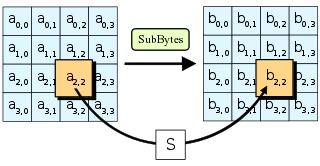
The Advanced Encryption Standard (AES), also known by its original name Rijndael, is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001.
In cryptography, a block cipher is a deterministic algorithm operating on fixed-length groups of bits, called blocks, with an unvarying transformation that is specified by a symmetric key. Block ciphers operate as important elementary components in the design of many cryptographic protocols, and are widely used to implement encryption of bulk data.

The Data Encryption Standard is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits makes it too insecure for modern applications, it has been highly influential in the advancement of cryptography.
In cryptography, RC4 is a stream cipher. While it is remarkable for its simplicity and speed in software, multiple vulnerabilities have been discovered in RC4, rendering it insecure. It is especially vulnerable when the beginning of the output keystream is not discarded, or when nonrandom or related keys are used. Particularly problematic uses of RC4 have led to very insecure protocols such as WEP.

A stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream). In a stream cipher, each plaintext digit is encrypted one at a time with the corresponding digit of the keystream, to give a digit of the ciphertext stream. Since encryption of each digit is dependent on the current state of the cipher, it is also known as state cipher. In practice, a digit is typically a bit and the combining operation is an exclusive-or (XOR).
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. The keys may be identical or there may be a simple transformation to go between the two keys. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. This requirement that both parties have access to the secret key is one of the main drawbacks of symmetric key encryption, in comparison to public-key encryption.
In computing, a linear-feedback shift register (LFSR) is a shift register whose input bit is a linear function of its previous state.

In cryptography, the Tiny Encryption Algorithm (TEA) is a block cipher notable for its simplicity of description and implementation, typically a few lines of code. It was designed by David Wheeler and Roger Needham of the Cambridge Computer Laboratory; it was first presented at the Fast Software Encryption workshop in Leuven in 1994, and first published in the proceedings of that workshop.
In cryptography, Camellia is a symmetric key block cipher with a block size of 128 bits and key sizes of 128, 192 and 256 bits. It was jointly developed by Mitsubishi Electric and NTT of Japan. The cipher has been approved for use by the ISO/IEC, the European Union's NESSIE project and the Japanese CRYPTREC project. The cipher has security levels and processing abilities comparable to the Advanced Encryption Standard.
In cryptography, MISTY1 is a block cipher designed in 1995 by Mitsuru Matsui and others for Mitsubishi Electric.
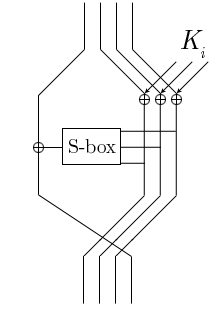
In cryptography, MacGuffin is a block cipher created in 1994 by Bruce Schneier and Matt Blaze at a Fast Software Encryption workshop. It was intended as a catalyst for analysis of a new cipher structure, known as Generalized Unbalanced Feistel Networks (GUFNs). The cryptanalysis proceeded very quickly, so quickly that the cipher was broken at the same workshop by Vincent Rijmen and Bart Preneel.
SOBER-128 is a synchronous stream cipher designed by Hawkes and Rose (2003) and is a member of the SOBER family of ciphers. SOBER-128 was also designed to provide MAC functionality.
In cryptography, MUGI is a pseudorandom number generator (PRNG) designed for use as a stream cipher. It was among the cryptographic techniques recommended for Japanese government use by CRYPTREC in 2003, however, has been dropped to "candidate" by CRYPTREC revision in 2013.
Anubis is a block cipher designed by Vincent Rijmen and Paulo S. L. M. Barreto as an entrant in the NESSIE project, a former research program initiated by the European Commission in 2000 for the identification of new cryptographic algorithms. Although the cipher has not been included in the final NESSIE portfolio, its design is considered very strong, and no attacks have been found by 2004 after the project had been concluded. The cipher is not patented and has been released by the designers for free public use.
In cryptography, Achterbahn is the name of a synchronous stream cipher algorithm submitted to the eSTREAM Project of the eCRYPT network. In the final specification the cipher is called ACHTERBAHN-128/80, because it supports the key lengths of 80 bits and 128 bits, respectively. Achterbahn was developed by Berndt Gammel, Rainer Göttfert and Oliver Kniffler. Achterbahn means rollercoaster, though a literal translation of the term would be eight-track, which indicates that the cipher can encrypt eight bit streams in parallel.
In cryptography, Hierocrypt-L1 and Hierocrypt-3 are block ciphers created by Toshiba in 2000. They were submitted to the NESSIE project, but were not selected. Both algorithms were among the cryptographic techniques recommended for Japanese government use by CRYPTREC in 2003, however, both have been dropped to "candidate" by CRYPTREC revision in 2013.
In cryptography, SOBER is a family of stream ciphers initially designed by Greg Rose of QUALCOMM Australia starting in 1997. The name is a contrived acronym for Seventeen Octet Byte Enabled Register. Initially the cipher was intended as a replacement for broken ciphers in cellular telephony. The ciphers evolved, and other developers joined the project.
ORYX is an encryption algorithm used in cellular communications in order to protect data traffic. It is a stream cipher designed to have a very strong 96-bit key strength with a way to reduce the strength to 32-bits for export. However, due to mistakes the actual strength is a trivial 16-bits and any signal can be cracked after the first 25–27 bytes.

Crypto1 is a proprietary encryption algorithm created by NXP Semiconductors specifically for Mifare RFID tags, including Oyster card, CharlieCard and OV-chipkaart.
Gregory G. "Greg" Rose was a senior vice president of technology for Qualcomm.





