Technique
Terms







- Working path - is the chosen route from source to destination.
- Segment protection path - is the working path where the broken segment is using the protected path.
- Primary segment - is a segment of the working path.
- Protected segment - is the backup path of one segment.
- End-to-end protection - is the protection of one segment where is source and destination are also the end points of the backup protection.
Examples
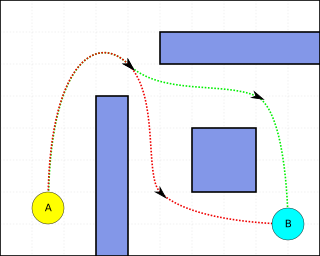
In "Working path" animation on the right it can be seen that for a chosen route the primary path becomes the working path. This example illustrates that the source (node A) is routed to B,then C,D,E, and lastly the destination (node F). We can see that segment protection has been implemented. Segment consists of nodes A, B, C, and D while segment consists of nodes C, D, E, and F. Lets assume that link B-C failed. Nodes B and C know that the link between them is down so they signal to their neighboring nodes that a link is down and to move to a backup path. Node A sends its traffic over to node D directly. Node D then sends the traffic over its route to E then finally destination F.
Note: in this case the segment protection path for segment does not contain any intermediate nodes; this is usually not the case, but the example would follow respectively.
Overlapping vs. non-overlapping
Overlapping and non-overlapping segment protection have one main difference but provide different protections at different costs. [2] The diagrams to the right, "overlapping protection" and "non-overlapping protection" illustrate the difference between the two. The overlapping scheme makes sure that there is at least one link that is protected by two segments, while the non-overlapping scheme begins a segment protection at the same node as the previous ended. Node protection is the main advantage of the overlapping scheme over the non-overlapping scheme.
Node protection that is provided allows a path to be provisioned if a node goes offline. In the diagram, "Overlapped link", we can see that link C-D has protection from segment and segment . This type of protection allows node C to fail and for the backup of segment to be used. The path would then be node A to D to E to F. This would work the same if node D failed. The corresponding path to that failure would be node A to B to C to F.
Non-overlapping segment protection does not provide node protection at every node. This scheme is only able to recover from a node failure that is not at the segment end node. In the diagram, "Non-overlapping protection", if node D fails a path cannot be provisioned from node A, the source, to node F, the Destination. Non-overlapping segment protection is a more cost efficient solution because only the end node of every segment requires to have extra ports. In the long term it is more cost efficient to implement overlapping segment protection because the a provisioned circuit's availability would be much higher.
Backup variations
Dedicated segment protection and shared segment protection are both available for use. Shared segment protection allows a more efficient network to be deployed. Both of these schemes can be implemented on an overlapping and a non-overlapping network topology. The "working path" diagram illustrates the dedicated-overlapping segment protection.
"Shared segment protection", on the right, illustrated a shared-non-overlapping segment protection. Working paths, A and B, both have segment protection. The first segment protection path consists of, node A to B to C to D and the second consists of, node D to E to F. In this example we can see that if part of working path A, node D to F, would fail that node D would use its shred segment protection for that segment. The new path for working path A would be, A to D to E to F. Of course, if a second failure occurred on the same segment before the first failure is fixed a recovery would not be possible. [2]
Shared segment protection provides a higher efficiency. Although the networks provided here as examples are simple the benefits of sharing are noticeable. In the previous example we can see that a new backup segment protection is not necessary for each working path. When this scheme is scaled to a large network a substantial cost improvement can be seen.