
Security-Enhanced Linux (SELinux) is a Linux kernel security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC).
This is a list of operating systems specifically focused on security. General-purpose operating systems may be secure in practice, without being specifically "security-focused".
RSBAC is an open source access control framework for current Linux kernels, which has been in stable production use since January 2000.
Exec Shield is a project started at Red Hat, Inc in late 2002 with the aim of reducing the risk of worm or other automated remote attacks on Linux systems. The first result of the project was a security patch for the Linux kernel that emulates an NX bit on x86 CPUs that lack a native NX implementation in hardware. While the Exec Shield project has had many other components, some people refer to this first patch as Exec Shield.
In computer security, mandatory access control (MAC) refers to a type of access control by which the operating system constrains the ability of a subject or initiator to access or generally perform some sort of operation on an object or target. In practice, a subject is usually a process or thread; objects are constructs such as files, directories, TCP/UDP ports, shared memory segments, IO devices, etc. Subjects and objects each have a set of security attributes. Whenever a subject attempts to access an object, an authorization rule enforced by the operating system kernel examines these security attributes and decides whether the access can take place. Any operation by any subject on any object is tested against the set of authorization rules to determine if the operation is allowed. A database management system, in its access control mechanism, can also apply mandatory access control; in this case, the objects are tables, views, procedures, etc.

Linux-VServer is a virtual private server implementation that was created by adding operating system-level virtualization capabilities to the Linux kernel. It is developed and distributed as open-source software.

The Openwall Project is a source for various software, including Openwall GNU/*/Linux (Owl), a security-enhanced Linux distribution designed for servers. Openwall patches and security extensions have been included into many major Linux distributions.
seccomp is a computer security facility in the Linux kernel. seccomp allows a process to make a one-way transition into a "secure" state where it cannot make any system calls except exit , sigreturn , read and write to already-open file descriptors. Should it attempt any other system calls, the kernel will terminate the process with SIGKILL or SIGSYS. In this sense, it does not virtualize the system's resources but isolates the process from them entirely.

AppArmor is a Linux kernel security module that allows the system administrator to restrict programs' capabilities with per-program profiles. Profiles can allow capabilities like network access, raw socket access, and the permission to read, write, or execute files on matching paths. AppArmor supplements the traditional Unix discretionary access control (DAC) model by providing mandatory access control (MAC). It has been included in the mainline Linux kernel since version 2.6.36 and its development has been supported by Canonical since 2009.
Linux Security Modules (LSM) is a framework that allows the Linux kernel to support a variety of computer security models while avoiding favoritism toward any single security implementation. The framework is licensed under the terms of the GNU General Public License and is a standard part of the Linux kernel since Linux 2.6. AppArmor, SELinux, Smack, and TOMOYO Linux are the currently accepted modules in the official kernel.
CE Linux Forum, otherwise known as the Consumer Electronics Linux Forum or CELF, is a non-profit organization that works to advance Linux as an open source platform for consumer electronics (CE) devices. It has a primarily technical focus, working on specifications, implementations, conferences and testing to help Linux developers improve Linux for use in CE products.
kexec, abbreviated from kernel execution and analogous to the Unix/Linux kernel call exec, is a mechanism of the Linux kernel that allows booting of a new kernel from the currently running one. Essentially, kexec skips the bootloader stage and hardware initialization phase performed by the system firmware, and directly loads the new kernel into main memory and starts executing it immediately. This avoids the long times associated with a full reboot, and can help systems to meet high-availability requirements by minimizing downtime.
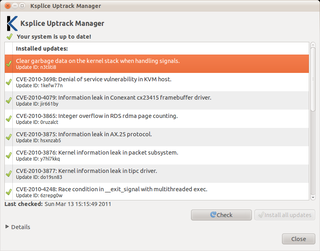
Ksplice is an open-source extension of the Linux kernel that allows security patches to be applied to a running kernel without the need for reboots, avoiding downtimes and improving availability. Ksplice supports only the patches that do not make significant semantic changes to kernel's data structures.
Tor-ramdisk is an i686 uClibc-based micro Linux distribution whose only purpose is to host a Tor server in an environment that maximizes security and privacy. Security is enhanced in Tor-ramdisk by employing a monolithically compiled GRSEC/PaX patched kernel and hardened system tools. Privacy is enhanced by turning off logging at all levels so that even the Tor operator only has access to minimal information. Finally, since everything runs in ephemeral memory, no information survives a reboot, except for the Tor configuration file and the private RSA key, which may be exported and imported by FTP or SCP.

The Linux kernel is a free and open-source, monolithic, Unix-like operating system kernel. The Linux family of operating systems is based on this kernel and deployed on both traditional computer systems such as personal computers and servers, usually in the form of Linux distributions, and on various embedded devices such as routers, wireless access points, PBXes, set-top boxes, FTA receivers, smart TVs, PVRs, and NAS appliances. While the adoption of the Linux kernel in desktop computer operating system is low, Linux-based operating systems dominate nearly every other segment of computing, from mobile devices to mainframes. Since November 2017, all of the world's 500 most powerful supercomputers run Linux. The Android operating system for tablet computers, smartphones, and smartwatches also uses the Linux kernel.

Linux-libre is an operating system kernel and a GNU package.
LXC is an operating-system-level virtualization method for running multiple isolated Linux systems (containers) on a control host using a single Linux kernel.
In computer security, the Linux Intrusion Detection System (LIDS) is a patch to the Linux kernel and associated administrative tools that enhances the kernel's security by implementing mandatory access control (MAC). When LIDS is in effect all system network administration operations, chosen file access, any capability use, raw device, memory, and I/O access can be made impossible, even for root. One can define which programs can access specific files. It uses and extends the system capabilities bounding set to control the whole system and adds some network and filesystem security features to the kernel to enhance the security. One can finely tune the security protections online, hide sensitive processes, receive security alerts through the network, and more. LIDS currently supports Linux kernel 2.6, 2.4. LIDS is released under the terms of the GNU General Public License (GPL).

Smack is a Linux kernel security module that protects data and process interaction from malicious manipulation using a set of custom mandatory access control (MAC) rules, with simplicity as its main design goal. It has been officially merged since the Linux 2.6.25 release, it was the main access control mechanism for the MeeGo mobile Operating System. It is also used to sandbox HTML5 web applications in the Tizen architecture, in the commercial Wind River Linux solutions for embedded device development, in Philips Digital TV products., and in Intel's Ostro OS for IoT devices.
KernelCare is a live kernel patching service that provides security patches and bugfixes for a range of popular Linux kernels that can be installed without rebooting the system.








