z80 and 4.81 MHz Intel 8088 CPUs. The Rainbow 100 was a triple-use machine: VT100 mode, 8-bit CP/M mode, and CP/M-86 or MS-DOS mode using the 8088. It ultimately failed to in the marketplace which became dominated by the simpler IBM PC and its clones which established the industry standard as compatibility with CP/M became less important than IBM PC compatibility. Writer David Ahl called it a disastrous foray into the personal computer market. The Rainbow was launched along with the similarly packaged DEC Professional and DECmate II which were also not successful. The failure of DEC to gain a significant foothold in the high-volume PC market would be the beginning of the end of the computer hardware industry in New England, as nearly all computer companies located there were focused on minicomputers for large organizations, from DEC to Data General, Wang, Prime, Computervision, Honeywell, and Symbolics Inc.
The Michelangelo virus is a computer virus first discovered on 3 February 1991 in Australia. The virus was designed to infect DOS systems, but did not engage the operating system or make any OS calls. Michelangelo, like all boot sector viruses, operated at the BIOS level. Each year, the virus remained dormant until March 6, the birthday of Renaissance artist Michelangelo. There is no reference to the artist in the virus, and it is doubtful that the virus's developer(s) intended a connection between the virus and the artist. The name was chosen in researchers who noticed the coincidence of the activation date. The actual significance of the date to the author is unknown. Michelangelo is a variant of the already endemic Stoned virus.
Distribution Media Format (DMF) is a format for floppy disks that Microsoft used to distribute software. It allowed the disk to contain 1680 KiB of data on a 31⁄2-inch disk, instead of the standard 1440 KiB. As a side effect, utilities had to specially support the format in order to read and write the disks, which made copying of products distributed on this medium more difficult. An Apple Macintosh computer running Disk Copy 6.3.3 on the Mac OS 7.6 or later operating system can copy and make DMF disks. The first Microsoft software product that uses DMF for distribution were the "c" revisions of Office 4.x. It also was the first software product to use CAB files, then called "Diamond".
Form was a boot sector virus isolated in Switzerland in the summer of 1990 which became very common worldwide. The origin of Form is widely listed as Switzerland, but this may be an assumption based on its isolation locale. The only notable characteristics of Form are that it infects the boot sector instead of the Master Boot Record (MBR) and the clicking noises associated with some infections. Infections under Form can result in severe data damage if operating system characteristics are not identical to those Form assumes.

The Ping-Pong virus is a boot sector virus discovered on March 1, 1988, at the Politecnico di Torino in Italy. It was likely the most common and best known boot sector virus until outnumbered by the Stoned virus.
A self-booting disk is a floppy disk for home computers or personal computers that loads—or boots—directly into a standalone application when the system is turned on, bypassing the operating system. This was common, even standard, on some computers in the late 1970s to early 1990s. Video games were the type of application most commonly distributed using this technique.

The IBM JX was a personal computer released in 1984 into the Japanese, Australian and New Zealand markets. Designed in Japan, it was based on the technology of the IBM PCjr and was designated the IBM 5511. It was targeted in the Australasian market towards the public education sector rather than at consumers, and was sold in three levels: JX (64 KiB), JX2 (128 KiB) and JX3 (256 KiB). Upgrades were available to both 384 KiB and 512 KiB. The JX was the first IBM PC to use 3.5" floppy drives.

A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses.

MS-DOS is an operating system for x86-based personal computers mostly developed by Microsoft. Collectively, MS-DOS, its rebranding as IBM PC DOS, and a few operating systems attempting to be compatible with MS-DOS, are sometimes referred to as "DOS". MS-DOS was the main operating system for IBM PC compatibles during the 1980s, from which point it was gradually superseded by operating systems offering a graphical user interface (GUI), in various generations of the graphical Microsoft Windows operating system.

The floppy disk is a data storage and transfer medium that was ubiquitous from the mid-1970s well into the 2000s. Besides the 3½-inch and 5¼-inch formats used in IBM PC compatible systems, or the 8-inch format that preceded them, many proprietary floppy disk formats were developed, either using a different disk design or special layout and encoding methods for the data held on the disk.
The IBM Personal Computer Basic, commonly shortened to IBM BASIC, is a programming language first released by IBM with the IBM Personal Computer, Model 5150 in 1981. IBM released four different versions of the Microsoft BASIC interpreter, licensed from Microsoft for the PC and PCjr. They are known as Cassette BASIC, Disk BASIC, Advanced BASIC (BASICA), and Cartridge BASIC. Versions of Disk BASIC and Advanced BASIC were included with IBM PC DOS up to PC DOS 4. In addition to the features of an ANSI standard BASIC, the IBM versions offered support for the graphics and sound hardware of the IBM PC line. Source code could be entered with a full-screen editor, and limited facilities were provided for rudimentary program debugging. IBM also released a version of the Microsoft BASIC compiler for the PC concurrently with the release of PC DOS 1.10 in 1982.











