The Goodtimes virus, also styled as Good Times virus, was a computer virus hoax that spread during the early years of the Internet's popularity. Warnings about a computer virus named "Good Times" began being passed around among Internet users in 1994. The Goodtimes virus was supposedly transmitted via an email bearing the subject header "Good Times" or "Goodtimes", hence the virus's name, and the warning recommended deleting any such email unread. The virus described in the warnings did not exist, but the warnings themselves were, in effect, virus-like. In 1997 the Cult of the Dead Cow hacker collective announced that they had been responsible for the perpetration of the "Good Times" virus hoax as an exercise to "prove the gullibility of self-proclaimed 'experts' on the Internet".
A chain letter is a message that attempts to convince the recipient to make a number of copies and pass them on to a certain number of recipients. The "chain" is an exponentially growing pyramid that cannot be sustained indefinitely.

Antivirus software, also known as anti-malware, is a computer program used to prevent, detect, and remove malware.

Blaster was a computer worm that spread on computers running operating systems Windows XP and Windows 2000 during August 2003.
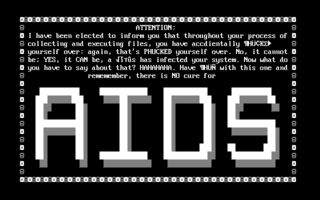
AIDS is a DOS computer virus which overwrites COM files.
Norton AntiVirus is an anti-virus or anti-malware software product founded by Peter Norton, developed and distributed by Symantec since 1990 as part of its Norton family of computer security products. It uses signatures and heuristics to identify viruses. Other features included in it are e-mail spam filtering and phishing protection.
Email fraud is intentional deception for either personal gain or to damage another individual using email as the vehicle. Almost as soon as email became widely used, it began to be used as a means to defraud people, just as telephony and paper mail were used by previous generations.
SULFNBK.EXE is an internal component of the Microsoft Windows operating system for restoring long file names.
Ransomware is a type of cryptovirological malware that permanently blocks access to the victim's personal data unless a ransom is paid. While some simple ransomware may lock the system without damaging any files, more advanced malware uses a technique called cryptoviral extortion. It encrypts the victim's files, making them inaccessible, and demands a ransom payment to decrypt them. In a properly implemented cryptoviral extortion attack, recovering the files without the decryption key is an intractable problem, and difficult-to-trace digital currencies such as paysafecard or Bitcoin and other cryptocurrencies are used for the ransoms, making tracing and prosecuting the perpetrators difficult.
Tuxissa is a fictional computer virus hoax made up by Humorix, a humor website on Linux.
Bad Times is a computer virus hoax sent out by e-mail. This "virus" does not actually exist, and the "warning" is meant to parody the alarmist message that spread the hoax of the Goodtimes virus hoax.
CTX is a computer virus created in Spain in 1999. CTX was initially discovered as part of the Cholera worm, with which the author intentionally infected with CTX. Although the Cholera worm had the capability to send itself via email, the CTX worm quickly surpassed it in prevalence. Cholera is now considered obsolete, while CTX remains in the field, albeit with only rare discoveries.
The Vundo Trojan is either a Trojan horse or a computer worm that is known to cause popups and advertising for rogue antispyware programs, and sporadically other misbehavior including performance degradation and denial of service with some websites including Google and Facebook. It also is used to deliver other malware to its host computers. Later versions include rootkits and ransomware.
W32.Navidad is a mass-mailing worm program or virus, discovered in December 2000 that ran on Windows 95, Windows 98, Windows NT, and Windows 2000 systems. It was designed to spread through email clients such as Microsoft Outlook while masquerading as an executable electronic Christmas card. Infected computers can be identified by blue eye icons which appear in the Windows system tray.

Security and Maintenance is a component of the Windows NT family of operating systems that monitors the security and maintenance status of the computer. Its monitoring criteria includes optimal operation of antivirus software, personal firewall, as well as the working status of Backup and Restore, Network Access Protection (NAP), User Account Control (UAC), Windows Error Reporting (WER), and Windows Update. It notifies the user of any problem with the monitored criteria, such as when an antivirus program is not up-to-date or is offline.

The Storm Worm is a phishing backdoor Trojan horse that affects computers using Microsoft operating systems, discovered on January 17, 2007. The worm is also known as:
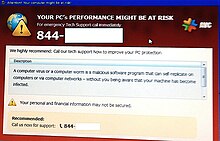
Koobface is a network worm that attacks Microsoft Windows, Mac OS X, and Linux platforms. This worm originally targeted users of networking websites like Facebook, Skype, Yahoo Messenger, and email websites such as GMail, Yahoo Mail, and AOL Mail. It also targets other networking websites, such as MySpace, Twitter, and it can infect other devices on the same local network. Technical support scammers also fraudulently claim to their intended victims that they have a Koobface infection on their computer by using fake popups and using built-in Windows programs.
The Pikachu virus, also referred to as Pokey or the Pokémon virus, was a computer worm believed to be the first malware geared at children, due to its incorporation of Pikachu, a creature from the Pokémon media franchise. It was considered similar to the Love Bug, albeit slower in its spread and less dangerous.
Zeus is a Trojan horse malware package that runs on versions of Microsoft Windows. It is often used to steal banking information by man-in-the-browser keystroke logging and form grabbing. Zeus is spread mainly through drive-by downloads and phishing schemes. First identified in July 2007 when it was used to steal information from the United States Department of Transportation, it became more widespread in March 2009. In June 2009 security company Prevx discovered that Zeus had compromised over 74,000 FTP accounts on websites of such companies as the Bank of America, NASA, Monster.com, ABC, Oracle, Play.com, Cisco, Amazon, and BusinessWeek. Similarly to Koobface, Zeus has also been used to trick victims of technical support scams into giving the scam artists money through pop-up messages that claim the user has a virus, when in reality they might have no viruses at all. The scammers may use programs such as Command prompt or Event viewer to make the user believe that their computer is infected.
The jdbgmgr.exe virus hoax involved an e-mail spam in 2002 that advised computer users to delete a file named jdbgmgr.exe because it was a computer virus. jdbgmgr.exe, which had a little teddy bear like icon, was actually a valid Microsoft Windows file, the Debugger Registrar for Java.