Related Research Articles

In cryptography, a cipher is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a procedure. An alternative, less common term is encipherment. To encipher or encode is to convert information into cipher or code. In common parlance, "cipher" is synonymous with "code", as they are both a set of steps that encrypt a message; however, the concepts are distinct in cryptography, especially classical cryptography.

Cryptanalysis refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown.

In cryptography, encryption is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor.

The Kama Sutra is an ancient Indian Hindu Sanskrit text on sexuality, eroticism and emotional fulfillment. Attributed to Vātsyāyana, the Kamasutra is neither exclusively nor predominantly a sex manual on sex positions, but rather a guide on the art of living well, the nature of love, finding partners, maintaining sex life, and other aspects pertaining to pleasure-oriented faculties. It is a sutra-genre text with terse aphoristic verses that have survived into the modern era with different bhāṣyas (commentaries). The text is a mix of prose and anustubh-meter poetry verses.
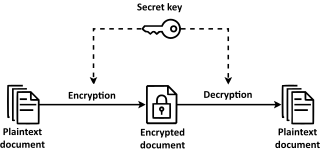
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. The keys may be identical, or there may be a simple transformation to go between the two keys. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. The requirement that both parties have access to the secret key is one of the main drawbacks of symmetric-key encryption, in comparison to public-key encryption. However, symmetric-key encryption algorithms are usually better for bulk encryption. With exception of the one-time pad they have a smaller key size, which means less storage space and faster transmission. Due to this, asymmetric-key encryption is often used to exchange the secret key for symmetric-key encryption.
A chosen-plaintext attack (CPA) is an attack model for cryptanalysis which presumes that the attacker can obtain the ciphertexts for arbitrary plaintexts. The goal of the attack is to gain information that reduces the security of the encryption scheme.

The Playfair cipher or Playfair square or Wheatstone–Playfair cipher is a manual symmetric encryption technique and was the first literal digram substitution cipher. The scheme was invented in 1854 by Charles Wheatstone, but bears the name of Lord Playfair for promoting its use.

In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher to decrypt it. This process prevents the loss of sensitive information via hacking. Decryption, the inverse of encryption, is the process of turning ciphertext into readable plaintext. Ciphertext is not to be confused with codetext because the latter is a result of a code, not a cipher.
A null cipher, also known as concealment cipher, is an ancient form of encryption where the plaintext is mixed with a large amount of non-cipher material. Today it is regarded as a simple form of steganography, which can be used to hide ciphertext.
The vulnerability of Japanese naval codes and ciphers was crucial to the conduct of World War II, and had an important influence on foreign relations between Japan and the west in the years leading up to the war as well. Every Japanese code was eventually broken, and the intelligence gathered made possible such operations as the victorious American ambush of the Japanese Navy at Midway in 1942 and the shooting down of Japanese admiral Isoroku Yamamoto a year later in Operation Vengeance.

Books on cryptography have been published sporadically and with variable quality for a long time. This is despite the paradox that secrecy is of the essence in sending confidential messages – see Kerckhoffs' principle.
Cryptography, the use of codes and ciphers to protect secrets, began thousands of years ago. Until recent decades, it has been the story of what might be called classical cryptography — that is, of methods of encryption that use pen and paper, or perhaps simple mechanical aids. In the early 20th century, the invention of complex mechanical and electromechanical machines, such as the Enigma rotor machine, provided more sophisticated and efficient means of encryption; and the subsequent introduction of electronics and computing has allowed elaborate schemes of still greater complexity, most of which are entirely unsuited to pen and paper.

David Kahn was an American historian, journalist, and writer. He wrote extensively on the history of cryptography and military intelligence.
In cryptography, a classical cipher is a type of cipher that was used historically but for the most part, has fallen into disuse. In contrast to modern cryptographic algorithms, most classical ciphers can be practically computed and solved by hand. However, they are also usually very simple to break with modern technology. The term includes the simple systems used since Greek and Roman times, the elaborate Renaissance ciphers, World War II cryptography such as the Enigma machine and beyond.

In cryptology, a code is a method used to encrypt a message that operates at the level of meaning; that is, words or phrases are converted into something else. A code might transform "change" into "CVGDK" or "cocktail lounge". The U.S. National Security Agency defined a code as "A substitution cryptosystem in which the plaintext elements are primarily words, phrases, or sentences, and the code equivalents typically consist of letters or digits in otherwise meaningless combinations of identical length." A codebook is needed to encrypt, and decrypt the phrases or words.
In the history of cryptography, a grille cipher was a technique for encrypting a plaintext by writing it onto a sheet of paper through a pierced sheet. The earliest known description is due to Jacopo Silvestri in 1526. His proposal was for a rectangular stencil allowing single letters, syllables, or words to be written, then later read, through its various apertures. The written fragments of the plaintext could be further disguised by filling the gaps between the fragments with anodyne words or letters. This variant is also an example of steganography, as are many of the grille ciphers.
With the rise of easily-intercepted wireless telegraphy, codes and ciphers were used extensively in World War I. The decoding by British Naval intelligence of the Zimmermann telegram helped bring the United States into the war.

Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications.
Mūlabhadra (മൂലഭദ്ര) aka Mūlabhadri was a secret method of communication employed by the royal spies of the erstwhile Travancore Kingdom during the medieval period. The scheme was also colloquially referred to as Mūlapatra. It was essentially a cryptographic scheme involving a partial transposition of the letters of the Malayalam alphabet. The scheme had been extensively used by King Marthanda Varma (1706–1758) of Travancore Kingdom and his spies both for oral and written communication of messages. It was a fixed one-time unchangeable code in as much as it did not employ any key in its implementation in contrast to modern methods of substitution ciphers involving the utilisation of a key for generating a system of codes.

Gaṇikā or ganika were female courtesans in early Ancient India, with their earliest reference in the Vedic period. Mentioned in the Kamasutra, Gaṇikās were also dubbed as "courtesans de luxe," this was how Indians in early Ancient India, separated them from veshyas, who were also courtesans.Moti Chandra, an Indian scholar who suggested that "In the hierarchy of courtesans, the kumbhadasi occupied the lowest place and the Gaṇikās the highest." This suggests that Gaṇikās, were not merely prostitutes or normal courtesans, but they were considered "premium courtesans." It is similar to how there is a difference between an Oiran and a Geisha.
References
- 1 2 The Kama Sutra of Vatsyayana (Translated From The Sanscrit In Seven Parts With Preface, Introduction and Concluding Remarks). Translated by Burton, Richard; Indrajit, Bhagavanlal; Bhide, Shivaram Parashuram. The Project Gutenberg. January 18, 2009. Retrieved 3 December 2015.
- ↑ David Kahn (December 1996). The Codebreakers. Simon and Schuster. p. 74. ISBN 9781439103555 . Retrieved 25 November 2015.
- ↑ Simon Singh. "The Black Chamber" . Retrieved 4 December 2015.
- 1 2 3 4 Anil Baran Ganguly (1979). Fine Arts of Ancient India. Abhinav Publications. pp. 1678–170. Retrieved 4 December 2015.
- ↑ Friedrich L Brauer (2007). Decrypted Secrets: Methods and Maxims of Cryptology. Springer. p. 47. ISBN 978-3-540-24502-5.
- ↑ Anil Baran Ganguly (1979). Fine Arts in Ancient India. Abhinav Publications. p. 169. Retrieved 26 November 2015.