Mobile Slotted Aloha (MS-Aloha) is a wireless network protocol proposed for applications such as vehicle networks.

A wireless network is a computer network that uses wireless data connections between network nodes.
Contents

Mobile Slotted Aloha (MS-Aloha) is a wireless network protocol proposed for applications such as vehicle networks.

A wireless network is a computer network that uses wireless data connections between network nodes.

Considering the typical taxonomy of MAC protocols, MS-Aloha represents a hybrid solution. It is based on connection-oriented paradigm (hence may fall in the class of channel-based/TDMA protocols); however it is also very reactive to topology changes and does not include any reservations separate from data exchanges. It is classified among the packet-based and collision-free MAC methods.[ citation needed ]
In general, a slotted protocol can be either connectionless or connection-oriented. However, only the latter case represents a true alternative to IEEE 802.11p, by introducing the determinism which carrier sense multiple access with collision avoidance (CSMA/CA) lacks. In vehicle networks the connection set-up phases of a telephone call (reservation request, confirmation, data exchange, tear-down) cannot be applied (it does not hold for broadcast communications, it is hampered by hidden stations, it is not manageable with heavy losses, mobility and varying channel conditions). For these reasons MS-Aloha is connection oriented and continuously refreshes each reservation simply by transmitting each period. MS-Aloha adopts a different approach and subtends the following hypotheses and rules which, basically, define all its main mechanisms.[ citation needed ]
IEEE 802.11p is an approved amendment to the IEEE 802.11 standard to add wireless access in vehicular environments (WAVE), a vehicular communication system. It defines enhancements to 802.11 required to support Intelligent Transportation Systems (ITS) applications. This includes data exchange between high-speed vehicles and between the vehicles and the roadside infrastructure, so called V2X communication, in the licensed ITS band of 5.9 GHz (5.85-5.925 GHz). IEEE 1609 is a higher layer standard based on the IEEE 802.11p. It is also the basis of a European standard for vehicular communication known as ETSI ITS-G5.

Ethernet is a family of computer networking technologies commonly used in local area networks (LAN), metropolitan area networks (MAN) and wide area networks (WAN). It was commercially introduced in 1980 and first standardized in 1983 as IEEE 802.3, and has since retained a good deal of backward compatibility and been refined to support higher bit rates and longer link distances. Over time, Ethernet has largely replaced competing wired LAN technologies such as Token Ring, FDDI and ARCNET.

Carrier-sense multiple access with collision avoidance (CSMA/CA) in computer networking, is a network multiple access method in which carrier sensing is used, but nodes attempt to avoid collisions by beginning transmission only after the channel is sensed to be "idle". When they do transmit, nodes transmit their packet data in its entirety.
Carrier-sense multiple access with collision detection (CSMA/CD) is a media access control method used most notably in early Ethernet technology for local area networking. It uses carrier-sensing to defer transmissions until no other stations are transmitting. This is used in combination with collision detection in which a transmitting station detects collisions by sensing transmissions from other stations while it is transmitting a frame. When this collision condition is detected, the station stops transmitting that frame, transmits a jam signal, and then waits for a random time interval before trying to resend the frame.
Carrier-sense multiple access (CSMA) is a media access control (MAC) protocol in which a node verifies the absence of other traffic before transmitting on a shared transmission medium, such as an electrical bus or a band of the electromagnetic spectrum.
In telecommunications and computer networks, a channel access method or multiple access method allows more than two terminals connected to the same transmission medium to transmit over it and to share its capacity. Examples of shared physical media are wireless networks, bus networks, ring networks and point-to-point links operating in half-duplex mode.
ALOHAnet, also known as the ALOHA System, or simply ALOHA, was a pioneering computer networking system developed at the University of Hawaii. ALOHAnet became operational in June, 1971, providing the first public demonstration of a wireless packet data network. ALOHA originally stood for Additive Links On-line Hawaii Area.
In the IEEE 802 reference model of computer networking, the logical link control (LLC) data communication protocol layer is the upper sublayer of the data link layer of the seven-layer OSI model. The LLC sublayer provides multiplexing mechanisms that make it possible for several network protocols to coexist within a multipoint network and to be transported over the same network medium. It can also provide flow control and automatic repeat request (ARQ) error management mechanisms.
The data layer, or layer 2, is the second layer of the seven-layer OSI model of computer networking. This layer is the protocol layer that transfers data between adjacent network nodes in a wide area network (WAN) or between nodes on the same local area network (LAN) segment. The data link layer provides the functional and procedural means to transfer data between network entities and might provide the means to detect and possibly correct errors that may occur in the physical layer.
In IEEE 802 LAN/MAN standards, the medium access control (MAC) sublayer is the layer that controls the hardware responsible for interaction with the wired, optical or wireless transmission medium. The MAC sublayer and the logical link control (LLC) sublayer together make up the data link layer. Within the data link layer, the LLC provides flow control and multiplexing for the logical link, while the MAC provides flow control and multiplexing for the transmission medium.
HiperLAN is a Wireless LAN standard. It is a European alternative for the IEEE 802.11 standards. It is defined by the European Telecommunications Standards Institute (ETSI). In ETSI the standards are defined by the BRAN project. The HiperLAN standard family has four different versions.
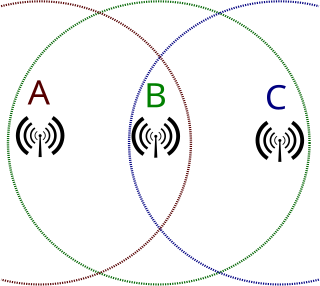
In wireless networking, the hidden node problem or hidden terminal problem occurs when a node can communicate with a wireless access point (AP), but cannot directly communicate with other nodes that are communicating with that AP. This leads to difficulties in medium access control sublayer since multiple nodes can send data packets to the AP simultaneously, which creates interference at the AP resulting in neither packet getting through.
IEEE 802.15.4 is a technical standard which defines the operation of low-rate wireless personal area networks (LR-WPANs). It specifies the physical layer and media access control for LR-WPANs, and is maintained by the IEEE 802.15 working group, which defined the standard in 2003. It is the basis for the Zigbee, ISA100.11a, WirelessHART, MiWi, 6LoWPAN, Thread and SNAP specifications, each of which further extends the standard by developing the upper layers which are not defined in IEEE 802.15.4. In particular, 6LoWPAN defines a binding for the IPv6 version of the Internet Protocol (IP) over WPANs, and is itself used by upper layers like Thread.
Slot time is a concept in computer networking. It is at least twice the time it takes for an electronic pulse to travel the length of the maximum theoretical distance between two nodes. In CSMA/CD networks such as Ethernet, the slot time is an upper limit on the acquisition of the medium, a limit on the length of a packet fragment generated by a collision, and the scheduling quantum for retransmission.

A wireless mesh network (WMN) is a communications network made up of radio nodes organized in a mesh topology. It is also a form of wireless ad hoc network.
Vehicular ad-hoc networks (VANETs) are created by applying the principles of mobile ad hoc networks (MANETs) – the spontaneous creation of a wireless network of mobile devices – to the domain of vehicles. VANETs were first mentioned and introduced in 2001 under "car-to-car ad-hoc mobile communication and networking" applications, where networks can be formed and information can be relayed among cars. It was shown that vehicle-to-vehicle and vehicle-to-roadside communications architectures will co-exist in VANETs to provide road safety, navigation, and other roadside services. VANETs are a key part of the intelligent transportation systems (ITS) framework. Sometimes, VANETs are referred as Intelligent Transportation Networks
A wireless ad hoc network (WANET) or MANET is a decentralised type of wireless network. The network is ad hoc because it does not rely on a pre-existing infrastructure, such as routers in wired networks or access points in managed (infrastructure) wireless networks. Instead, each node participates in routing by forwarding data for other nodes, so the determination of which nodes forward data is made dynamically on the basis of network connectivity and the routing algorithm in use.
Multiple Access with Collision Avoidance for Wireless (MACAW) is a slotted medium access control (MAC) protocol widely used in ad hoc networks. Furthermore, it is the foundation of many other MAC protocols used in wireless sensor networks (WSN). The IEEE 802.11 RTS/CTS mechanism is adopted from this protocol. It uses RTS-CTS-DS-DATA-ACK frame sequence for transferring data, sometimes preceded by an RTS-RRTS frame sequence, in view to provide solution to the hidden node problem. Although protocols based on MACAW, such as S-MAC, use carrier sense in addition to the RTS/CTS mechanism, MACAW does not make use of carrier sense.
Intelligent vehicular ad hoc networks (InVANETs) use WiFi IEEE 802.11p and WiMAX IEEE 802.16 for easy and effective communication between vehicles with dynamic mobility. Effective measures such as media communication between vehicles can be enabled as well methods to track automotive vehicles. InVANET is not foreseen to replace current mobile communication standards.
A mobile ad hoc network (MANET), also known as wireless ad hoc network or ad hoc wireless network, is a continuously self-configuring, infrastructure-less network of mobile devices connected wirelessly.
Vehicular Ad hoc Networks (VANETs) is a network protocol designed for traffic safety applications. As other computer network protocols, it is also subject to several attacks that can have fatal consequences due to the VANET's intended usage. One of these possible attacks is location spoofing where the attacker is lying about a vehicle's position to disrupt VANET safety application. This attack can be performed either through existent vehicles or forging new identities by a Sybil attack. There are several publications that propose mechanisms to detect and correct malicious location advertisements. This article presents an overview of some of these verification mechanisms proposed in the literature.
| This technology-related article is a stub. You can help Wikipedia by expanding it. |