Capability-based security is a concept in the design of secure computing systems, one of the existing security models. A capability is a communicable, unforgeable token of authority. It refers to a value that references an object along with an associated set of access rights. A user program on a capability-based operating system must use a capability to access an object. Capability-based security refers to the principle of designing user programs such that they directly share capabilities with each other according to the principle of least privilege, and to the operating system infrastructure necessary to make such transactions efficient and secure. Capability-based security is to be contrasted with an approach that uses traditional UNIX permissions and Access Control Lists.
In computer security, a sandbox is a security mechanism for separating running programs, usually in an effort to mitigate system failures and/or software vulnerabilities from spreading. The isolation metaphor is taken from the idea of children who do not play well together, so each is given their own sandbox to play in alone. It is often used to execute untested or untrusted programs or code, possibly from unverified or untrusted third parties, suppliers, users or websites, without risking harm to the host machine or operating system. A sandbox typically provides a tightly controlled set of resources for guest programs to run in, such as storage and memory scratch space. Network access, the ability to inspect the host system, or read from input devices are usually disallowed or heavily restricted.
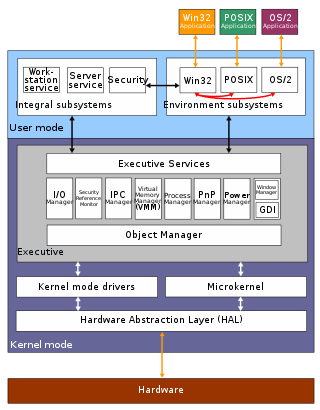
The architecture of Windows NT, a line of operating systems produced and sold by Microsoft, is a layered design that consists of two main components, user mode and kernel mode. It is a preemptive, reentrant multitasking operating system, which has been designed to work with uniprocessor and symmetrical multiprocessor (SMP)-based computers. To process input/output (I/O) requests, it uses packet-driven I/O, which utilizes I/O request packets (IRPs) and asynchronous I/O. Starting with Windows XP, Microsoft began making 64-bit versions of Windows available; before this, there were only 32-bit versions of these operating systems.
In the context of the Microsoft Windows NT line of operating systems, a Security Identifier (SID) is a unique, immutable identifier of a user, user group, or other security principal. A security principal has a single SID for life, and all properties of the principal, including its name, are associated with the SID. This design allows a principal to be renamed without affecting the security attributes of objects that refer to the principal.
OAuth is an open standard for access delegation, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon, Google, Meta Platforms, Microsoft, and Twitter to permit users to share information about their accounts with third-party applications or websites.
In computer systems, an access token contains the security credentials for a login session and identifies the user, the user's groups, the user's privileges, and, in some cases, a particular application. In some instances, one may be asked to enter an access token rather than the usual password.
Mandatory Integrity Control (MIC) is a core security feature of Windows Vista and later that adds mandatory access control to running processes based on their Integrity Level (IL). The IL represents the level of trustworthiness of an object. This mechanism's goal is to restrict the access permissions for potentially less trustworthy contexts, compared with other contexts running under the same user account that are more trusted.
Security Support Provider Interface (SSPI) is a component of Windows API that performs security-related operations such as authentication.
Flutter is an open-source UI software development kit created by Google. It can be used to develop cross platform applications from a single codebase for the web, Fuchsia, Android, iOS, Linux, macOS, and Windows. First described in 2015, Flutter was released in May 2017. Flutter is used internally by Google in apps such as Google Pay and Google Earth as well as by other software developers including ByteDance and Alibaba.
Permissions are a means of controlling and regulating access to specific system- and device-level functions by software. Typically, types of permissions cover functions that may have privacy implications, such as the ability to access a device's hardware features, and personal data. Permissions are typically declared in an application's manifest, and certain permissions must be specifically granted at runtime by the user—who may revoke the permission at any time.
HarmonyOS (HMOS) is a distributed operating system developed by Huawei for smartphones, tablets, smart TVs, smart watches, personal computers and other smart devices. It has a single real-time microkernel design in kernel mode with a single framework: the operating system derives from HarmonyOS NEXT, based on OpenHarmony operating system family that is the user mode of HarmonyOS NEXT system that takes full L0-L2 source code derived from LiteOS roots that selects suitable kernels from the kernel abstraction layer. The operating system was officially launched by Huawei in August 2019.
Android devices have the ability to run virtual machines or emulate other operating systems. It does this either via desktop virtualization, platform virtualization, or emulation via compatibility layer.

Huawei Mobile Services (HMS) is a collection of proprietary services and high level application programming interfaces (APIs) developed by Huawei Technologies Co., Ltd. Its hub known as HMS Core serves as a toolkit for app development on Huawei devices. HMS is typically installed on Huawei devices on top of running HarmonyOS operating system, and on its earlier devices running the Android operating system with EMUI including devices already distributed with Google Mobile Services. Alongside, HMS Core Wear Engine for Android phones with lightweight based LiteOS wearable middleware app framework integration connectivity like notifications, status etc.

DevEco Studio is the official integrated development environment (IDE) for Huawei's HarmonyOS operating system, built on JetBrains' IntelliJ IDEA software and Huawei's SmartAssist designed specifically for HarmonyOS development. It is available for download on Microsoft Windows and macOS based operating systems.
The version history of the HarmonyOS distributed operating system began with the public release of the HarmonyOS 1.0 for Honor Vision smart TVs on August 9, 2019. The first expanded commercial version of the Embedded, IoT AI, Edge computing based operating system, HarmonyOS 2.0, was released on June 2, 2021, for phones, tablets, smartwatches, smart speakers, routers, and internet of things. Beforehand, DevEco Studio, the HarmonyOS app development IDE, was released in September 2020 together with the HarmonyOS 2.0 Beta. HarmonyOS is developed by Huawei. New major releases are announced at the Huawei Developers Conference (HDC) in the fourth quarter of each year together with the first public beta version of the operating system's next major version. The next major stable version is then released in the third to fourth quarter of the following year.

OpenAtom OpenHarmony, or abbreviated as OpenHarmony (OHOS), is a family of open-source distributed operating systems based on HarmonyOS derived from LiteOS, donated the L0-L2 branch source code by Huawei to the OpenAtom Foundation. Similar to HarmonyOS, the open-source distributed operating system is designed with a layered architecture, which consists of four layers from the bottom to the top, i.e., the kernel layer, system service layer, framework layer, and application layer. It is also an extensive collection of free software, which can be used as an operating system or can be used in parts with other operating systems via Kernel Abstraction Layer subsystems.
The HarmonyOS App Pack or the App file, identified with the file extension ".app", serves as the file format used by the HarmonyOS operating system. It functions as a native HarmonyOS app for distribution and installation through Huawei AppGallery, or for distribution through Huawei Ability Gallery in respect of installation-free apps under both former classic dual-framework and current HarmonyOS NEXT system of unified OpenHarmony app framework. The App file is also used by a number of other open source HarmonyOS-based operating systems such as OpenHarmony and Oniro OS-based operating systems for distribution and installation of applications, video games and middleware. Including non OpenHarmony-based operating systems, such as GNU Linux-based Unity Operating System that supports the app file format.
HarmonyOS NEXT is a proprietary distributed operating system and an iteration of HarmonyOS, developed by Huawei to support only HarmonyOS native apps. The operating system base is primarily aimed at software and hardware developers that deal directly with Huawei. It does not include Android's AOSP core and is incompatible with Android applications.
ArkGraphics 3D is an open source, open standard low-level, low-overhead hardware-accelerated 3D graphic and compute shader API developed by Huawei as a subset of Ark Engine for HarmonyOS and OpenAtom OpenHarmony. It is compared to low-level APIs on other platforms such as Apple Metal, Vulkan and DirectX 12.
ArkTS is a high-level general-purpose, multi-paradigm, compiled programming language developed by Huawei which is a superset of open-source TypeScript, in turn a superset of JavaScript formerly used in July 2022 HarmonyOS 3.0 version, alongside its evolved percussor, extended TypeScript (eTS) built for HarmonyOS development as a shift towards Declarative programming. ArkTS compiles to machine code via it's Ahead-of-time compilation Ark Compiler. ArkTS was first released in September 30, 2021 on OpenHarmony, and the ArkTS toolchain has shipped in DevEco Studio since version 3.1, released in 2022. Since, OpenHarmony 4.0 release on October 26, 2023, ArkTS APIs has been added to the open source community to contribute.

