
A password, sometimes called a passcode, is secret data, typically a string of characters, usually used to confirm a user's identity. Traditionally, passwords were expected to be memorized, but the large number of password-protected services that a typical individual accesses can make memorization of unique passwords for each service impractical. Using the terminology of the NIST Digital Identity Guidelines, the secret is held by a party called the claimant while the party verifying the identity of the claimant is called the verifier. When the claimant successfully demonstrates knowledge of the password to the verifier through an established authentication protocol, the verifier is able to infer the claimant's identity.

An intranet is a computer network for sharing information, easier communication, collaboration tools, operational systems, and other computing services within an organization, usually to the exclusion of access by outsiders. The term is used in contrast to public networks, such as the Internet, but uses the same technology based on the Internet protocol suite.
A web portal is a specially designed website that brings information from diverse sources, like emails, online forums and search engines, together in a uniform way. Usually, each information source gets its dedicated area on the page for displaying information ; often, the user can configure which ones to display. Variants of portals include mashups and intranet dashboards for executives and managers. The extent to which content is displayed in a "uniform way" may depend on the intended user and the intended purpose, as well as the diversity of the content. Very often design emphasis is on a certain "metaphor" for configuring and customizing the presentation of the content and the chosen implementation framework or code libraries. In addition, the role of the user in an organization may determine which content can be added to the portal or deleted from the portal configuration.
A management information system (MIS) is an information system used for decision-making, and for the coordination, control, analysis, and visualization of information in an organization. The study of the management information systems involves people, processes and technology in an organizational context. In other words, it serves, as the functions of controlling, planning, decision making in the management level setting.
In business, an intranet strategy is the use of an intranet and associated hardware and software to obtain one or more organizational objectives. An intranet is an access-restricted network used internally in an organization. An intranet uses the same concepts and technologies as the World Wide Web and Internet. This includes web browsers and servers running on the internet protocol suite and using Internet protocols such as FTP, TCP/IP, HTML, and Simple Mail Transfer Protocol (SMTP).

Single sign-on (SSO) is an authentication scheme that allows a user to log in with a single SSO ID to any of several related, yet independent, software systems.
Identity and access management or Identity management (IdM), is a framework of policies and technologies to ensure that the right users have the appropriate access to technology resources. IAM systems fall under the overarching umbrellas of IT security and data management. Identity and access management systems not only identify, authenticate, and control access for individuals who will be utilizing IT resources but also the hardware and applications employees need to access.
Business software is any software or set of computer programs used by business users to perform various business functions. These business applications are used to increase productivity, measure productivity, and perform other business functions accurately.
Enterprise content management (ECM) extends the concept of content management by adding a timeline for each content item and, possibly, enforcing processes for its creation, approval, and distribution. Systems using ECM generally provide a secure repository for managed items, analog or digital. They also include one methods for importing content to manage new items, and several presentation methods to make items available for use. Although ECM content may be protected by digital rights management (DRM), it is not required. ECM is distinguished from general content management by its cognizance of the processes and procedures of the enterprise for which it is created.
Self-service password reset (SSPR) is defined as any process or technology that allows users who have either forgotten their password or triggered an intruder lockout to authenticate with an alternate factor, and repair their own problem, without calling the help desk. It is a common feature in identity management software and often bundled in the same software package as a password synchronization capability.
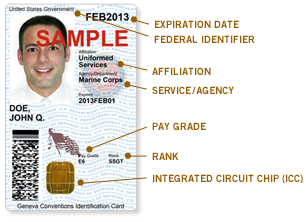
The common access card, also commonly referred to as the CAC, is the standard identification for active duty United States defense personnel. The card itself is a smart card about the size of a credit card. Defense personnel that use the CAC include the Selected Reserve and National Guard, United States Department of Defense (DoD) civilian employees, United States Coast Guard (USCG) civilian employees and eligible DoD and USCG contractor personnel. It is also the principal card used to enable physical access to buildings and controlled spaces, and it provides access to defense computer networks and systems. It also serves as an identification card under the Geneva Conventions. In combination with a personal identification number, a CAC satisfies the requirement for two-factor authentication: something the user knows combined with something the user has. The CAC also satisfies the requirements for digital signature and data encryption technologies: authentication, integrity and non-repudiation.
Glow is the Scottish Schools National Intranet. It is a major national ICT and telecommunications programme managed by Education Scotland. The project is funded by the Scottish Government and is a collaboration between local authorities, Education Scotland and RM Education. The online portal is powered by RM Unify, a service which provides account management and the Launchpad, an interface which allows users to access applications provided by the Scottish Government, local authorities, and individual schools.
An enterprise portal, also known as an enterprise information portal (EIP), is a framework for integrating information, people and processes across organizational boundaries in a manner similar to the more general web portals. Enterprise portals provide a secure unified access point, often in the form of a web-based user interface, and are designed to aggregate and personalize information through application-specific portlets.
Cyn.in is an open-source enterprise collaborative software built on top of Plone a content management system written in the Python programming language which is a layer above Zope. Cyn.in is developed by Cynapse a company founded by Apurva Roy Choudhury and Dhiraj Gupta which is based in India. Cyn.in enables its users to store, retrieve and organize files and rich content in a collaborative, multiuser environment.
Password fatigue is the feeling experienced by many people who are required to remember an excessive number of passwords as part of their daily routine, such as to log in to a computer at work, undo a bicycle lock or conduct banking from an automated teller machine. The concept is also known as password chaos, or more broadly as identity chaos.
ILIAS is an open-source web-based learning management system (LMS). It supports learning content management and tools for collaboration, communication, evaluation and assessment. The software is published under the GNU General Public License and can be run on any server that supports PHP and MySQL.

SharePoint is a collection of enterprise content management and knowledge management tools developed by Microsoft. Launched in 2001, it was initially bundled with Windows Server as Windows SharePoint Server, then renamed to Microsoft Office SharePoint Server, and then finally renamed to SharePoint. It is provided as part of Microsoft 365, but can also be configured to run as on-premises software.
Secure messaging is a server-based approach to protect sensitive data when sent beyond the corporate borders, and it provides compliance with industry regulations such as HIPAA, GLBA and SOX. Advantages over classical secure e-mail are that confidential and authenticated exchanges can be started immediately by any internet user worldwide since there is no requirement to install any software nor to obtain or to distribute cryptographic keys beforehand. Secure messages provide non-repudiation as the recipients are personally identified and transactions are logged by the secure email platform.
An intranet portal is the gateway that unifies access to enterprise information and applications on an intranet. It is a tool that helps a company manage its data, applications, and information more easily through personalized views. Some portal solutions are able to integrate legacy applications, objects from other portals, and handle thousands of user requests. In a corporate enterprise environment, it is also known as an enterprise portal.
milSuite, launched in October 2009 by the U.S. Army PEO EIS milTech Solution office, is a collection of online applications designed to enhance secure collaboration for the United States Department of Defense. With a served user base of 2.21 million, milSuite is one of the largest networks for personal information sharing across the joint-domain. milSuite comprises ten applications, with its five primary applications being milBook, milWiki, milTube, milUniversity and milSurvey.





