Related Research Articles

The Fourth Amendment to the United States Constitution is part of the Bill of Rights. It prohibits unreasonable searches and seizures and sets requirements for issuing warrants: warrants must be issued by a judge or magistrate, justified by probable cause, supported by oath or affirmation, and must particularly describe the place to be searched and the persons or things to be seized.
A search warrant is a court order that a magistrate or judge issues to authorize law enforcement officers to conduct a search of a person, location, or vehicle for evidence of a crime and to confiscate any evidence they find. In most countries, a search warrant cannot be issued in aid of civil process.

The Electronic Communications Privacy Act of 1986 (ECPA) was enacted by the United States Congress to extend restrictions on government wire taps of telephone calls to include transmissions of electronic data by computer, added new provisions prohibiting access to stored electronic communications, i.e., the Stored Communications Act, and added so-called pen trap provisions that permit the tracing of telephone communications . ECPA was an amendment to Title III of the Omnibus Crime Control and Safe Streets Act of 1968, which was primarily designed to prevent unauthorized government access to private electronic communications. The ECPA has been amended by the Communications Assistance for Law Enforcement Act (CALEA) of 1994, the USA PATRIOT Act (2001), the USA PATRIOT reauthorization acts (2006), and the FISA Amendments Act (2008)

Mobile phone tracking is a process for identifying the location of a mobile phone, whether stationary or moving. Localization may be affected by a number of technologies, such as the multilateration of radio signals between (several) cell towers of the network and the phone or by simply using GNSS. To locate a mobile phone using multilateration of mobile radio signals, the phone must emit at least the idle signal to contact nearby antenna towers and does not require an active call. The Global System for Mobile Communications (GSM) is based on the phone's signal strength to nearby antenna masts.
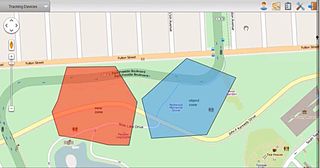
A geofence is a virtual perimeter for a real-world geographic area. A geofence can be dynamically generated or match a predefined set of boundaries.

United States v. Graham, 846 F. Supp. 2d 384, was a Maryland District Court case in which the Court held that historical cell site location data is not protected by the Fourth Amendment. Reacting to the precedent established by the recent Supreme Court case United States v. Jones in conjunction with the application of the third party doctrine, Judge Richard D. Bennett, found that "information voluntarily disclosed to a third party ceases to enjoy Fourth Amendment protection" because that information no longer belongs to the consumer, but rather to the telecommunications company that handles the transmissions records. The historical cell site location data is then not subject to the privacy protections afforded by the Fourth Amendment standard of probable cause, but rather to the Stored Communications Act, which governs the voluntary or compelled disclosure of stored electronic communications records.

United States v. Kincade, 379 F.3d 813, is a case of the United States Court of Appeals for the Ninth Circuit dealing with the constitutionality of collecting and retaining DNA from parolees.
Maryland v. King, 569 U.S. 435 (2013), was a decision of the United States Supreme Court which held that a cheek swab of an arrestee's DNA is comparable to fingerprinting and therefore, a legal police booking procedure that is reasonable under the Fourth Amendment.
The third-party doctrine is a United States legal doctrine that holds that people who voluntarily give information to third parties—such as banks, phone companies, internet service providers (ISPs), and e-mail servers—have "no reasonable expectation of privacy" in that information. A lack of privacy protection allows the United States government to obtain information from third parties without a legal warrant and without otherwise complying with the Fourth Amendment prohibition against search and seizure without probable cause and a judicial search warrant.

In re Application of the United States for Historical Cell Site Data, 724 F.3d 600, was a case in which the United States Court of Appeals for the Fifth Circuit held that the government can access cell site records without a warrant. Specifically, the court held that court orders under the Stored Communications Act compelling cell phone providers to disclose historical cell site information are not per se unconstitutional.
Mass surveillance in Australia takes place in several network media, including telephone, internet, and other communications networks, financial systems, vehicle and transit networks, international travel, utilities, and government schemes and services including those asking citizens to report on themselves or other citizens.
Microsoft Corp. v. United States, known on appeal to the U.S. Supreme Court as United States v. Microsoft Corp., 584 U.S. ___, 138 S. Ct. 1186 (2018), was a data privacy case involving the extraterritoriality of law enforcement seeking electronic data under the 1986 Stored Communications Act (SCA), Title II of the Electronic Communications Privacy Act of 1986 (ECPA), in light of modern computing and Internet technologies such as data centers and cloud storage.

Microsoft Corporation v. United States of America was a complaint for declaratory judgment action filed in the U.S. District Court in Seattle, Washington. At issue was the 1986 Electronic Communications Privacy Act. with Microsoft arguing that secrecy orders were preventing them from disclosing warrants to customers in violation of the company's and customers' rights. The case was started in April 2016 and although the government bid for dismissal of the suit, in February 2017 a federal judge set a trial date set for June 2018. Microsoft was supported in its lawsuit by companies such as Amazon, Apple, Google, Dropbox and Salesforce. The case was dropped by Microsoft in October 2017 after policy changes at the Department of Justice. Although no laws were changed, the new DOJ policy "changed data request rules on alerting Internet users about agencies accessing their information," and mandated defined periods of time for secrecy orders from the government. Although the change represented "most of what Microsoft was asking for," Microsoft did not rule out future litigation.
Carpenter v. United States, 585 U.S. ___, 138 S.Ct. 2206 (2018), is a landmark United States Supreme Court case concerning the privacy of historical cell site location information (CSLI). The Court held that the government violates the Fourth Amendment to the United States Constitution when it accesses historical CSLI records containing the physical locations of cellphones without a search warrant.
Investigative genetic genealogy, or forensic genetic genealogy, is the emerging practice of utilizing genetic information from direct-to-consumer companies for identifying suspects or victims in criminal cases. As of September 2021, the use of this practice has led to the discovery of over 150 suspects of murder and sexual assault. The investigative power of genetic genealogy revolves around the use of publicly accessible genealogy databases such as GEDMatch and FamilyTreeDNA. On GEDMatch, users are able to upload their genetic data from any direct-to-consumer company in an effort to identify relatives that have tested at companies other than their own.
Search engine privacy is a subset of internet privacy that deals with user data being collected by search engines. Both types of privacy fall under the umbrella of information privacy. Privacy concerns regarding search engines can take many forms, such as the ability for search engines to log individual search queries, browsing history, IP addresses, and cookies of users, and conducting user profiling in general. The collection of personally identifiable information (PII) of users by search engines is referred to as tracking.
Sensorvault is an internal Google database that contains records of users' historical geo-location data.
A geo-fence warrant is a search warrant issued by a court to allow law enforcement to search a database to find all active mobile devices within a particular geo-fence area. Courts have granted law enforcement geo-fence warrants to obtain information from databases such as Google's Sensorvault, which collects users' historical geolocation data. Geo-fence warrants are a part of a category of warrants known as reverse search warrants.
Digital Search and Seizure refers to the ability of the United States Government to obtain and read an individual's private digital correspondence and material under The Fourth Amendment of the United States Constitution.

Fog Reveal is a tracking tool that aggregates location data from mobile apps. It is a product of FOG Data Science.
References
- 1 2 3 4 5 "Geofence Warrants and the Fourth Amendment". Harvard Law Review . 134 (7). May 10, 2021.
- 1 2 3 4 5 Bhuiyan, Johana (September 16, 2021). "The new warrant: how US police mine Google for your location and search history". the Guardian. Retrieved October 17, 2021.
- 1 2 3 Fussell, Sidney (August 27, 2021). "An Explosion in Geofence Warrants Threatens Privacy Across the US". Wired . ISSN 1059-1028 . Retrieved October 17, 2021.
- ↑ "Geofence Warrants and the Fourth Amendment". Harvard Law Review . 134 (7). May 10, 2021.
- ↑ Rathi, Mohit (2021). "Rethinking Reverse Location Search Warrants". The Journal of Criminal Law and Criminology . 111 (3): 805–837. ISSN 0091-4169. JSTOR 48617799 – via JSTOR.
- ↑ O'Sullivan, Andrea (October 12, 2021). "The Government's Secret 'Google Search' Warrant Trap". Reason . Retrieved October 17, 2021.
- 1 2 Aldhous, Peter (February 3, 2020). "A Court Tried To Force Ancestry.com To Open Up Its DNA Database To Police. The Company Said No". BuzzFeed News . Retrieved October 17, 2021.
- ↑ Cahn, Albert Fox; Humell, Amanda (October 15, 2020). "'Keyword Warrants' Make Every Search A Risk". Verfassungsblog . doi:10.17176/20201015-233342-0. ISSN 2366-7044.
- 1 2 Lynch, Jennifer; Sobel, Nathaniel (August 31, 2021). "New Federal Court Rulings Find Geofence Warrants Unconstitutional". Electronic Frontier Foundation . Retrieved October 18, 2021.