In cryptography, a cipher is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a procedure. An alternative, less common term is encipherment. To encipher or encode is to convert information into cipher or code. In common parlance, "cipher" is synonymous with "code", as they are both a set of steps that encrypt a message; however, the concepts are distinct in cryptography, especially classical cryptography.

Cryptanalysis refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown.

The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the German military. The Enigma machine was considered so secure that it was used to encipher the most top-secret messages.
In cryptography, a substitution cipher is a method of encrypting in which units of plaintext are replaced with the ciphertext, in a defined manner, with the help of a key; the "units" may be single letters, pairs of letters, triplets of letters, mixtures of the above, and so forth. The receiver deciphers the text by performing the inverse substitution process to extract the original message.

In cryptography, a Caesar cipher, also known as Caesar's cipher, the shift cipher, Caesar's code, or Caesar shift, is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a left shift of 3, D would be replaced by A, E would become B, and so on. The method is named after Julius Caesar, who used it in his private correspondence.

In the history of cryptography, the "System 97 Typewriter for European Characters" or "Type B Cipher Machine", codenamed Purple by the United States, was an encryption machine used by the Japanese Foreign Office from February 1939 to the end of World War II. The machine was an electromechanical device that used stepping-switches to encrypt the most sensitive diplomatic traffic. All messages were written in the 26-letter English alphabet, which was commonly used for telegraphy. Any Japanese text had to be transliterated or coded. The 26-letters were separated using a plug board into two groups, of six and twenty letters respectively. The letters in the sixes group were scrambled using a 6 × 25 substitution table, while letters in the twenties group were more thoroughly scrambled using three successive 20 × 25 substitution tables.

In the history of cryptography, the ECM Mark II was a cipher machine used by the United States for message encryption from World War II until the 1950s. The machine was also known as the SIGABA or Converter M-134 by the Army, or CSP-888/889 by the Navy, and a modified Navy version was termed the CSP-2900.

William Frederick Friedman was a US Army cryptographer who ran the research division of the Army's Signal Intelligence Service (SIS) in the 1930s, and parts of its follow-on services into the 1950s. In 1940, subordinates of his led by Frank Rowlett broke Japan's PURPLE cipher, thus disclosing Japanese diplomatic secrets before America's entrance into World War II.

In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher to decrypt it. This process prevents the loss of sensitive information via hacking. Decryption, the inverse of encryption, is the process of turning ciphertext into readable plaintext. Ciphertext is not to be confused with codetext because the latter is a result of a code, not a cipher.
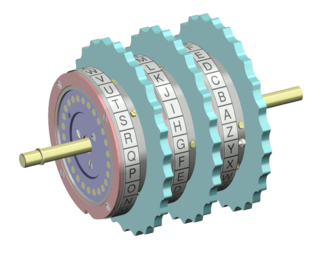
In cryptography, a rotor machine is an electro-mechanical stream cipher device used for encrypting and decrypting messages. Rotor machines were the cryptographic state-of-the-art for much of the 20th century; they were in widespread use in the 1920s–1970s. The most famous example is the German Enigma machine, the output of which was deciphered by the Allies during World War II, producing intelligence code-named Ultra.
Articles related to cryptography include:

Arthur Scherbius was a German electrical engineer who invented the mechanical cipher Enigma machine. He patented the invention and later sold the machine under the brand name Enigma.
Edward Hugh Hebern was an early inventor of rotor machines, devices for encryption.

The bombe was an electro-mechanical device used by British cryptologists to help decipher German Enigma-machine-encrypted secret messages during World War II. The US Navy and US Army later produced their own machines to the same functional specification, albeit engineered differently both from each other and from Polish and British bombes.

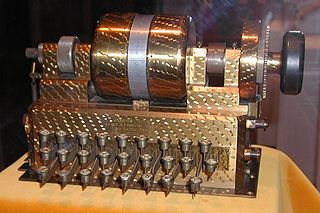
In cryptography, the M-209, designated CSP-1500 by the United States Navy is a portable, mechanical cipher machine used by the US military primarily in World War II, though it remained in active use through the Korean War. The M-209 was designed by Swedish cryptographer Boris Hagelin in response to a request for such a portable cipher machine, and was an improvement of an earlier machine, the C-36.

In the history of cryptography, the Kryha machine was a device for encryption and decryption, appearing in the early 1920s and used until the 1950s. The machine was the invention of Alexander von Kryha. During the Second World War, Kryha worked as an officer for the German Wehrmacht. There were several versions; the standard Kryha machine weighed around five kilograms, and was totally mechanical. A scaled down pocket version was introduced later on, termed the "Lilliput" model. There was also a more bulky electrical version.
Below is a timeline of notable events related to cryptography.

Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications.

In the history of cryptography, 91-shiki ōbun injiki or Angōki Taipu-A, codenamed Red by the United States, was a diplomatic cryptographic machine used by the Japanese Foreign Office before and during World War II. A relatively simple device, it was quickly broken by western cryptographers. The Red cipher was succeeded by the Type B "Purple" machine which used some of the same principles. Parallel usage of the two systems assisted in the breaking of the Purple system.
The following outline is provided as an overview of and topical guide to cryptography: