Related Research Articles
Internetwork Packet Exchange (IPX) is the network layer protocol in the IPX/SPX protocol suite. IPX is derived from Xerox Network Systems' IDP. It also has the ability to act as a transport layer protocol.
The Internet protocol suite, commonly known as TCP/IP, is a framework for organizing the set of communication protocols used in the Internet and similar computer networks according to functional criteria. The foundational protocols in the suite are the Transmission Control Protocol (TCP), the User Datagram Protocol (UDP), and the Internet Protocol (IP). Early versions of this networking model were known as the Department of Defense (DoD) model because the research and development were funded by the United States Department of Defense through DARPA.

The Open Systems Interconnection model is a conceptual model, originally conceived as the 7 layer onion skin architecture by Jack Holdsworth of ICL, that 'provides a common basis for the coordination of [ISO] standards development for the purpose of systems interconnection'. In the OSI reference model, the communications between a computing system are split into seven different abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application.
In computer networking, Point-to-Point Protocol (PPP) is a data link layer communication protocol between two routers directly without any host or any other networking in between. It can provide loop connection authentication, transmission encryption, and data compression.

X.25 is an ITU-T standard protocol suite for packet-switched data communication in wide area networks (WAN). It was originally defined by the International Telegraph and Telephone Consultative Committee in a series of drafts and finalized in a publication known as The Orange Book in 1976.
The Routing Information Protocol (RIP) is one of the oldest distance-vector routing protocols which employs the hop count as a routing metric. RIP prevents routing loops by implementing a limit on the number of hops allowed in a path from source to destination. The largest number of hops allowed for RIP is 15, which limits the size of networks that RIP can support.

Network address translation (NAT) is a method of mapping an IP address space into another by modifying network address information in the IP header of packets while they are in transit across a traffic routing device. The technique was originally used to bypass the need to assign a new address to every host when a network was moved, or when the upstream Internet service provider was replaced, but could not route the network's address space. It has become a popular and essential tool in conserving global address space in the face of IPv4 address exhaustion. One Internet-routable IP address of a NAT gateway can be used for an entire private network.
In the IEEE 802 reference model of computer networking, the logical link control (LLC) data communication protocol layer is the upper sublayer of the data link layer of the seven-layer OSI model. The LLC sublayer acts as an interface between the media access control (MAC) sublayer and the network layer.
A virtual private network (VPN) is a mechanism for creating a secure connection between a computing device and a computer network, or between two networks, using an insecure communication medium such as the public Internet. A VPN can extend a private network, enabling users to send and receive data across public networks as if their devices were directly connected to the private network. The benefits of a VPN include security, reduced costs for dedicated communication lines, and greater flexibility for remote workers. VPNs are also used to bypass internet censorship. Encryption is common, although not an inherent part of a VPN connection.
Network congestion in data networking and queueing theory is the reduced quality of service that occurs when a network node or link is carrying more data than it can handle. Typical effects include queueing delay, packet loss or the blocking of new connections. A consequence of congestion is that an incremental increase in offered load leads either only to a small increase or even a decrease in network throughput.
The computer file hosts is an operating system file that maps hostnames to IP addresses. It is a plain text file. Originally a file named HOSTS.TXT was manually maintained and made available via file sharing by Stanford Research Institute for the ARPANET membership, containing the hostnames and address of hosts as contributed for inclusion by member organizations. The Domain Name System, first described in 1983 and implemented in 1984, automated the publication process and provided instantaneous and dynamic hostname resolution in the rapidly growing network. In modern operating systems, the hosts file remains an alternative name resolution mechanism, configurable often as part of facilities such as the Name Service Switch as either the primary method or as a fallback method.
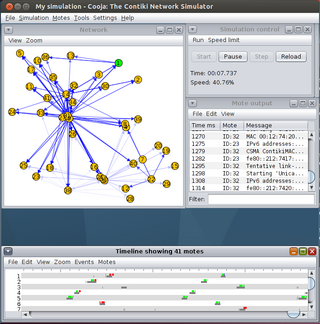
Contiki is an operating system for networked, memory-constrained systems with a focus on low-power wireless Internet of Things (IoT) devices. Contiki is used for systems for street lighting, sound monitoring for smart cities, radiation monitoring and alarms. It is open-source software released under the BSD-3-Clause license.
Internet traffic is the flow of data within the entire Internet, or in certain network links of its constituent networks. Common traffic measurements are total volume, in units of multiples of the byte, or as transmission rates in bytes per certain time units.

NetFlow is a feature that was introduced on Cisco routers around 1996 that provides the ability to collect IP network traffic as it enters or exits an interface. By analyzing the data provided by NetFlow, a network administrator can determine things such as the source and destination of traffic, class of service, and the causes of congestion. A typical flow monitoring setup consists of three main components:
Local Area Transport (LAT) is a non-routable networking technology developed by Digital Equipment Corporation to provide connection between the DECserver terminal servers and Digital's VAX and Alpha and MIPS host computers via Ethernet, giving communication between those hosts and serial devices such as video terminals and printers. The protocol itself was designed in such a manner as to maximize packet efficiency over Ethernet by bundling multiple characters from multiple ports into a single packet for Ethernet transport.
Cisco HDLC (cHDLC) is an extension to the High-Level Data Link Control (HDLC) network protocol, and was created by Cisco Systems, Inc. HDLC is a bit-oriented synchronous data link layer protocol that was originally developed by the International Organization for Standardization (ISO). Often described as being a proprietary extension, the details of cHDLC have been widely distributed and the protocol has been implemented by many network equipment vendors. cHDLC extends HDLC with multi-protocol support.

Cerent Corporation was an optical equipment maker based in Petaluma, California. It was founded in 1997 as Fiberlane Communications with funding from Kleiner Perkins Caufield & Byers and Vinod Khosla as the managing VC. The company was founded with three divisions: Systems in Petaluma, Chip Design in Mountain View, California and Network Management Systems in Burnaby, British Columbia. In early 1998 the company split into two companies with the Petaluma branch becoming Cerent and the Burnaby and Mountain View branches becoming Siara Systems.
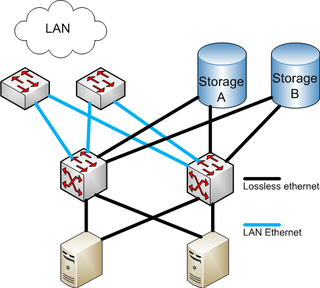
Fibre Channel over Ethernet (FCoE) is a computer network technology that encapsulates Fibre Channel frames over Ethernet networks. This allows Fibre Channel to use 10 Gigabit Ethernet networks while preserving the Fibre Channel protocol. The specification was part of the International Committee for Information Technology Standards T11 FC-BB-5 standard published in 2009.
The uIP is an open-source implementation of the TCP/IP network protocol stack intended for use with tiny 8- and 16-bit microcontrollers. It was initially developed by Adam Dunkels of the Networked Embedded Systems group at the Swedish Institute of Computer Science, licensed under a BSD style license, and further developed by a wide group of developers.
A long-running debate in computer science known as the Protocol Wars occurred from the 1970s to the 1990s when engineers, organizations and nations became polarized over the issue of which communication protocol would result in the best and most robust computer networks. This culminated in the Internet–OSI Standards War in the late 1980s and early 1990s, which was ultimately "won" by the Internet protocol suite ("TCP/IP") by the mid-1990s and has since resulted in most other protocols disappearing.
References
- ↑ Satz, G.; Day, R.; Glick, G.; Forster, J. (1994). "cisco Systems X.25 over TCP (XOT)". tools.ietf.org. doi:10.17487/RFC1613 . Retrieved 2020-11-09.
- ↑ Goff Hill (26 July 2012). The Cable and Telecommunications Professionals' Reference: Transport Networks. CRC Press. p. 361. ISBN 978-1-136-03434-3.