
In computing, BIOS is firmware used to provide runtime services for operating systems and programs and to perform hardware initialization during the booting process. The BIOS firmware comes pre-installed on an IBM PC or IBM PC compatible's system board and exists in UEFI-based systems too. The name originates from the Basic Input/Output System used in the CP/M operating system in 1975. The BIOS originally proprietary to the IBM PC has been reverse engineered by some companies looking to create compatible systems. The interface of that original system serves as a de facto standard.

In computing, booting is the process of starting a computer as initiated via hardware such as a button or by a software command. After it is switched on, a computer's central processing unit (CPU) has no software in its main memory, so some process must load software into memory before it can be executed. This may be done by hardware or firmware in the CPU, or by a separate processor in the computer system.

A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed and often masks its existence or the existence of other software. The term rootkit is a compound of "root" and the word "kit". The term "rootkit" has negative connotations through its association with malware.
Logical block addressing (LBA) is a common scheme used for specifying the location of blocks of data stored on computer storage devices, generally secondary storage systems such as hard disk drives. LBA is a particularly simple linear addressing scheme; blocks are located by an integer index, with the first block being LBA 0, the second LBA 1, and so on.

Multi-booting is the act of installing multiple operating systems on a single computer, and being able to choose which one to boot. The term dual-booting refers to the common configuration of specifically two operating systems. Multi-booting may require a custom boot loader.
dd is a command-line utility for Unix, Unix-like operating systems and beyond, the primary purpose of which is to convert and copy files.

The SRM firmware is the boot firmware written by Digital Equipment Corporation (DEC) for computer systems based on the DEC Alpha microprocessor. SRM are the initials of (Alpha) System Reference Manual, the publication detailing the Alpha AXP architecture and which specified various features of the SRM firmware.

The GUID Partition Table (GPT) is a standard for the layout of partition tables of a physical computer storage device, such as a hard disk drive or solid-state drive, using universally unique identifiers, which are also known as globally unique identifiers (GUIDs). Forming a part of the Unified Extensible Firmware Interface (UEFI) standard, it is nevertheless also used for some BIOS systems, because of the limitations of master boot record (MBR) partition tables, which use 32 bits for logical block addressing (LBA) of traditional 512-byte disk sectors.
hdparm is a command line program for Linux to set and view ATA hard disk drive hardware parameters and test performance. It can set parameters such as drive caches, sleep mode, power management, acoustic management, and DMA settings. GParted and Parted Magic both include hdparm.
INT 13h is shorthand for BIOS interrupt call 13hex, the 20th interrupt vector in an x86-based computer system. The BIOS typically sets up a real mode interrupt handler at this vector that provides sector-based hard disk and floppy disk read and write services using cylinder-head-sector (CHS) addressing. Modern PC BIOSes also include INT 13h extension functions, originated by IBM and Microsoft in 1992, that provide those same disk access services using 64-bit LBA addressing; with minor additions, these were quasi-standardized by Phoenix Technologies and others as the EDD BIOS extensions.
In Linux systems, initrd is a scheme for loading a temporary root file system into memory, to be used as part of the Linux startup process. initrd and initramfs refer to two different methods of achieving this. Both are commonly used to make preparations before the real root file system can be mounted.

A live USB is a portable USB-attached external data storage device containing a full operating system that can be booted from. The term is reminiscent of USB flash drives but may encompass an external hard disk drive or solid-state drive, though they may be referred to as "live HDD" and "live SSD" respectively. They are the evolutionary next step after live CDs, but with the added benefit of writable storage, allowing customizations to the booted operating system. Live USBs can be used in embedded systems for system administration, data recovery, or test driving, and can persistently save settings and install software packages on the USB device.
In computing, error recovery control (ERC) is a feature of hard disks which allow a system administrator to configure the amount of time a drive's firmware is allowed to spend recovering from a read or write error. Limiting the recovery time allows for improved error handling in hardware or software RAID environments. In some cases, there is a conflict as to whether error handling should be undertaken by the hard drive or by the RAID implementation, which leads to drives being marked as unusable and significant performance degradation, when this could otherwise have been avoided.
Device configuration overlay (DCO) is a hidden area on many of today's hard disk drives (HDDs). Usually when information is stored in either the DCO or host protected area (HPA), it is not accessible by the BIOS, OS, or the user. However, certain tools can be used to modify the HPA or DCO. The system uses the IDENTIFY_DEVICE command to determine the supported features of a given hard drive, but the DCO can report to this command that supported features are nonexistent or that the drive is smaller than it actually is. To determine the actual size and features of a disk, the DEVICE_CONFIGURATION_IDENTIFY command is used, and the output of this command can be compared to the output of IDENTIFY_DEVICE to see if a DCO is present on a given hard drive. Most major tools will remove the DCO in order to fully image a hard drive, using the DEVICE_CONFIGURATION_RESET command. This permanently alters the disk, unlike with the host protected area (HPA), which can be temporarily removed for a power cycle.
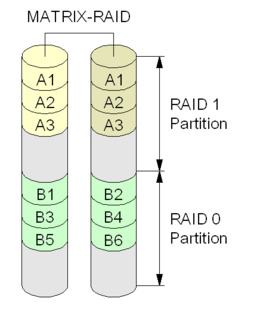
Intel Rapid Storage Technology (RST), until 2010 called Matrix RAID, is a firmware-based RAID solution built into a wide range of Intel chipsets. As of 2020, it includes a RAID system capable of RAID levels 0, 1, 5, and 10, a block level SSD caching accelerator with support for write-back and write-through modes for speed or data protection of any disk or RAID array, and support for intelligent caching, speedy recovery from certain issues, and for PCI Express based drives. Intel RST comes in two variants, RST for desktops, and RSTe for enterprise scenarios, although for many chipsets, the user can choose as both variants will operate correctly.
In Unix-like operating systems, a device file or special file is an interface to a device driver that appears in a file system as if it were an ordinary file. There are also special files in DOS, OS/2, and Windows. These special files allow an application program to interact with a device by using its device driver via standard input/output system calls. Using standard system calls simplifies many programming tasks, and leads to consistent user-space I/O mechanisms regardless of device features and functions.
A trim command allows an operating system to inform a solid-state drive (SSD) which blocks of data are no longer considered to be 'in use' and therefore can be erased internally.
A master boot record (MBR) is a special type of boot sector at the very beginning of partitioned computer mass storage devices like fixed disks or removable drives intended for use with IBM PC-compatible systems and beyond. The concept of MBRs was publicly introduced in 1983 with PC DOS 2.0.
Absolute Home & Office is a proprietary laptop theft recovery software. The persistent security features are built into the firmware of devices. Absolute Home & Office has services of an investigations and recovery team who partners with law enforcement agencies to return laptops to their owners. Absolute Software licensed the name LoJack from the vehicle recovery service LoJack in 2005.

ATATool is freeware software that is used to display and modify ATA disk information from a Microsoft Windows environment. The software is typically used to manage host protected area (HPA) and device configuration overlay (DCO) features and is broadly similar to the hdparm for Linux. Recent versions include support for DCO restore and freeze operations, HPA security (password) operations and simulated bad sectors.









