| AIDS | |
|---|---|
| Technical name | AIDS |
 | |
| Alias | AIDSB, AIDS-II, AIDS II, AIDS92, Hahaha, Taunt |
| Type | DOS |
| Subtype | |
| Classification | Virus |
| Family | N/A |
| Origin | Unknown |
| Authors | Unknown |
AIDS is a DOS computer virus which overwrites COM files.
| AIDS | |
|---|---|
| Technical name | AIDS |
 | |
| Alias | AIDSB, AIDS-II, AIDS II, AIDS92, Hahaha, Taunt |
| Type | DOS |
| Subtype | |
| Classification | Virus |
| Family | N/A |
| Origin | Unknown |
| Authors | Unknown |
AIDS is a DOS computer virus which overwrites COM files.
AIDS is the first virus known to exploit the MS-DOS "corresponding file" vulnerability. In MS-DOS, if the user enters FOO in the command interpreter, in a directory where both FOO.COM and FOO.EXE exist, then FOO.COM will always be executed. Thus, by creating infected COM files, AIDS code will always be executed before the intended EXE file. [1]
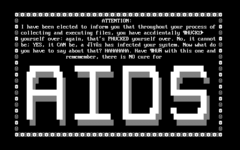
When the AIDS virus activates, it displays the following screen (bracketed comments not in original): [2]
ATTENTION: I have been elected to inform you that throughout your process of collecting and executing files, you have accidentally ¶HÜ¢KΣ► [phucked in leet] yourself over: again, that's PHUCKED yourself over. No, it cannot be; YES, it CAN be, a √ìτûs [virus] has infected your system. Now what do you have to say about that? HAHAHAHAHA. Have ¶HÜÑ [phun] with this one and rememember, there is NO cure for AIDS
In the message above, the word "AIDS" covers about half of the screen. The system is then halted, and must be powered down and rebooted to restart it. [3]
The AIDS virus overwrites the first 13,952 bytes of an infected COM file. Overwritten files must be deleted and replaced with clean copies in order to remove the virus. It is not possible to recover the overwritten portion of the program. [4]
| AIDS 2 | |
|---|---|
| Technical name | AIDS II.8064 |
| Alias | AIDS-II, Aids.8064, AIDS_8064, AIDS_II.8064 |
| Type | DOS |
| Subtype | EXE to COM companion General nuisance |
| Classification | Virus |
| Family | AIDS II |
| Origin | Unknown |
| Authors | WOP & PGT of DutchCrack |
AIDS II is a companion computer virus, which infects COM files. First discovered in April 1990, it appears to be a more elegant revision of AIDS, which also employs the corresponding file technique to execute infected code. [4]
Unlike generic file infectors, AIDS II is the second known virus to use the "corresponding file technique" of infection (after the original AIDS), and the first to use this technique in a way that does not modify the original target EXE file. AIDS II works by first finding an uninfected EXE file in the working directory and then creating a companion COM file with the viral code. The COM files will always be 8,064 bytes in length, with a timestamp corresponding to the time of infection. After creating the new COM file, the virus then plays a loud note, and displays the following message: [4]
Your computer is infected with ...
- ❤Aids Virus II❤
- Signed WOP & PGT of DutchCrack -
AIDS II then executes EXE file the user intended to execute without incident. Once that program is exited, control returns to the virus. The note is replayed, with a new message displayed: [4]
Getting used to me? Next time, use a Condom .....
Since the EXE file is unchanged, cyclic redundancy checks, such as those present in antivirus software, cannot detect this virus having infected a system. A way to remove AIDS II manually is to check for EXE files with an identically named COM file 8,064 bytes in length. Those COM files can be deleted. [4]
According to Symantec, AIDS II may play a melody and display the following string: [5]
Your computer is infected with AIDS VIRUS II

CIH, also known as Chernobyl or Spacefiller, is a Microsoft Windows 9x computer virus that first emerged in 1998. Its payload is highly destructive to vulnerable systems, overwriting critical information on infected system drives and, in some cases, destroying the system BIOS. The virus was created by Chen Ing-hau, a student at Tatung University in Taiwan. It was believed to have infected sixty million computers internationally, resulting in an estimated NT$1 billion (US$35,801,231.56) in commercial damages.
Elk Cloner is one of the first known microcomputer viruses that spread "in the wild", i.e., outside the computer system or laboratory in which it was written. It attached itself to the Apple II operating system and spread by floppy disk. It was written around 1982 by programmer and entrepreneur Rich Skrenta as a 15-year-old high school student, originally as a joke, and put onto a game disk.

A COM file is a type of simple executable file. On the Digital Equipment Corporation (DEC) VAX operating systems of the 1970s, .COM was used as a filename extension for text files containing commands to be issued to the operating system. With the introduction of Digital Research's CP/M, the type of files commonly associated with COM extension changed to that of executable files. This convention was later carried over to DOS. Even when complemented by the more general EXE file format for executables, the compact COM files remained viable and frequently used under DOS.
Abraxas, also known as Abraxas5, discovered in April 1993, is an encrypted, overwriting, file infecting computer virus which infects .COM and .EXE files, although it does not infect command.com. It does not become memory resident. Each time an infected file is executed, Abraxas infects the copy of dosshell.com located in the C:\DOS directory, as well as one EXE file in the current directory. Due to a bug in the virus, only the first EXE file in any directory is infected.
Acid is a computer virus which infects .COM and .EXE files including command.com. Each time an infected file is executed, Acid infects all of the .EXE files in the current directory. Later, if an infected file is executed, it infects the .COM files in the current directory. Programs infected with Acid will have had the first 792 bytes of the host program overwritten with Acid's own code. There will be no file length increase unless the original host program was smaller than 792 bytes, in which case it will become 792 bytes in length. The program's date and time in the DOS disk directory listing will not be altered.
Acme is a computer virus which infects MS-DOS EXE files. Each time an infected file is executed, Acme may infect an EXE in the current directory by creating a hidden 247 byte long read-only COM file with the same base name. Acme is a variant of Clonewar, a spawning virus. Acme is also perhaps a descendant of the small single-step infector Zeno, which is not to be confused with the Zeno programming language.
Norton AntiVirus is an anti-virus or anti-malware software product founded by Peter Norton, developed and distributed by Symantec since 1990 as part of its Norton family of computer security products. It uses signatures and heuristics to identify viruses. Other features included in it are e-mail spam filtering and phishing protection.
ABC, discovered in October 1992, is a memory-resident, file-infecting computer virus which infects EXE files and may alter both COM and EXE files. ABC activates on the 13th day of every month.
Jerusalem is a logic bomb DOS virus first detected at Hebrew University of Jerusalem, in October 1987. On infection, the Jerusalem virus becomes memory resident, and then infects every executable file run, except for COMMAND.COM. COM files grow by 1,813 bytes when infected by Jerusalem and are not re-infected. Executable files grow by 1,808 to 1,823 bytes each time they are infected, and are then re-infected each time the files are loaded until they are too large to load into memory. Some .EXE files are infected but do not grow because several overlays follow the genuine .EXE file in the same file. Sometimes .EXE files are incorrectly infected, causing the program to fail to run as soon as it is executed.
Scott's Valley [sic] is a computer virus, a member of the Slow virus family and distantly related to the Jerusalem virus family. It was discovered in September 1990 in Scotts Valley, California.
Alabama is a computer virus, discovered in October 1989 on the campus of the Hebrew University of Jerusalem.
Ontario is a family of computer viruses, named after its point of isolation, the Canadian province of Ontario. This family of computer virus consists of Ontario.1024, Ontario.512 and Ontario.2048. The first variant Ontario.512 was discovered in July 1990. Because Ontario.1024 was also discovered in Ontario, it is likely that both viruses originate from within the province. By the Ontario.2048 variant, the author had adopted "Ontario" as the family's name and even included the name "Ontario-3" in the virus code.
CTX is a computer virus created in Spain in 1999. CTX was initially discovered as part of the Cholera worm, with which the author intentionally infected with CTX. Although the Cholera worm had the capability to send itself via email, the CTX worm quickly surpassed it in prevalence. Cholera is now considered obsolete, while CTX remains in the field, albeit with only rare discoveries.
The Vundo Trojan is either a Trojan horse or a computer worm that is known to cause popups and advertising for rogue antispyware programs, and sporadically other misbehavior including performance degradation and denial of service with some websites including Google and Facebook. It also is used to deliver other malware to its host computers. Later versions include rootkits and ransomware.
ExploreZip is a destructive computer worm that attacks machines running Microsoft Windows. It was first discovered in Israel on June 6, 1999. The worm contains a malicious payload, and utilizes Microsoft Outlook, Outlook Express, or Exchange to mail itself out by replying to unread messages in the user's inbox. The worm also searches mapped drives and networked computers for Windows installations. If found, it copies itself to the Windows folder of the remote computer and then modifies the Win.ini file of the infected computer. On January 8, 2003, Symantec discovered a packed variant of this threat which exhibits the same characteristics.
5lo is a computer virus that increases file size and does little more than replicate. Size: 1,032 bytes
A batch file is a script file in DOS, OS/2 and Microsoft Windows. It consists of a series of commands to be executed by the command-line interpreter, stored in a plain text file. A batch file may contain any command the interpreter accepts interactively and use constructs that enable conditional branching and looping within the batch file, such as IF, FOR, and GOTO labels. The term "batch" is from batch processing, meaning "non-interactive execution", though a batch file might not process a batch of multiple data.
KoKo Virus is a memory resident computer virus created in March 1991. KoKo's name came from the creator himself, which was a nickname used by his friends. Many on-line virus databases refer to KoKo as Koko.1780. KoKo is written in the Assembly programming language and the executable file usually has an approximate file size of around 1780 bytes.
Virdem was the first file virus for MS-DOS. It was written by Ralf Burger in 1986 as a demonstration program for the Chaos Computer Club conference. The virus spread by attaching itself to files with the .COM file extension. It is one of the oldest MS-DOS viruses.
| External videos | |
|---|---|