ECHELON, originally a secret government code name, is a surveillance program operated by the five signatory states to the UKUSA Security Agreement: Australia, Canada, New Zealand, the United Kingdom and the United States, also known as the Five Eyes.

The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The NSA has roughly 32,000 employees.

Robert Philip Hanssen was an American Federal Bureau of Investigation (FBI) agent who spied for Soviet and Russian intelligence services against the United States from 1979 to 2001. His espionage was described by the Department of Justice as "possibly the worst intelligence disaster in U.S. history".
James Bamford is an American author, journalist and documentary producer noted for his writing about United States intelligence agencies, especially the National Security Agency (NSA). The New York Times has called him "the nation's premier journalist on the subject of the National Security Agency" and The New Yorker named him "the NSA's chief chronicler."
Project SHAMROCK was the sister project to Project MINARET, an espionage exercise started in August 1945. Project MINARET involved the accumulation of all telegraphic data that entered or exited the United States. The Armed Forces Security Agency (AFSA) and its successor, the National Security Agency (NSA), were given direct access to daily microfilm copies of all incoming, outgoing, and transiting telegrams via the Western Union and its associates RCA and ITT. NSA did the operational interception, and, if there was information that would be of interest to other intelligence agencies, the material was passed to them. Intercepted messages were disseminated to the FBI, CIA, Secret Service, Bureau of Narcotics and Dangerous Drugs (BNDD), and the Department of Defense. No court authorized the operation and there were no warrants.

The Terrorist Surveillance Program was an electronic surveillance program implemented by the National Security Agency (NSA) of the United States in the wake of the September 11, 2001 attacks. It was part of the President's Surveillance Program, which was in turn conducted under the overall umbrella of the War on Terrorism. The NSA, a signals intelligence agency, implemented the program to intercept al Qaeda communications overseas where at least one party is not a U.S. person. In 2005, The New York Times disclosed that technical glitches resulted in some of the intercepts including communications which were "purely domestic" in nature, igniting the NSA warrantless surveillance controversy. Later works, such as James Bamford's The Shadow Factory, described how the nature of the domestic surveillance was much, much more widespread than initially disclosed. In a 2011 New Yorker article, former NSA employee Bill Binney said that his colleagues told him that the NSA had begun storing billing and phone records from "everyone in the country."
Spying on the United Nations refers to acts of espionage committed by states against the United Nations.

The Five Eyes (FVEY) is an Anglosphere intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States. These countries are parties to the multilateral UK-USA Agreement, a treaty for joint cooperation in signals intelligence. Informally, Five Eyes can also refer to the group of intelligence agencies of these countries.

FIRSTFRUITS is a United States counterintelligence program and database that tracks unauthorized disclosures of intelligence material in the news media. The project's goal is to reduce losses of collection capability due to journalists. The database was created by the US Central Intelligence Agency, but then transferred to US National Security Agency. The database has thousands of unofficial and negative articles and authors. Maintenance of the program was outsourced to third parties like Booz Allen Hamilton. The program became known through whistleblower Edward Snowden.
Vint Hill Farms Station (VHFS) was a United States Army and National Security Agency (NSA) signals intelligence and electronic warfare facility located in Fauquier County, Virginia, near Warrenton. VHFS was closed in 1997 and the land was sold off in 1999. Today the site hosts various engineering and technology companies, as well as two Federal Aviation Administration (FAA) air traffic control facilities.

The Beltsville Information Management Center (BIMC), formerly named the Beltsville Messaging Center (BMC) and the Beltsville Communications Center, is a United States Department of State facility located in Beltsville, Maryland, next door to the U.S. Special Collection Service (SCS). It serves as the primary relay facility for the Diplomatic Telecommunications Service and services the communications needs of various U.S. government programs and agencies, including the SCS.

Perry Fellwock is a former National Security Agency (NSA) analyst and whistleblower who revealed the existence of the NSA and its worldwide covert surveillance network in an interview, using the pseudonym Winslow Peck, with Ramparts in 1971. At the time that Fellwock blew the whistle on ECHELON, the NSA was a nearly unknown organization and among the most secretive of the US intelligence agencies. Fellwock revealed that it had a significantly larger budget than the Central Intelligence Agency (CIA). Fellwock was motivated by Daniel Ellsberg's release of the Pentagon Papers. Today, Fellwock has been acknowledged as the first NSA whistleblower.

The practice of mass surveillance in the United States dates back to wartime monitoring and censorship of international communications from, to, or which passed through the United States. After the First and Second World Wars, mass surveillance continued throughout the Cold War period, via programs such as the Black Chamber and Project SHAMROCK. The formation and growth of federal law-enforcement and intelligence agencies such as the FBI, CIA, and NSA institutionalized surveillance used to also silence political dissent, as evidenced by COINTELPRO projects which targeted various organizations and individuals. During the Civil Rights Movement era, many individuals put under surveillance orders were first labelled as integrationists, then deemed subversive, and sometimes suspected to be supportive of the communist model of the United States' rival at the time, the Soviet Union. Other targeted individuals and groups included Native American activists, African American and Chicano liberation movement activists, and anti-war protesters.

During the 2010s, international media news reports revealed new operational details about the Anglophone cryptographic agencies' global surveillance of both foreign and domestic nationals. The reports mostly relate to top secret documents leaked by ex-NSA contractor Edward Snowden. The documents consist of intelligence files relating to the U.S. and other Five Eyes countries. In June 2013, the first of Snowden's documents were published, with further selected documents released to various news outlets through the year.
This is a category of disclosures related to global surveillance.

Global mass surveillance can be defined as the mass surveillance of entire populations across national borders.
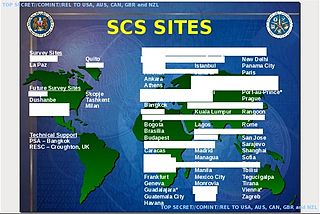
STATEROOM is the code name of a highly secretive signals intelligence collection program involving the interception of international radio, telecommunications and Internet traffic. It is operated out of the diplomatic missions of the signatories to the UKUSA Agreement and the members of the ECHELON network including Australia, New Zealand, United Kingdom, Canada and the United States.

This timeline of global surveillance disclosures from 2013 to the present day is a chronological list of the global surveillance disclosures that began in 2013. The disclosures have been largely instigated by revelations from the former American National Security Agency contractor Edward Snowden.

Operation Monopoly was a covert plan by the United States Federal Bureau of Investigation (FBI) to build a tunnel underneath the Soviet Embassy in Washington, D.C., to gather secret intelligence in effect from 1977 until its public discovery in 2001.