
The Global System for Mobile Communications (GSM) is a standard developed by the European Telecommunications Standards Institute (ETSI) to describe the protocols for second-generation (2G) digital cellular networks used by mobile devices such as mobile phones and tablets. GSM is also a trade mark owned by the GSM Association. GSM may also refer to the Full Rate voice codec.
Location-based service (LBS) is a general term denoting software services which use geographic data and information to provide services or information to users. LBS can be used in a variety of contexts, such as health, indoor object search, entertainment, work, personal life, etc. Commonly used examples of location-based services include navigation software, social networking services, location-based advertising, and tracking systems. LBS can also include mobile commerce when taking the form of coupons or advertising directed at customers based on their current location. LBS also includes personalized weather services and even location-based games.
Enhanced 911 is a system used in North America to automatically provide the caller's location to 911 dispatchers. 911 is the universal emergency telephone number in the region. In the European Union, a similar system exists known as E112 and known as eCall when called by a vehicle.

Base station is – according to the International Telecommunication Union's (ITU) Radio Regulations (RR) – a "land station in the land mobile service."

A cell site, cell phone tower, cell base tower, or cellular base station is a cellular-enabled mobile device site where antennas and electronic communications equipment are placed to create a cell, or adjacent cells, in a cellular network. The raised structure typically supports antenna and one or more sets of transmitter/receivers transceivers, digital signal processors, control electronics, a GPS receiver for timing, primary and backup electrical power sources, and sheltering.

A satellite telephone, satellite phone or satphone is a type of mobile phone that connects to other phones or the telephone network by radio link through satellites orbiting the Earth instead of terrestrial cell sites, as cellphones do. Therefore, they can work in most geographic locations on the Earth's surface, as long as open sky and the line-of-sight between the phone and the satellite are provided. Depending on the architecture of a particular system, coverage may include the entire Earth or only specific regions. Satellite phones provide similar functionality to terrestrial mobile telephones; voice calling, text messaging, and low-bandwidth Internet access are supported through most systems. The advantage of a satellite phone is that it can be used in such regions where local terrestrial communication infrastructures, such as landline and cellular networks, are not available.

A cellular network or mobile network is a telecommunications network where the link to and from end nodes is wireless and the network is distributed over land areas called cells, each served by at least one fixed-location transceiver. These base stations provide the cell with the network coverage which can be used for transmission of voice, data, and other types of content. A cell typically uses a different set of frequencies from neighboring cells, to avoid interference and provide guaranteed service quality within each cell.

Mobile telephony is the provision of telephone services to mobile phones rather than fixed-location phones. Telephony is supposed to specifically point to a voice-only service or connection, though sometimes the line may blur.
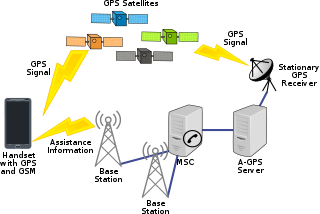
Assisted GNSS (A-GNSS) is a GNSS augmentation system that often significantly improves the startup performance—i.e., time-to-first-fix (TTFF)—of a global navigation satellite system (GNSS). A-GNSS works by providing the necessary data to the device via a radio network instead of the slow satellite link, essentially "warming up" the receiver for a fix. When applied to GPS, it is known as assisted GPS or augmented GPS. Other local names include A-GANSS for Galileo and A-Beidou for BeiDou.
Radiolocation, also known as radiolocating or radiopositioning, is the process of finding the location of something through the use of radio waves. It generally refers to passive uses, particularly radar—as well as detecting buried cables, water mains, and other public utilities. It is similar to radionavigation, but radiolocation usually refers to passively finding a distant object rather than actively one's own position. Both are types of radiodetermination. Radiolocation is also used in real-time locating systems (RTLS) for tracking valuable assets.
An international mobile subscriber identity-catcher, or IMSI-catcher, is a telephone eavesdropping device used for intercepting mobile phone traffic and tracking location data of mobile phone users. Essentially a "fake" mobile tower acting between the target mobile phone and the service provider's real towers, it is considered a man-in-the-middle (MITM) attack. The 3G wireless standard offers some risk mitigation due to mutual authentication required from both the handset and the network. However, sophisticated attacks may be able to downgrade 3G and LTE to non-LTE network services which do not require mutual authentication.
Thuraya is a United Arab Emirates-based regional mobile-satellite service (MSS) provider. The company operates two geosynchronous satellites and provides telecommunications coverage in more than 161 countries in Europe, the Middle East, North, Central and East Africa, Asia and Australia. Thuraya's L-band network delivers voice and data services.

A tracking system, also known as a locating system, is used for the observing of persons or objects on the move and supplying a timely ordered sequence of location data for further processing.
gpsOne is the brand name for a cellphone chipset manufactured by Qualcomm for mobile phone tracking. It uses A-GPS or Assisted-GPS to locate the phone more quickly, accurately and reliably than by GPS alone, especially in places with poor GPS reception.
Wi-Fi calling refers to mobile phone voice calls and data that are made over IP networks using Wi-Fi, instead of the cell towers provided by cellular networks. Using this feature, compatible handsets are able to route regular cellular calls through a wireless LAN (Wi-Fi) network with broadband Internet, while seamlessly change connections between the two where necessary. This feature makes use of the Generic Access Network (GAN) protocol, also known as Unlicensed Mobile Access (UMA).

A mobile phone signal is the signal strength received by a mobile phone from a cellular network. Depending on various factors, such as proximity to a tower, any obstructions such as buildings or trees, etc. this signal strength will vary. Most mobile devices use a set of bars of increasing height to display the approximate strength of this received signal to the mobile phone user. Traditionally five bars are used.

A mobile phone is a portable telephone that can make and receive calls over a radio frequency link while the user is moving within a telephone service area, as opposed to a fixed-location phone. The radio frequency link establishes a connection to the switching systems of a mobile phone operator, which provides access to the public switched telephone network (PSTN). Modern mobile telephone services use a cellular network architecture and therefore mobile telephones are called cellphones in North America. In addition to telephony, digital mobile phones support a variety of other services, such as text messaging, multimedia messaging, email, Internet access, short-range wireless communications, satellite access, business applications, video games and digital photography. Mobile phones offering only basic capabilities are known as feature phones; mobile phones which offer greatly advanced computing capabilities are referred to as smartphones.
A vehicle tracking system combines the use of automatic vehicle location in individual vehicles with software that collects these fleet data for a comprehensive picture of vehicle locations. Modern vehicle tracking systems commonly use GPS or GLONASS technology for locating the vehicle, but other types of automatic vehicle location technology can also be used. Vehicle information can be viewed on electronic maps via the Internet or specialized software. Urban public transit authorities are an increasingly common user of vehicle tracking systems, particularly in large cities.

The StingRay is an IMSI-catcher, a cellular phone surveillance device, manufactured by Harris Corporation. Initially developed for the military and intelligence community, the StingRay and similar Harris devices are in widespread use by local and state law enforcement agencies across Canada, the United States, and in the United Kingdom. Stingray has also become a generic name to describe these kinds of devices.
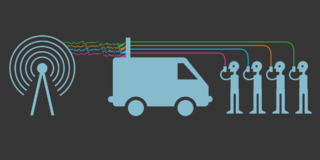
Cellphone surveillance may involve tracking, bugging, monitoring, eavesdropping, and recording conversations and text messages on mobile phones. It also encompasses the monitoring of people's movements, which can be tracked using mobile phone signals when phones are turned on.











