
Research is "creative and systematic work undertaken to increase the stock of knowledge". It involves the collection, organization and analysis of evidence to increase understanding of a topic, characterized by a particular attentiveness to controlling sources of bias and error. These activities are characterized by accounting and controlling for biases. A research project may be an expansion of past work in the field. To test the validity of instruments, procedures, or experiments, research may replicate elements of prior projects or the project as a whole.
A case study is an in-depth, detailed examination of a particular case within a real-world context. For example, case studies in medicine may focus on an individual patient or ailment; case studies in business might cover a particular firm's strategy or a broader market; similarly, case studies in politics can range from a narrow happening over time like the operations of a specific political campaign, to an enormous undertaking like world war, or more often the policy analysis of real-world problems affecting multiple stakeholders.

Qualitative research is a type of research that aims to gather and analyse non-numerical (descriptive) data in order to gain an understanding of individuals' social reality, including understanding their attitudes, beliefs, and motivation. This type of research typically involves in-depth interviews, focus groups, or observations in order to collect data that is rich in detail and context. Qualitative research is often used to explore complex phenomena or to gain insight into people's experiences and perspectives on a particular topic. It is particularly useful when researchers want to understand the meaning that people attach to their experiences or when they want to uncover the underlying reasons for people's behavior. Qualitative methods include ethnography, grounded theory, discourse analysis, and interpretative phenomenological analysis. Qualitative research methods have been used in sociology, anthropology, political science, psychology, communication studies, social work, folklore, educational research, information science and software engineering research.

Quantitative research is a research strategy that focuses on quantifying the collection and analysis of data. It is formed from a deductive approach where emphasis is placed on the testing of theory, shaped by empiricist and positivist philosophies.

Content analysis is the study of documents and communication artifacts, which might be texts of various formats, pictures, audio or video. Social scientists use content analysis to examine patterns in communication in a replicable and systematic manner. One of the key advantages of using content analysis to analyse social phenomena is their non-invasive nature, in contrast to simulating social experiences or collecting survey answers.
DSI may refer to:

Data analysis is the process of inspecting, cleansing, transforming, and modeling data with the goal of discovering useful information, informing conclusions, and supporting decision-making. Data analysis has multiple facets and approaches, encompassing diverse techniques under a variety of names, and is used in different business, science, and social science domains. In today's business world, data analysis plays a role in making decisions more scientific and helping businesses operate more effectively.
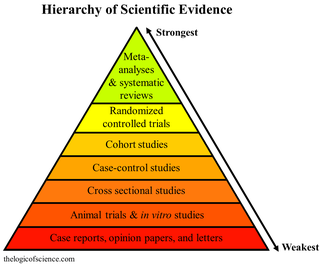
A systematic review is a scholarly synthesis of the evidence on a clearly presented topic using critical methods to identify, define and assess research on the topic. A systematic review extracts and interprets data from published studies on the topic, then analyzes, describes, critically appraises and summarizes interpretations into a refined evidence-based conclusion. For example, a systematic review of randomized controlled trials is a way of summarizing and implementing evidence-based medicine.

Sociology of terrorism is a field of sociology that seeks to understand terrorism as a social phenomenon. The field defines terrorism, studies why it occurs and evaluates its impacts on society. The sociology of terrorism draws from the fields of political science, history, economics and psychology. The sociology of terrorism differs from critical terrorism studies, emphasizing the social conditions that enable terrorism. It also studies how individuals as well as states respond to such events.
In the social sciences, coding is an analytical process in which data, in both quantitative form or qualitative form are categorized to facilitate analysis.
Quantitative methods provide the primary research methods for studying the distribution and causes of crime. Quantitative methods provide numerous ways to obtain data that are useful to many aspects of society. The use of quantitative methods such as survey research, field research, and evaluation research as well as others. The data can, and is often, used by criminologists and other social scientists in making causal statements about variables being researched.
The marketing research process is a six-step process involving the definition of the problem being studied upon, determining what approach to take, formulation of research design, field work entailed, data preparation and analysis, and the generation of reports, how to present these reports, and overall, how the task can be accomplished.
RQDA is an R package for computer assisted qualitative data analysis or CAQDAS. It is installable from, and runs within, the R statistical software, but has a separate window running a graphical user interface. RQDA's approach allows for tight integration of the constructivist approach of qualitative research with quantitative data analysis which can increase the rigor, transparency and validity of qualitative research.
MAXQDA is a software program designed for computer-assisted qualitative and mixed methods data, text and multimedia analysis in academic, scientific, and business institutions. It is being developed and distributed by VERBI Software based in Berlin, Germany.
The WomanStats Project is a donor-funded research and database project housed at Brigham Young University that "seeks to collect detailed statistical data on the status of women around the world, and to connect that data with data on the security of states." The WomanStats Database has the most comprehensive compilation of information on the status of women in the world. Coders comb the extant literature and conduct expert interviews to find qualitative and quantitative information on over 300 indicators of women's status in 174 countries with populations of at least 200,000. Access to the online database is free.

The Global Terrorism Index (GTI) is a report published annually by the Institute for Economics and Peace (IEP), and was developed by IT entrepreneur and IEP's founder Steve Killelea. The index provides a comprehensive summary of the key global trends and patterns in terrorism since 2000. It is an attempt to systematically rank the nations of the world according to terrorist activity. The index combines a number of factors associated with terrorist attacks to build an explicit picture of the impact of terrorism, illustrating trends, and providing a data series for analysis by researchers and policymakers. It produces a composite score in order to provide an ordinal ranking of countries on the impact of terrorism.

The Global Terrorism Database (GTD) is a database of terrorist incidents from 1970 onward. As of May 2021, the list extended through 2019 recording over 200,000 incidents, although data from 1993 is excluded. The database is maintained by the National Consortium for the Study of Terrorism and Responses to Terrorism (START) at the University of Maryland, College Park in the United States. It is also the basis for other terrorism-related measures, such as the Global Terrorism Index (GTI) published by the Institute for Economics and Peace.

Quirkos is a CAQDAS software package for the qualitative analysis of text data, commonly used in social science. It provides a graphical interface in which the nodes or themes of analysis are represented by bubbles. It is designed primarily for new and non-academic users of qualitative data, to allow them to quickly learn the basics of qualitative data analysis. Although simpler to use, it lacks some of the features present in other commercial CAQDAS packages such as multimedia support. However, it has been proposed as a useful tool for lay and participant led analysis and is comparatively affordable. It is developed by Edinburgh, UK based Quirkos Software, and was first released in October 2014.
This glossary of computer science is a list of definitions of terms and concepts used in computer science, its sub-disciplines, and related fields, including terms relevant to software, data science, and computer programming.

The economics of terrorism is a branch of economics dedicated to the study of terrorism. It involves using the tools of economic analysis to analyse issues related to terrorism, such as the link between education, poverty and terrorism, the effect of macroeconomic conditions on the frequency and quality of terrorism, the economic costs of terrorism, and the economics of counter-terrorism. The field also extends to the political economy of terrorism, which seeks to answer questions on the effect of terrorism on voter preferences and party politics.