Related Research Articles
In computer science, self-modifying code is code that alters its own instructions while it is executing – usually to reduce the instruction path length and improve performance or simply to reduce otherwise repetitively similar code, thus simplifying maintenance. The term is usually only applied to code where the self-modification is intentional, not in situations where code accidentally modifies itself due to an error such as a buffer overflow.

A COM file is a type of simple executable file. On the Digital Equipment Corporation (DEC) VAX operating systems of the 1970s, .COM was used as a filename extension for text files containing commands to be issued to the operating system. With the introduction of Digital Research's CP/M, the type of files commonly associated with COM extension changed to that of executable files. This convention was later carried over to DOS. Even when complemented by the more general EXE file format for executables, the compact COM files remained viable and frequently used under DOS.
Abraxas, also known as Abraxas5, discovered in April 1993, is an encrypted, overwriting, file infecting computer virus which infects .COM and .EXE files, although it does not infect command.com. It does not become memory resident. Each time an infected file is executed, Abraxas infects the copy of dosshell.com located in the C:\DOS directory, as well as one EXE file in the current directory. Due to a bug in the virus, only the first EXE file in any directory is infected.
Acid is a computer virus which infects .COM and .EXE files including command.com. Each time an infected file is executed, Acid infects all of the .EXE files in the current directory. Later, if an infected file is executed, it infects the .COM files in the current directory. Programs infected with Acid will have had the first 792 bytes of the host program overwritten with Acid's own code. There will be no file length increase unless the original host program was smaller than 792 bytes, in which case it will become 792 bytes in length. The program's date and time in the DOS disk directory listing will not be altered.
Acme is a computer virus which infects MS-DOS EXE files. Each time an infected file is executed, Acme may infect an EXE in the current directory by creating a hidden 247 byte long read-only COM file with the same base name. Acme is a variant of Clonewar, a spawning virus. Acme is also perhaps a descendant of the small single-step infector Zeno, which is not to be confused with the Zeno programming language.
Ada is a computer virus that can affect any of the DOS operating systems. Ada was first discovered in 1991.
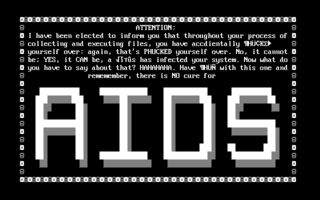
AIDS is a DOS computer virus which overwrites COM files.
Norton AntiVirus is an anti-virus or anti-malware software product founded by Peter Norton, developed and distributed by Symantec since 1990 as part of its Norton family of computer security products. It uses signatures and heuristics to identify viruses. Other features included in it are e-mail spam filtering and phishing protection.
Win32/Simile is a metamorphic computer virus written in assembly language for Microsoft Windows. The virus was released in its most recent version in early March 2002. It was written by the virus writer "Mental Driller". Some of his previous viruses, such as Win95/Drill, have proved very challenging to detect.
Jerusalem is a logic bomb DOS virus first detected at Hebrew University of Jerusalem, in October 1987. On infection, the Jerusalem virus becomes memory resident, and then infects every executable file run, except for COMMAND.COM. COM files grow by 1,813 bytes when infected by Jerusalem and are not re-infected. Executable files grow by 1,808 to 1,823 bytes each time they are infected, and are then re-infected each time the files are loaded until they are too large to load into memory. Some .EXE files are infected but do not grow because several overlays follow the genuine .EXE file in the same file. Sometimes .EXE files are incorrectly infected, causing the program to fail to run as soon as it is executed.
Scott's Valley [sic] is a computer virus, a member of the Slow virus family and distantly related to the Jerusalem virus family. It was discovered in September 1990 in Scotts Valley, California.
Alabama is a computer virus, discovered in October 1989 on the campus of the Hebrew University of Jerusalem.
Ontario is a family of computer viruses, named after its point of isolation, the Canadian province of Ontario. This family of computer virus consists of Ontario.1024, Ontario.512 and Ontario.2048. The first variant Ontario.512 was discovered in July 1990. Because Ontario.1024 was also discovered in Ontario, it is likely that both viruses originate from within the province. By the Ontario.2048 variant, the author had adopted "Ontario" as the family's name and even included the name "Ontario-3" in the virus code.
Bomber is a DOS polymorphic memory resident computer virus, known for its technique of "patchy infection". This method of infection is very similar to that which is utilised by the OneHalf computer virus.
CTX is a computer virus created in Spain in 1999. CTX was initially discovered as part of the Cholera worm, with which the author intentionally infected with CTX. Although the Cholera worm had the capability to send itself via email, the CTX worm quickly surpassed it in prevalence. Cholera is now considered obsolete, while CTX remains in the field, albeit with only rare discoveries.
The Vundo Trojan is either a Trojan horse or a computer worm that is known to cause popups and advertising for rogue antispyware programs, and sporadically other misbehavior including performance degradation and denial of service with some websites including Google and Facebook. It also is used to deliver other malware to its host computers. Later versions include rootkits and ransomware.
5lo is a computer virus that increases file size and does little more than replicate. Size: 1,032 bytes

A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses.
The Fun.Exe virus is of the w32.Assarm family of computer viruses. According to Symantec it registers itself as a Windows system process then periodically sends mail with spreading attachments as a response to any unopened emails in Outlook Express. This virus first appeared in early 2008 and is now recognized by most anti virus programs.
Sality is the classification for a family of malicious software (malware), which infects Microsoft Windows systems files. Sality was first discovered in 2003 and has advanced to become a dynamic, enduring and full-featured form of malicious code. Systems infected with Sality may communicate over a peer-to-peer (P2P) network to form a botnet to relay spam, proxying of communications, exfiltrating sensitive data, compromising web servers and/or coordinating distributed computing tasks to process intensive tasks. Since 2010, certain variants of Sality have also incorporated rootkit functions as part of an ongoing evolution of the malware family. Because of its continued development and capabilities, Sality is considered one of the most complex and formidable forms of malware to date.
References
- ↑ "ABC Virus". VSUM. Retrieved 12 February 2013.