Related Research Articles

The United States Foreign Intelligence Surveillance Court is a U.S. federal court established under the Foreign Intelligence Surveillance Act of 1978 (FISA) to oversee requests for surveillance warrants against foreign spies inside the United States by federal law enforcement and intelligence agencies. Such requests are made most often by the National Security Agency (NSA) and the Federal Bureau of Investigation (FBI). Congress created FISA and its court as a result of the recommendations by the U.S. Senate's Church Committee.

The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The existence of the NSA was not revealed until 1975.
Computer and network surveillance is the monitoring of computer activity and data stored locally on a computer or data being transferred over computer networks such as the Internet. This monitoring is often carried out covertly and may be completed by governments, corporations, criminal organizations, or individuals. It may or may not be legal and may or may not require authorization from a court or other independent government agencies. Computer and network surveillance programs are widespread today and almost all Internet traffic can be monitored.

Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizations, such as organizations like the NSA and the FBI, but it may also be carried out by corporations. Depending on each nation's laws and judicial systems, the legality of and the permission required to engage in mass surveillance varies. It is the single most indicative distinguishing trait of totalitarian regimes. It is also often distinguished from targeted surveillance.

Keith Brian Alexander is a retired four-star general of the United States Army, who served as director of the National Security Agency, chief of the Central Security Service, and commander of the United States Cyber Command. He previously served as Deputy Chief of Staff, G-2 (Intelligence), United States Army from 2003 to 2005. He assumed the positions of Director of the National Security Agency and Chief of the Central Security Service on August 1, 2005, and the additional duties as Commander United States Cyber Command on May 21, 2010.

NSA warrantless surveillance — also commonly referred to as "warrantless-wiretapping" or "-wiretaps" — refers to the surveillance of persons within the United States, including U.S. citizens, during the collection of notionally foreign intelligence by the National Security Agency (NSA) as part of the Terrorist Surveillance Program. In late 2001, the NSA was authorized to monitor, without obtaining a FISA warrant, the phone calls, Internet activity, text messages and other communication involving any party believed by the NSA to be outside the U.S., even if the other end of the communication lay within the U.S.

MAINWAY is a database maintained by the United States' National Security Agency (NSA) containing metadata for hundreds of billions of telephone calls made through the four largest telephone carriers in the United States: AT&T, SBC, BellSouth and Verizon.
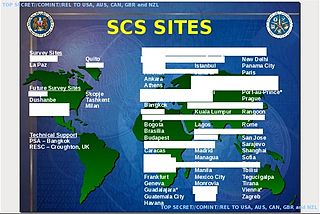
The Special Collection Service (SCS), codenamed F6, is a highly classified joint U.S. Central Intelligence Agency–National Security Agency program charged with inserting eavesdropping equipment in difficult-to-reach places, such as foreign embassies, communications centers, and foreign government installations. Established in the late 1970s and headquartered in Beltsville, Maryland, the SCS has been involved in operations ranging from the Cold War to the Global War on Terrorism.

Pinwale is the code name for a National Security Agency (NSA) collection and retrieval system for so-called "Digital Network Intelligence", including internet e-mail. It is searchable by monitored NSA analysts.

PRISM is a code name for a program under which the United States National Security Agency (NSA) collects internet communications from various U.S. internet companies. The program is also known by the SIGAD US-984XN. PRISM collects stored internet communications based on demands made to internet companies such as Google LLC under Section 702 of the FISA Amendments Act of 2008 to turn over any data that match court-approved search terms. Among other things, the NSA can use these PRISM requests to target communications that were encrypted when they traveled across the internet backbone, to focus on stored data that telecommunication filtering systems discarded earlier, and to get data that is easier to handle.

Boundless Informant is a big data analysis and data visualization tool used by the United States National Security Agency (NSA). It gives NSA managers summaries of the NSA's worldwide data collection activities by counting metadata. The existence of this tool was disclosed by documents leaked by Edward Snowden, who worked at the NSA for the defense contractor Booz Allen Hamilton. Those disclosed documents were in a direct contradiction to the NSA's assurance to United States Congress that it does not collect any type of data on millions of Americans.

XKeyscore is a secret computer system used by the United States National Security Agency (NSA) for searching and analyzing global Internet data, which it collects in real time. The NSA has shared XKeyscore with other intelligence agencies, including the Australian Signals Directorate, Canada's Communications Security Establishment, New Zealand's Government Communications Security Bureau, Britain's Government Communications Headquarters, Japan's Defense Intelligence Headquarters, and Germany's Bundesnachrichtendienst.

The practice of mass surveillance in the United States dates back to wartime monitoring and censorship of international communications from, to, or which passed through the United States. After the First and Second World Wars, mass surveillance continued throughout the Cold War period, via programs such as the Black Chamber and Project SHAMROCK. The formation and growth of federal law-enforcement and intelligence agencies such as the FBI, CIA, and NSA institutionalized surveillance used to also silence political dissent, as evidenced by COINTELPRO projects which targeted various organizations and individuals. During the Civil Rights Movement era, many individuals put under surveillance orders were first labelled as integrationists, then deemed subversive, and sometimes suspected to be supportive of the communist model of the United States' rival at the time, the Soviet Union. Other targeted individuals and groups included Native American activists, African American and Chicano liberation movement activists, and anti-war protesters.

Ongoing news reports in the international media have revealed operational details about the Anglophone cryptographic agencies' global surveillance of both foreign and domestic nationals. The reports mostly emanate from a cache of top secret documents leaked by ex-NSA contractor Edward Snowden, which he obtained whilst working for Booz Allen Hamilton, one of the largest contractors for defense and intelligence in the United States. In addition to a trove of U.S. federal documents, Snowden's cache reportedly contains thousands of Australian, British and Canadian intelligence files that he had accessed via the exclusive "Five Eyes" network. In June 2013, the first of Snowden's documents were published simultaneously by The Washington Post and The Guardian, attracting considerable public attention. The disclosure continued throughout 2013, and a small portion of the estimated full cache of documents was later published by other media outlets worldwide, most notably The New York Times, the Canadian Broadcasting Corporation, the Australian Broadcasting Corporation, Der Spiegel (Germany), O Globo (Brazil), Le Monde (France), L'espresso (Italy), NRC Handelsblad, Dagbladet (Norway), El País (Spain), and Sveriges Television (Sweden).

Global mass surveillance can be defined as the mass surveillance of entire populations across national borders.

The Data Intercept Technology Unit is a unit of the Federal Bureau of Investigation (FBI) of the United States, which is responsible for intercepting telephone calls and e-mail messages of terrorists and foreign intelligence targets inside the US. It is not known when DITU was established, but the unit already existed in 1997.

This timeline of global surveillance disclosures from 2013 to the present day is a chronological list of the global surveillance disclosures that began in 2013. The disclosures have been largely instigated by revelations from the former American National Security Agency contractor Edward Snowden.

MYSTIC is a former secret program used since 2009 by the US National Security Agency (NSA) to collect the metadata as well as the content of phone calls from several countries. The program was first revealed in March 2014, based upon documents leaked by Edward Snowden.
Targeted surveillance is a form of surveillance, such as wiretapping, that is directed towards specific persons of interest, and is distinguishable from mass surveillance. Both untargeted and targeted surveillance is routinely accused of treating innocent people as suspects in ways that are unfair, of violating human rights, international treaties and conventions as well as national laws, and of failing to pursue security effectively.
References
- ↑ Ellen Nakashima; Joby Warrick (July 14, 2013). "For NSA chief, terrorist threat drives passion to 'collect it all,' observers say". The Washington Post. Retrieved July 15, 2013.
Collect it all, tag it, store it. . . . And whatever it is you want, you go searching for it.
- 1 2 3 4 Shane Harris, "@War, The Rise of the Military-Internet Complex", Houghton Mifflin Harcourt, New York, 2014, p. 33-38.
- 1 2 Wall Street Journal: Technology Emboldened the NSA, June 9, 2013.
- 1 2 Washington Post: For NSA chief, terrorist threat drives passion to ‘collect it all’, July 14, 2013
- ↑ Glenn Greenwald (July 15, 2013). "The crux of the NSA story in one phrase: 'collect it all': The actual story that matters is not hard to see: the NSA is attempting to collect, monitor and store all forms of human communication". The Guardian. Retrieved July 16, 2013.
- 1 2 Dana Priest, William M. Arkin, Top Secret America: The Rise of the New American Security State, Little, Brown and Company, 2011.
- ↑ Matthew M. Aid, Intel Wars: The Secret History of the Fight Against Terror, Bloomsbury, 2012.
- ↑ Washington Post: NSA growth fueled by need to target terrorists, July 22, 2013.
- ↑ Defensenews.com: Change agent Archived 2015-02-27 at archive.today , October 8, 2010.
