Related Research Articles

Computing is any goal-oriented activity requiring, benefiting from, or creating computing machinery. It includes the study and experimentation of algorithmic processes, and development of both hardware and software. Computing has scientific, engineering, mathematical, technological and social aspects. Major computing disciplines include computer engineering, computer science, cybersecurity, data science, information systems, information technology, digital art and software engineering.

An embedded system is a computer system—a combination of a computer processor, computer memory, and input/output peripheral devices—that has a dedicated function within a larger mechanical or electronic system. It is embedded as part of a complete device often including electrical or electronic hardware and mechanical parts. Because an embedded system typically controls physical operations of the machine that it is embedded within, it often has real-time computing constraints. Embedded systems control many devices in common use. In 2009, it was estimated that ninety-eight percent of all microprocessors manufactured were used in embedded systems.
Checkpointing is a technique that provides fault tolerance for computing systems. It basically consists of saving a snapshot of the application's state, so that applications can restart from that point in case of failure. This is particularly important for long running applications that are executed in failure-prone computing systems.
TRON is an open architecture real-time operating system kernel design. The project was started by Professor Dr. Ken Sakamura of the University of Tokyo in 1984. The project's goal is to create an ideal computer architecture and network, to provide for all of society's needs.

Embedded software is computer software, written to control machines or devices that are not typically thought of as computers, commonly known as embedded systems. It is typically specialized for the particular hardware that it runs on and has time and memory constraints. This term is sometimes used interchangeably with firmware.

Component-based software engineering (CBSE), also called component-based development (CBD), is a branch of software engineering that emphasizes the separation of concerns with respect to the wide-ranging functionality available throughout a given software system. It is a reuse-based approach to defining, implementing and composing loosely coupled independent components into systems. This practice aims to bring about an equally wide-ranging degree of benefits in both the short-term and the long-term for the software itself and for organizations that sponsor such software.

PLECS is a software tool for system-level simulations of electrical circuits developed by Plexim. It is especially designed for power electronics but can be used for any electrical network. PLECS includes the possibility to model controls and different physical domains besides the electrical system.

T-Kernel is an open source real-time operating system (RTOS) designed for 32-bit microcontrollers. It is standardized by the T-Engine Forum, which distributes it under a T-License agreement. There is also a corresponding Micro T-Kernel (μT-Kernel) implementation designed for embedded systems with 16-bit or 8-bit microcontrollers.
Ch is a proprietary cross-platform C and C++ interpreter and scripting language environment. It was originally designed by Harry H. Cheng as a scripting language for beginners to learn mathematics, computing, numerical analysis, and programming in C/C++. Ch is now developed and marketed by SoftIntegration, Inc, with multiple versions available, including a freely available student edition and Ch Professional Edition for Raspberry Pi is free for non-commercial use.
Software-defined networking (SDN) technology is an approach to network management that enables dynamic, programmatically efficient network configuration in order to improve network performance and monitoring, in a manner more akin to cloud computing than to traditional network management. SDN is meant to address the static architecture of traditional networks and may be employed to centralize network intelligence in one network component by disassociating the forwarding process of network packets from the routing process. The control plane consists of one or more controllers, which are considered the brain of the SDN network, where the whole intelligence is incorporated. However, centralization has certain drawbacks related to security, scalability and elasticity.

RIOT is a small operating system for networked, memory-constrained systems with a focus on low-power wireless Internet of things (IoT) devices. It is open-source software, released under the GNU Lesser General Public License (LGPL).
Multi-access edge computing (MEC), formerly mobile edge computing, is an ETSI-defined network architecture concept that enables cloud computing capabilities and an IT service environment at the edge of the cellular network and, more in general at the edge of any network. The basic idea behind MEC is that by running applications and performing related processing tasks closer to the cellular customer, network congestion is reduced and applications perform better. MEC technology is designed to be implemented at the cellular base stations or other edge nodes, and enables flexible and rapid deployment of new applications and services for customers. Combining elements of information technology and telecommunications networking, MEC also allows cellular operators to open their radio access network (RAN) to authorized third parties, such as application developers and content providers.

Bashir Mohammed Ali Al-Hashimi, CBE, FRS, FREng, FIEEE, FIET, FBCS is a recognised multidisciplinary global researcher with sustained and pioneering contributions to computer engineering and a prominent academic and higher education leader. He is Vice President and ARM Professor of Computer Engineering at King's College London in the United Kingdom. He was the co-founder and co-director of the ARM-ECS Research Centre, an industry-university collaboration partnership involving the University of Southampton and ARM. He is actively involved in promoting science and engineering for young people and regularly contributes to engineering higher education and skills national debates.
Ramesh Govindan is an Indian-American professor of computer science. He is the Northrop Grumman Chair in Engineering and Professor of Computer Science and Electrical Engineering at the University of Southern California.
An AI accelerator is a class of specialized hardware accelerator or computer system designed to accelerate artificial intelligence and machine learning applications, including artificial neural networks and machine vision. Typical applications include algorithms for robotics, Internet of Things, and other data-intensive or sensor-driven tasks. They are often manycore designs and generally focus on low-precision arithmetic, novel dataflow architectures or in-memory computing capability. As of 2018, a typical AI integrated circuit chip contains billions of MOSFET transistors. A number of vendor-specific terms exist for devices in this category, and it is an emerging technology without a dominant design.
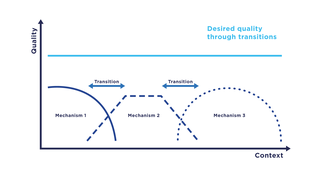
Transition refers to a computer science paradigm in the context of communication systems which describes the change of communication mechanisms, i.e., functions of a communication system, in particular, service and protocol components. In a transition, communication mechanisms within a system are replaced by functionally comparable mechanisms with the aim to ensure the highest possible quality, e.g., as captured by the quality of service.

Nader Bagherzadeh is a professor of Computer Engineering in the Department of Electrical Engineering and Computer Science at the University of California, Irvine, where he served as a chair from 1998 to 2003. Bagherzadeh has been involved in research and development in the areas of: Computer Architecture, Reconfigurable Computing, VLSI Chip Design, Network-on-Chip, 3D chips, Sensor Networks, Computer Graphics, Memory and Embedded Systems. Bagherzadeh was named Fellow of the Institute of Electrical and Electronics Engineers (IEEE) in 2014 for contributions to the design and analysis of coarse-grained reconfigurable processor architectures. Bagherzadeh has published more than 400 articles in peer-reviewed journals and conferences. He was with AT&T Bell Labs from 1980 to 1984.
Bare Machine Computing (BMC) is a computer architecture based on bare machines. In the BMC paradigm, applications run without the support of any operating system (OS) or centralized kernel i.e., no intermediary software is loaded on the bare machine prior to running applications. The applications, which are called bare machine applications or simply BMC applications, do not use any persistent storage or a hard disk, and instead are stored on detachable mass storage such as a USB flash drive. A BMC program consists of a single application or a small set of applications that runs as a single executable within one address space. BMC applications have direct access to the necessary hardware resources. They are self-contained, self-managed and self-controlled entities that boot, load and run without using any other software components or external software. BMC applications have inherent security due to their design. There are no OS-related vulnerabilities, and each application only contains the necessary (minimal) functionality. There is no privileged mode in a BMC system since applications only run in user mode. Also, application code is statically compiled-there is no means to dynamically alter BMC program flow during execution.
The booting process of Android devices starts at the power-on of the SoC and ends at the visibility of the home screen, or special modes like recovery and fastboot. The boot process of devices that run Android is influenced by the firmware design of the SoC manufacturers.
References
- ↑ Dalmasso, Isabelle; Datta, Soumya Kanti; Bonnet, Christian; Nikaein, Navid (July 2013), "Survey, comparison and evaluation of cross platform mobile application development tools", 2013 9th International Wireless Communications and Mobile Computing Conference (IWCMC), Institute of Electrical & Electronics Engineers (IEEE), pp. 323–328, doi:10.1109/iwcmc.2013.6583580, S2CID 15990920 .
- ↑ Tsiligkos, Kleomenis; Meliones, Apostolos (August 2014), "Formulating Optimized Storage and Memory Space Specifications for Linux Network Embedded Systems", 2014 IEEE International Conference on High Performance Computing and Communications, 6th International Symposium on Cyberspace Safety and Security, and 11th International Conference on Embedded Software and Syst (HPCC, CSS, ICESS), Institute of Electrical & Electronics Engineers (IEEE), pp. 580–584, doi:10.1109/hpcc.2014.99, S2CID 9689524 .
- ↑ Mackall, Matt (2009), "smem: understanding memory usage" (PDF), Embedded Linux Conference.
- ↑ corbet (April 18, 2007), ELC: How much memory are applications really using?, LWN.net , retrieved 2016-03-17.