PHP-Nuke is a web-based automated news publishing and content management system based on PHP and MySQL originally written by Francisco Burzi. The system is controlled using a web-based user interface. PHP-Nuke was originally a fork of the Thatware news portal system by David Norman.
Deep packet inspection (DPI) is a type of data processing that inspects in detail the data being sent over a computer network, and may take actions such as alerting, blocking, re-routing, or logging it accordingly. Deep packet inspection is often used to baseline application behavior, analyze network usage, troubleshoot network performance, ensure that data is in the correct format, check for malicious code, eavesdropping, and internet censorship, among other purposes. There are multiple headers for IP packets; network equipment only needs to use the first of these for normal operation, but use of the second header is normally considered to be shallow packet inspection despite this definition.

An application firewall is a form of firewall that controls input/output or system calls of an application or service. It operates by monitoring and blocking communications based on a configured policy, generally with predefined rule sets to choose from. The application firewall can control communications up to the application layer of the OSI model, which is the highest operating layer, and where it gets its name. The two primary categories of application firewalls are network-based and host-based.
Norton AntiVirus is an anti-virus or anti-malware software product founded by Peter Norton, developed and distributed by Gen Digital since 1990 as part of its Norton family of computer security products. It uses signatures and heuristics to identify viruses. Other features included in it are e-mail spam filtering and phishing protection.
Norton Internet Security, developed by Symantec Corporation, is a discontinued computer program that provides malware protection and removal during a subscription period. It uses signatures and heuristics to identify viruses. Other features include a personal firewall, email spam filtering, and phishing protection. With the release of the 2015 line in summer 2014, Symantec officially retired Norton Internet Security after 14 years as the chief Norton product. It was superseded by Norton Security, a rechristened adaptation of the Norton 360 security suite.
The following tables compare general and technical information for a number of File Transfer Protocol (FTP) clients. Unless otherwise specified in footnotes, comparisons are based on the stable versions without any add-ons, extensions, or external programs.
Take Command Console (TCC), formerly known as 4DOS for Windows NT (4NT), is a command-line interpreter by JP Software, designed as a substitute for the default command interpreter in Microsoft Windows, CMD.EXE.
Criticism of Windows XP deals with issues with security, performance and the presence of product activation errors that are specific to the Microsoft operating system Windows XP.
Axialis IconWorkshop is an icon editor developed by Axialis Software. IconWorkshop can create icons for Windows (.ico), Macintosh (.icns) and UNIX-like systems (.png). IconWorkshop includes a library of objects that can be put together to create many different styles of icons. The utility supports plugins and allows importing graphics directly from Photoshop and Illustrator.
Defensive computing is a form of practice for computer users to help reduce the risk of computing problems, by avoiding dangerous computing practices. The primary goal of this method of computing is to be able to anticipate and prepare for potentially problematic situations prior to their occurrence, despite any adverse conditions of a computer system or any mistakes made by other users. This can be achieved through adherence to a variety of general guidelines, as well as the practice of specific computing techniques.
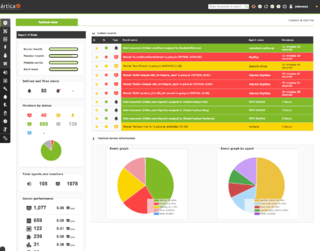
Pandora FMS is software for monitoring computer networks. Pandora FMS allows the visual monitoring of the status and performance of several parameters from different operating systems, servers, applications and hardware systems such as firewalls, proxies, databases, web servers or routers.

Software remastering is software development that recreates system software and applications while incorporating customizations, with the intent that it is copied and run elsewhere for "off-label" usage. The term comes from remastering in media production, where it is similarly distinguished from mere copying.
Opengear is a global computer network technology company headquartered in Edison, New Jersey, U.S., with R&D operations in Brisbane, Qld, Australia and production in Sandy, UT.

Microsoft Security Essentials (MSE) is an antivirus software (AV) product that provides protection against different types of malicious software, such as computer viruses, spyware, rootkits, and Trojan horses. Prior to version 4.5, MSE ran on Windows XP, Windows Vista, and Windows 7, but not on Windows 8 and later versions, which have built-in AV components known as Windows Defender. MSE 4.5 and later versions do not run on Windows XP. The license agreement allows home users and small businesses to install and use the product free of charge. It replaces Windows Live OneCare, a discontinued commercial subscription-based AV service, and the free Windows Defender, which only protected users from spyware until Windows 8.

TeeChart is a charting library for programmers, developed and managed by Steema Software of Girona, Catalonia, Spain. It is available as commercial and non-commercial software. TeeChart has been included in most Delphi and C++Builder products since 1997, and TeeChart Standard currently is part of Embarcadero RAD Studio 11 Alexandria. TeeChart Pro version is a commercial product that offers shareware releases for all of its formats, TeeChart. Lite for .NET is a free charting component for the Microsoft Visual Studio .NET community and TeeChart for PHP is an open-source library for PHP environments. The TeeChart Charting Library offers charts, maps and gauges in versions for Delphi VCL/FMX, ActiveX, C# for Microsoft Visual Studio .NET, Java and PHP. Full source code has always been available for all versions except the ActiveX version. TeeChart's user interface is translated into 38 languages.
LiveCode is a cross-platform rapid application development runtime system inspired by HyperCard. It features the LiveCode Script programming language which belongs to the family of xTalk scripting languages like HyperCard's HyperTalk.
Actian Zen is an ACID-compliant database management system (DBMS) developed by Pervasive Software. It is optimized for embedding in applications and used in several different types of packaged software applications offered by independent software vendors (ISVs) and original equipment manufacturers (OEMs). It is available for software as a service (SaaS) deployment due to a file-based architecture enabling partitioning of data for multitenancy needs.

A web shell is a shell-like interface that enables a web server to be remotely accessed, often for the purposes of cyberattacks. A web shell is unique in that a web browser is used to interact with it.

Remote Utilities is a remote desktop software that allows a user to remotely control another computer through a proprietary protocol and see the remote computer's desktop, operate its keyboard and mouse.






