Related Research Articles
The ten Arabic numerals 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9 are the most commonly used symbols for writing numbers. The term often also implies a positional notation using the numerals, as well as the use of a decimal base, in particular when contrasted with other systems such as Roman numerals. However, the symbols are also used to write numbers in other bases such as octal, as well as for writing non-numerical information such as trademarks or license plate identifiers.

In cryptography, a cipher is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a procedure. An alternative, less common term is encipherment. To encipher or encode is to convert information into cipher or code. In common parlance, "cipher" is synonymous with "code", as they are both a set of steps that encrypt a message; however, the concepts are distinct in cryptography, especially classical cryptography.

Cryptanalysis refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown.

A numeral system is a writing system for expressing numbers; that is, a mathematical notation for representing numbers of a given set, using digits or other symbols in a consistent manner.
0 (zero) is a number representing an empty quantity. Adding 0 to any number leaves that number unchanged. In mathematical terminology, 0 is the additive identity of the integers, rational numbers, real numbers, and complex numbers, as well as other algebraic structures. Multiplying any number by 0 has the result 0, and consequently, division by zero has no meaning in arithmetic.

A stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream). In a stream cipher, each plaintext digit is encrypted one at a time with the corresponding digit of the keystream, to give a digit of the ciphertext stream. Since encryption of each digit is dependent on the current state of the cipher, it is also known as state cipher. In practice, a digit is typically a bit and the combining operation is an exclusive-or (XOR).
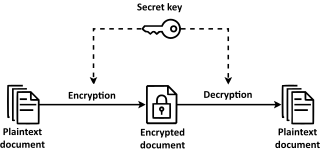
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. The keys may be identical, or there may be a simple transformation to go between the two keys. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. The requirement that both parties have access to the secret key is one of the main drawbacks of symmetric-key encryption, in comparison to public-key encryption. However, symmetric-key encryption algorithms are usually better for bulk encryption. With exception of the one-time pad they have a smaller key size, which means less storage space and faster transmission. Due to this, asymmetric-key encryption is often used to exchange the secret key for symmetric-key encryption.

In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher to decrypt it. This process prevents the loss of sensitive information via hacking. Decryption, the inverse of encryption, is the process of turning ciphertext into readable plaintext. Ciphertext is not to be confused with codetext because the latter is a result of a code, not a cipher.

The VIC cipher was a pencil and paper cipher used by the Soviet spy Reino Häyhänen, codenamed "VICTOR".
A straddling checkerboard is a device for converting an alphanumeric plaintext into digits whilst simultaneously achieving fractionation and data compression relative to other schemes using digits. It also is known as a monôme-binôme cipher.
In cryptography, confusion and diffusion are two properties of a secure cipher identified by Claude Shannon in his 1945 classified report A Mathematical Theory of Cryptography. These properties, when present, work together to thwart the application of statistics, and other methods of cryptanalysis.

The Polybius square, also known as the Polybius checkerboard, is a device invented by the ancient Greeks Cleoxenus and Democleitus, and made famous by the historian and scholar Polybius. The device is used for fractionating plaintext characters so that they can be represented by a smaller set of symbols, which is useful for telegraphy, steganography, and cryptography. The device was originally used for fire signalling, allowing for the coded transmission of any message, not just a finite number of predetermined options as was the convention before.
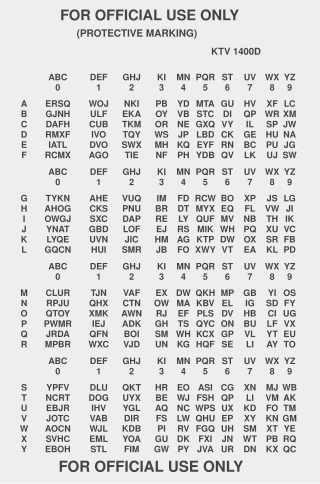
The DRYAD Numeral Cipher/Authentication System is a simple, paper cryptographic system employed by the U.S. military for authentication and for encryption of short, numerical messages. Each unit with a radio is given a set of matching DRYAD code sheets. A single sheet is valid for a limited time, called a cryptoperiod.
The Secure Communications Interoperability Protocol (SCIP) is a US standard for secure voice and data communication, for circuit-switched one-to-one connections, not packet-switched networks. SCIP derived from the US Government Future Narrowband Digital Terminal (FNBDT) project. SCIP supports a number of different modes, including national and multinational modes which employ different cryptography. Many nations and industries develop SCIP devices to support the multinational and national modes of SCIP.
A numeral is a character that denotes a number. The decimal number digits 0–9 are used widely in various writing systems throughout the world, however the graphemes representing the decimal digits differ widely. Therefore Unicode includes 22 different sets of graphemes for the decimal digits, and also various decimal points, thousands separators, negative signs, etc. Unicode also includes several non-decimal numerals such as Aegean numerals, Roman numerals, counting rod numerals, Mayan numerals, Cuneiform numerals and ancient Greek numerals. There is also a large number of typographical variations of the Western Arabic numerals provided for specialized mathematical use and for compatibility with earlier character sets, such as ² or ②, and composite characters such as ½.

Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications.

BATCO, short for Battle Code, is a hand-held, paper-based encryption system used at a low, front line level in the British Army. It was introduced along with the Clansman combat net radio in the early 1980s and was largely obsolete by 2010 due to the wide deployment of the secure Bowman radios. BATCO consists of a code, contained on a set of vocabulary cards, and cipher sheets for superencryption of the numeric code words. The cipher sheets, which are typically changed daily, also include an authentication table and a radio call sign protection system.
In cryptography, format-preserving encryption (FPE), refers to encrypting in such a way that the output is in the same format as the input. The meaning of "format" varies. Typically only finite sets of characters are used; numeric, alphabetic or alphanumeric. For example:
General der Nachrichtenaufklärung was the signals intelligence agency of the Heer, before and during World War II. It was the successor to the former cipher bureau known as Inspectorate 7/VI in operation between 1940 and 1942, when it was further reorganised into the Headquarters for Signal Intelligence between 1942 and 1944, until it was finally reorganised in October 1944 into the GdNA. The agency was also known at the OKH/Gend Na, GendNa or Inspectorate 7 or more commonly OKH/GdNA. Inspectorate 7/VI was also known as In 7 or In/7 or In 7/VI and also OKH/Chi.

The medieval Cistercian numerals, or "ciphers" in nineteenth-century parlance, were developed by the Cistercian monastic order in the early thirteenth century at about the time that Arabic numerals were introduced to northwestern Europe. They are more compact than Arabic or Roman numerals, with a single glyph able to indicate any integer from 1 to 9,999.
References
- Michael van der Meulen: Reihenschieber, in Cryptologia, Vol. 20(2), 1996, pp 141–154.