
A field-programmable gate array (FPGA) is a type of integrated circuit that can be programmed or reprogrammed after manufacturing. It consists of an array of programmable logic block and interconnects that can be configured to perform various digital functions. FPGAs are commonly used in applications where flexibility, speed, and parallel processing capabilities are required, such as in telecommunications, automotive, aerospace, and industrial sectors.
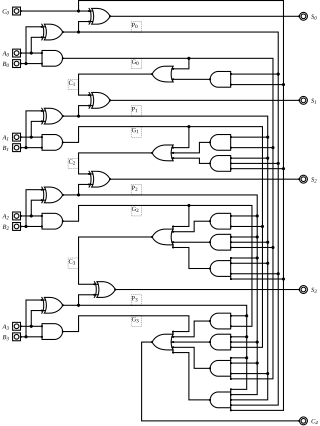
A logic gate is an idealized or physical device that performs a Boolean function, a logical operation performed on one or more binary inputs that produces a single binary output.
An intrusion detection system is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management (SIEM) system. A SIEM system combines outputs from multiple sources and uses alarm filtering techniques to distinguish malicious activity from false alarms.
ATPG is an electronic design automation method or technology used to find an input sequence that, when applied to a digital circuit, enables automatic test equipment to distinguish between the correct circuit behavior and the faulty circuit behavior caused by defects. The generated patterns are used to test semiconductor devices after manufacture, or to assist with determining the cause of failure. The effectiveness of ATPG is measured by the number of modeled defects, or fault models, detectable and by the number of generated patterns. These metrics generally indicate test quality and test application time. ATPG efficiency is another important consideration that is influenced by the fault model under consideration, the type of circuit under test, the level of abstraction used to represent the circuit under test, and the required test quality.
JTAG is an industry standard for verifying designs and testing printed circuit boards after manufacture.
In electronics and computing, a soft error is a type of error where a signal or datum is wrong. Errors may be caused by a defect, usually understood either to be a mistake in design or construction, or a broken component. A soft error is also a signal or datum which is wrong, but is not assumed to imply such a mistake or breakage. After observing a soft error, there is no implication that the system is any less reliable than before. One cause of soft errors is single event upsets from cosmic rays.

A Medium Attachment Unit (MAU) is a transceiver which converts signals on an Ethernet cable to and from Attachment Unit Interface (AUI) signals.

Boundary scan is a method for testing interconnects on printed circuit boards or sub-blocks inside an integrated circuit. Boundary scan is also widely used as a debugging method to watch integrated circuit pin states, measure voltage, or analyze sub-blocks inside an integrated circuit.
Design for testing or design for testability (DFT) consists of IC design techniques that add testability features to a hardware product design. The added features make it easier to develop and apply manufacturing tests to the designed hardware. The purpose of manufacturing tests is to validate that the product hardware contains no manufacturing defects that could adversely affect the product's correct functioning.
In computer architecture, clock gating is a popular power management technique used in many synchronous circuits for reducing dynamic power dissipation, by removing the clock signal when the circuit, or a subpart of it, is not in use or ignores clock signal. Clock gating saves power by pruning the clock tree, at the cost of adding more logic to a circuit. Pruning the clock disables portions of the circuitry so that the flip-flops in them do not switch state, as switching the state consumes power. When not being switched, the switching power consumption goes to zero, and only leakage currents are incurred.
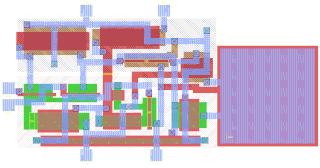
Integrated circuit design, or IC design, is a sub-field of electronics engineering, encompassing the particular logic and circuit design techniques required to design integrated circuits, or ICs. ICs consist of miniaturized electronic components built into an electrical network on a monolithic semiconductor substrate by photolithography.
Data loss prevention (DLP) software detects potential data breaches/data exfiltration transmissions and prevents them by monitoring, detecting and blocking sensitive data while in use, in motion, and at rest.
The Advanced Learning and Research Institute (ALaRI), a faculty of informatics, was established in 1999 at the University of Lugano to promote research and education in embedded systems. The Faculty of Informatics within very few years has become one of the Switzerland major destinations for teaching and research, ranking third after the two Federal Institutes of Technology, Zurich and Lausanne.

A physical unclonable function, or PUF, is a physical object that for a given input and conditions (challenge), provides a physically defined "digital fingerprint" output (response) that serves as a unique identifier, most often for a semiconductor device such as a microprocessor. PUFs are often based on unique physical variations occurring naturally during semiconductor manufacturing. A PUF is a physical entity embodied in a physical structure. PUFs are implemented in integrated circuits, including FPGAs, and can be used in applications with high-security requirements, more specifically cryptography, Internet of Things (IOT) devices and privacy protection.
In the electronics industry, embedded instrumentation refers to the integration of test and measurement instrumentation into semiconductor chips. Embedded instrumentation differs from embedded system, which are electronic systems or subsystems that usually comprise the control portion of a larger electronic system. Instrumentation embedded into chips is employed in a variety of electronic test applications, including validating and testing chips themselves, validating, testing and debugging the circuit boards where these chips are deployed, and troubleshooting systems once they have been installed in the field.
Physical unclonable function (PUF), sometimes also called physically unclonable function, is a physical entity that is embodied in a physical structure and is easy to evaluate but hard to predict.
Hardware backdoors are backdoors in hardware, such as code inside hardware or firmware of computer chips. The backdoors may be directly implemented as hardware Trojans in the integrated circuit.
Hardware security is a discipline originated from the cryptographic engineering and involves hardware design, access control, secure multi-party computation, secure key storage, ensuring code authenticity, measures to ensure that the supply chain that built the product is secure among other things.
A security switch is a hardware device designed to protect computers, laptops, smartphones and similar devices from unauthorized access or operation, distinct from a virtual security switch which offers software protection. Security switches should be operated by an authorized user only; for this reason, it should be isolated from other devices, in order to prevent unauthorized access, and it should not be possible to bypass it, in order to prevent malicious manipulation.

Mark M. Tehranipoor is an Iranian American academic researcher specializing in hardware security and trust, electronics supply chain security, IoT security, and reliable and testable VLSI design. He is the Intel Charles E. Young Preeminence Endowed Professor in Cybersecurity at the University of Florida and serves as the Director of the Florida Institute for Cybersecurity Research. Since June 2022, he has served as the chair of the Department of Electrical and Computer Engineering at the University of Florida. He is a fellow of IEEE, ACM, and NAI as well as a Golden Core member of the IEEE. He is a co-founder of the International Symposium on Hardware Oriented Security and Trust (HOST). He is the recipient of the 2023 SRC Aristotle award. Tehranipoor also serves as a co-director of the Air Force Office of Scientific Research CYAN and MEST Centers of Excellence.







