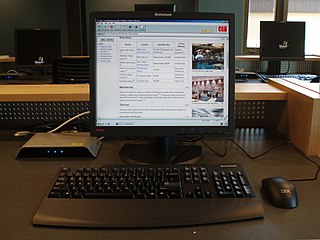
A thin client is a lightweight computer that has been optimized for establishing a remote connection with a server-based computing environment. The server does most of the work, which can include launching software programs, performing calculations, and storing data. This contrasts with a fat client or a conventional personal computer; the former is also intended for working in a client–server model but has significant local processing power, while the latter aims to perform its function mostly locally.

A weapon, arm or armament is any implement or device that can be used with intent to inflict damage or harm. Weapons are used to increase the efficacy and efficiency of activities such as hunting, crime, law enforcement, self-defense, and warfare. In broader context, weapons may be construed to include anything used to gain a tactical, strategic, material or mental advantage over an adversary or enemy target.

Chemical warfare (CW) involves using the toxic properties of chemical substances as weapons. This type of warfare is distinct from nuclear warfare and biological warfare, which together make up NBC, the military acronym for nuclear, biological, and chemical, all of which are considered "weapons of mass destruction" (WMDs). None of these fall under the term conventional weapons which are primarily effective due to their destructive potential. In theory, with proper protective equipment, training, and decontamination measures, the primary effects of chemical weapons can be overcome. In practice, they continue to cause much suffering, as most victims are defenseless . Many nations possess vast stockpiles of weaponized agents in preparation for wartime use. The threat and the perceived threat have become strategic tools in planning both measures and counter-measures.
A web portal is a specially designed website that brings information from diverse sources, like emails, online forums and search engines, together in a uniform way. Usually, each information source gets its dedicated area on the page for displaying information ; often, the user can configure which ones to display. Variants of portals include mashups and intranet "dashboards" for executives and managers. The extent to which content is displayed in a "uniform way" may depend on the intended user and the intended purpose, as well as the diversity of the content. Very often design emphasis is on a certain "metaphor" for configuring and customizing the presentation of the content and the chosen implementation framework or code libraries. In addition, the role of the user in an organization may determine which content can be added to the portal or deleted from the portal configuration.
Supervisory control and data acquisition (SCADA) is a control system architecture comprising computers, networked data communications and graphical user interfaces (GUI) for high-level process supervisory management, while also comprising other peripheral devices like programmable logic controllers (PLC) and discrete proportional-integral-derivative (PID) controllers to interface with process plant or machinery. The use of SCADA has been considered also for management and operations of project-driven-process in construction.
In computer security, a vulnerability is a weakness which can be exploited by a threat actor, such as an attacker, to perform unauthorized actions within a computer system. To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. In this frame, vulnerability is also known as the attack surface.

Internet privacy involves the right or mandate of personal privacy concerning the storing, repurposing, provision to third parties, and displaying of information pertaining to oneself via the internet. Internet privacy is a subset of data privacy. Privacy concerns have been articulated from the beginnings of large-scale computer sharing.
An Internet bot, also known as a web robot, robot or simply bot, is a software application that runs automated tasks (scripts) over the Internet. Typically, bots perform tasks that are both simple and structurally repetitive, at a much higher rate than would be possible for a human alone. The largest use of bots is in web spidering, in which an automated script fetches, analyzes and files information from web servers at many times the speed of a human. More than half of all web traffic is made up of bots.
Network-centric warfare, also called network-centric operations or net-centric warfare, is a military doctrine or theory of war pioneered by the United States Department of Defense in the 1990s.
Database security concerns the use of a broad range of information security controls to protect databases against compromises of their confidentiality, integrity and availability. It involves various types or categories of controls, such as technical, procedural/administrative and physical.

Mobile social networking (MSN) is social networking where individuals with similar interests converse and connect with one another through their mobile phone and/or tablet. Much like web-based social networking, mobile social networking occurs in virtual communities.

Intel Active Management Technology (AMT) is hardware and firmware for remote out-of-band management of select business computers, running on the Intel Management Engine, a separate microprocessor not exposed to the user, in order to monitor, maintain, update, upgrade, and repair them. Out-of-band (OOB) or hardware-based management is different from software-based management and software management agents.
Consumerization is the reorientation of product and service designs to focus on the end user as an individual consumer, in contrast with an earlier era of only organization-oriented offerings. Technologies whose first commercialization was at the inter-organization level thus have potential for later consumerization. The emergence of the individual consumer as the primary driver of product and service design is most commonly associated with the IT industry, as large business and government organizations dominated the early decades of computer usage and development. Thus the microcomputer revolution, in which electronic computing moved from exclusively enterprise and government use to include personal computing, is a cardinal example of consumerization. But many technology-based products, such as calculators and mobile phones, have also had their origins in business markets, and only over time did they become dominated by high-volume consumer usage, as these products commoditized and prices fell. An example of enterprise software that became consumer software is optical character recognition software, which originated with banks and postal systems but eventually became personal productivity software.
Shadow IT, also known as Stealth IT or Client IT or Fake IT, are Information technology (IT) systems built and used within organizations without explicit organizational approval, for example, systems specified and deployed by departments other than the IT department.
Dynamic Infrastructure is an information technology concept related to the design of data centers, whereby the underlying hardware and software can respond dynamically and more efficiently to changing levels of demand. In other words, data center assets such as storage and processing power can be provisioned to meet surges in user's needs. The concept has also been referred to as Infrastructure 2.0 and Next Generation Data Center.
Koobface is a network worm that attacks Microsoft Windows, Mac OS X, and Linux platforms. This worm originally targeted users of networking websites like Facebook, Skype, Yahoo Messenger, and email websites such as GMail, Yahoo Mail, and AOL Mail. It also targets other networking websites, such as MySpace, Twitter, and it can infect other devices on the same local network. Technical support scammers also fraudulently claim to their intended victims that they have a Koobface infection on their computer by using fake popups and using built-in Windows programs.
In computer security, a threat is a possible danger that might exploit a vulnerability to breach security and therefore cause possible harm.
Data monetization, a form of monetization, may refer to the act of generating measurable economic benefits from available data sources (analytics). Less commonly, it may also refer to the act of monetizing data services. In the case of analytics, typically, these benefits accrue as revenue or expense savings, but may also include market share or corporate market value gains. Data monetization leverages data generated through business operations, available exogenous data or content, as well as data associated with individual actors such as that collected via electronic devices and sensors participating in the internet of things. For example, the ubiquity of the internet of things is generating location data and other data from sensors and mobile devices at an ever-increasing rate. When this data is collated against traditional databases, the value and utility of both sources of data increases, leading to tremendous potential to mine data for social good, research and discovery, and achievement of business objectives. Closely associated with data monetization are the emerging data as a service models for transactions involving data by the data item.
In computers and computer networks an attack is any attempt to expose, alter, disable, destroy, steal or gain unauthorized access to or make unauthorized use of an asset. A cyberattack is any type of offensive maneuver that targets computer information systems, infrastructures, computer networks, or personal computer devices. An attacker is a person or process that attempts to access data, functions or other restricted areas of the system without authorization, potentially with malicious intent. Depending on context, cyberattacks can be part of cyberwarfare or cyberterrorism. A cyberattack can be employed by sovereign states, individuals, groups, society or organizations, and it may originate from an anonymous source.
The Internet of Military Things (IoMT) is a class of Internet of things for combat operations and warfare. It is a complex network of interconnected entities, or "things", in the military domain that continually communicate with each other to coordinate, learn, and interact with the physical environment to accomplish a broad range of activities in a more efficient and informed manner. The concept of IoMT is largely driven by the idea that future military battles will be dominated by machine intelligence and cyber warfare and will likely take place in urban environments. By creating a miniature ecosystem of smart technology capable of distilling sensory information and autonomously governing multiple tasks at once, the IoMT is conceptually designed to offload much of the physical and mental burden that warfighters encounter in a combat setting.





