
This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.
Acid is a computer virus which infects .COM and .EXE files including command.com. Each time an infected file is executed, Acid infects all of the .EXE files in the current directory. Later, if an infected file is executed, it infects the .COM files in the current directory. Programs infected with Acid will have had the first 792 bytes of the host program overwritten with Acid's own code. There will be no file length increase unless the original host program was smaller than 792 bytes, in which case it will become 792 bytes in length. The program's date and time in the DOS disk directory listing will not be altered.
Acme is a computer virus which infects MS-DOS EXE files. Each time an infected file is executed, Acme may infect an EXE in the current directory by creating a hidden 247 byte long read-only COM file with the same base name. Acme is a variant of Clonewar, a spawning virus. Acme is also perhaps a descendant of the small single-step infector Zeno, which is not to be confused with the Zeno programming language.

DOS Shell is a file manager that debuted in MS-DOS and PC DOS version 4.0, released in June 1988. It was no longer included in MS-DOS version 6, but remained part of the Supplemental Disk. The Supplemental Disk could be ordered or could be downloaded through Microsoft's FTP server. DOS Shell was retained in PC DOS until PC DOS 2000.
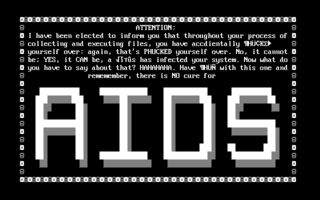
AIDS is a DOS computer virus which overwrites COM files.
PGPCoder or GPCode is a trojan that encrypts files on the infected computer and then asks for a ransom in order to release these files, a type of behavior dubbed ransomware or cryptovirology.
ABC, discovered in October 1992, is a memory-resident, file-infecting computer virus which infects EXE files and may alter both COM and EXE files. ABC activates on the 13th day of every month.
The Hare Virus was a destructive computer virus which infected DOS and Windows 95 machines in August 1996. It was also known as Hare.7610, Krsna and HD Euthanasia.
Jerusalem is a logic bomb DOS virus first detected at Hebrew University of Jerusalem, in October 1987. On infection, the Jerusalem virus becomes memory resident, and then infects every executable file run, except for COMMAND.COM. COM files grow by 1,813 bytes when infected by Jerusalem and are not re-infected. Executable files grow by 1,808 to 1,823 bytes each time they are infected, and are then re-infected each time the files are loaded until they are too large to load into memory. Some .EXE files are infected but do not grow because several overlays follow the genuine .EXE file in the same file. Sometimes .EXE files are incorrectly infected, causing the program to fail to run as soon as it is executed.
ARCV-n is a large family of viruses authored by the Association of Really Cruel Virsues (ARCV) group through October - November 1992. and polymorphed with the PS-MPC virus generation tool. A polymorphic virus mutates itself to avoid detection by traditional antivirus and antimalware software. ARCV-n viruses seem to infect COM and/or EXE files rapidly, but do not damage the compromised machine, instead displaying various text messages to the user. An infected file will have the ARCV-n virus appended to the end of it.
Alabama is a computer virus, discovered in October 1989 on the campus of the Hebrew University of Jerusalem.
Ontario is a family of computer viruses, named after its point of isolation, the Canadian province of Ontario. This family of computer virus consists of Ontario.1024, Ontario.512 and Ontario.2048. The first variant Ontario.512 was discovered in July 1990. Because Ontario.1024 was also discovered in Ontario, it is likely that both viruses originate from within the province. By the Ontario.2048 variant, the author had adopted "Ontario" as the family's name and even included the name "Ontario-3" in the virus code.
OneHalf is a DOS-based polymorphic computer virus discovered in October 1994. It is also known as Slovak Bomber, Freelove or Explosion-II. It infects the master boot record (MBR) of the hard disk, and any files with extensions .COM, .SCR and .EXE. However, it will not infect files that have SCAN, CLEAN, FINDVIRU, GUARD, NOD, VSAFE, MSAV or CHKDSK in the name.

Stoned is a boot sector computer virus created in 1987. It is one of the first viruses and is thought to have been written by a student in Wellington, New Zealand. By 1989 it had spread widely in New Zealand and Australia, and variants became very common worldwide in the early 1990s.
W32.Navidad is a mass-mailing worm program or virus, discovered in December 2000 that ran on Windows 95, Windows 98, Windows NT, and Windows 2000 systems. It was designed to spread through email clients such as Microsoft Outlook while masquerading as an executable electronic Christmas card. Infected computers can be identified by blue eye icons which appear in the Windows system tray.
Eliza is a computer virus discovered in December 1991. It infects COM files including COMMAND.COM. It has been reported that it is defective, yet destroys the .EXE files it creates. The .COM files are not deleted. To avoid detection, it does not alter the dates of files it infects, but increases their length by 1,193 or 1,194 bytes. It is also found in later versions of Windows.
5lo is a computer virus that increases file size and does little more than replicate. Size: 1,032 bytes

A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses.
Sality is the classification for a family of malicious software (malware), which infects Microsoft Windows systems files. Sality was first discovered in 2003 and has advanced to become a dynamic, enduring and full-featured form of malicious code. Systems infected with Sality may communicate over a peer-to-peer (P2P) network to form a botnet to relay spam, proxying of communications, exfiltrating sensitive data, compromising web servers and/or coordinating distributed computing tasks to process intensive tasks. Since 2010, certain variants of Sality have also incorporated rootkit functions as part of an ongoing evolution of the malware family. Because of its continued development and capabilities, Sality is considered one of the most complex and formidable forms of malware to date.




