
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The existence of the NSA was not revealed until 1975. The NSA has roughly 32,000 employees.

Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. It can also include simple technical methods, such as human intelligence gathering and postal interception.
Cryptome was an online library and 501(c)(3) private foundation created in 1996 by John Young and Deborah Natsios and closed in 2023. The site collected information about freedom of expression, privacy, cryptography, dual-use technologies, national security, intelligence, and government secrecy.

Strategic Forecasting Inc., commonly known as Stratfor, is an American strategic intelligence publishing company founded in 1996. Stratfor's business model is to provide individual and enterprise subscriptions to Stratfor Worldview, its online publication, and to perform intelligence gathering for corporate clients. The focus of Stratfor's content is security issues and analyzing geopolitical risk.

WikiLeaks is a publisher and media organisation founded in 2006. It operates as a non-profit and is funded by donations and media partnerships. It has published classified documents and other media provided by anonymous sources. It was founded by Julian Assange, an Australian editor, publisher, and activist, who is currently challenging extradition to the United States over his work with WikiLeaks. Since September 2018, Kristinn Hrafnsson has served as its editor-in-chief. Its website states that it has released more than ten million documents and associated analyses. WikiLeaks' most recent publication was in 2021 and its most recent publication of original documents was in 2019. Beginning in November 2022, many of the documents could not be accessed.

A data breach is a security violation, in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen, altered or used by an individual unauthorized to do so. Other terms are unintentional information disclosure, data leak, information leakage and data spill. Incidents range from concerted attacks by individuals who hack for personal gain or malice, organized crime, political activists or national governments, to poorly configured system security or careless disposal of used computer equipment or data storage media. Leaked information can range from matters compromising national security, to information on actions which a government or official considers embarrassing and wants to conceal. A deliberate data breach by a person privy to the information, typically for political purposes, is more often described as a "leak".
The WikiLeaks whistleblowing website founded by Julian Assange has received praise as well as criticism from the public, hacktivists, journalist organisations and government officials. The organisation has revealed human rights abuses and was the target of an alleged "cyber war". Allegations have been made that Wikileaks worked with or was exploited by the Russian government and acted in a partisan manner during the 2016 U.S. presidential election.
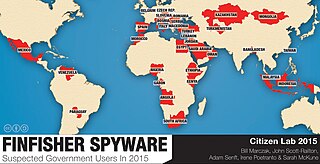
FinFisher, also known as FinSpy, is surveillance software marketed by Lench IT Solutions plc, which markets the spyware through law enforcement channels.
Emails by strategic intelligence company Stratfor, referred to by WikiLeaks as the Global Intelligence Files, began appearing on WikiLeaks on February 27, 2012, with 5,543,061 emails published as of July 18, 2014.

The practice of mass surveillance in the United States dates back to wartime monitoring and censorship of international communications from, to, or which passed through the United States. After the First and Second World Wars, mass surveillance continued throughout the Cold War period, via programs such as the Black Chamber and Project SHAMROCK. The formation and growth of federal law-enforcement and intelligence agencies such as the FBI, CIA, and NSA institutionalized surveillance used to also silence political dissent, as evidenced by COINTELPRO projects which targeted various organizations and individuals. During the Civil Rights Movement era, many individuals put under surveillance orders were first labelled as integrationists, then deemed subversive, and sometimes suspected to be supportive of the communist model of the United States' rival at the time, the Soviet Union. Other targeted individuals and groups included Native American activists, African American and Chicano liberation movement activists, and anti-war protesters.
The mass surveillance industry is a multibillion-dollar industry that has undergone phenomenal growth since 2001. According to data provided by The Wall Street Journal, the retail market for surveillance tools has grown from "nearly zero" in 2001 to about US$5 billion in 2011. The size of the video surveillance market rose to US$13.5 billion in 2012 and is expected to reach US$39 billion by 2020.

Ongoing news reports in the international media have revealed operational details about the Anglophone cryptographic agencies' global surveillance of both foreign and domestic nationals. The reports mostly emanate from a cache of top secret documents leaked by ex-NSA contractor Edward Snowden, which he obtained whilst working for Booz Allen Hamilton, one of the largest contractors for defense and intelligence in the United States. In addition to a trove of U.S. federal documents, Snowden's cache reportedly contains thousands of Australian, British, Canadian and New Zealand intelligence files that he had accessed via the exclusive "Five Eyes" network. In June 2013, the first of Snowden's documents were published simultaneously by The Washington Post and The Guardian, attracting considerable public attention. The disclosure continued throughout 2013, and a small portion of the estimated full cache of documents was later published by other media outlets worldwide, most notably The New York Times, the Canadian Broadcasting Corporation, the Australian Broadcasting Corporation, Der Spiegel (Germany), O Globo (Brazil), Le Monde (France), L'espresso (Italy), NRC Handelsblad, Dagbladet (Norway), El País (Spain), and Sveriges Television (Sweden).

Global mass surveillance can be defined as the mass surveillance of entire populations across national borders.
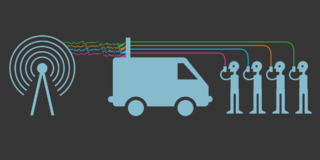
Cellphone surveillance may involve tracking, bugging, monitoring, eavesdropping, and recording conversations and text messages on mobile phones. It also encompasses the monitoring of people's movements, which can be tracked using mobile phone signals when phones are turned on.
HackingTeam was a Milan-based information technology company that sold offensive intrusion and surveillance capabilities to governments, law enforcement agencies and corporations. Its "Remote Control Systems" enable governments and corporations to monitor the communications of internet users, decipher their encrypted files and emails, record Skype and other Voice over IP communications, and remotely activate microphones and camera on target computers. The company has been criticized for providing these capabilities to governments with poor human rights records, though HackingTeam states that they have the ability to disable their software if it is used unethically. The Italian government has restricted their licence to do business with countries outside Europe.

Vault 7 is a series of documents that WikiLeaks began to publish on 7 March 2017, detailing the activities and capabilities of the United States Central Intelligence Agency (CIA) to perform electronic surveillance and cyber warfare. The files, dating from 2013 to 2016, include details on the agency's software capabilities, such as the ability to compromise cars, smart TVs, web browsers, and the operating systems of most smartphones, as well as other operating systems such as Microsoft Windows, macOS, and Linux. A CIA internal audit identified 91 malware tools out of more than 500 tools in use in 2016 being compromised by the release. The tools were developed by the Operations Support Branch of the C.I.A.
Kunstler v. Central Intelligence Agency is a lawsuit against the Central Intelligence Agency, former CIA Director Mike Pompeo, Undercover Global S.L., and David Morales Guillen filed by a group of American lawyers and journalists associated with WikiLeaks founder Julian Assange. The lawsuit alleges that the CIA violated their constitutional rights by recording their conversations with Assange and copying their phones and computers after suspicions were raised that Assange was working for the Russian intelligence services.









