The Common Language Infrastructure (CLI) is an open specification and technical standard originally developed by Microsoft and standardized by ISO/IEC and Ecma International that describes executable code and a runtime environment that allows multiple high-level languages to be used on different computer platforms without being rewritten for specific architectures. This implies it is platform agnostic. The .NET Framework, .NET and Mono are implementations of the CLI. The metadata format is also used to specify the API definitions exposed by the Windows Runtime.
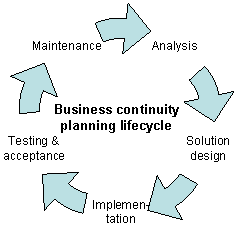
Business continuity may be defined as "the capability of an organization to continue the delivery of products or services at pre-defined acceptable levels following a disruptive incident", and business continuity planning is the process of creating systems of prevention and recovery to deal with potential threats to a company. In addition to prevention, the goal is to enable ongoing operations before and during execution of disaster recovery. Business continuity is the intended outcome of proper execution of both business continuity planning and disaster recovery.
The Organization for the Advancement of Structured Information Standards is a nonprofit consortium that works on the development, convergence, and adoption of projects - both open standards and open source - for Computer security, blockchain, Internet of things (IoT), emergency management, cloud computing, legal data exchange, energy, content technologies, and other areas.
The C standard library, sometimes referred to as libc, is the standard library for the C programming language, as specified in the ISO C standard. Starting from the original ANSI C standard, it was developed at the same time as the C library POSIX specification, which is a superset of it. Since ANSI C was adopted by the International Organization for Standardization, the C standard library is also called the ISO C library.
IT disaster recovery (also, simply disaster recovery (DR)) is the process of maintaining or reestablishing vital infrastructure and systems following a natural or human-induced disaster, such as a storm or battle. DR employs policies, tools, and procedures with a focus on IT systems supporting critical business functions. This involves keeping all essential aspects of a business functioning despite significant disruptive events; it can therefore be considered a subset of business continuity (BC). DR assumes that the primary site is not immediately recoverable and restores data and services to a secondary site.
Information technology service management (ITSM) are the activities performed by an organization to design, build, deliver, operate and control IT services offered to customers.

The Trusted Computing Group is a group formed in 2003 as the successor to the Trusted Computing Platform Alliance which was previously formed in 1999 to implement Trusted Computing concepts across personal computers. Members include Intel, AMD, IBM, Microsoft, and Cisco.
Office Open XML is a zipped, XML-based file format developed by Microsoft for representing spreadsheets, charts, presentations and word processing documents. Ecma International standardized the initial version as ECMA-376. ISO and IEC standardized later versions as ISO/IEC 29500.
Information security standards are techniques generally outlined in published materials that attempt to protect a user's or organization's cyber environment. This environment includes users themselves, networks, devices, all software, processes, information in storage or transit, applications, services, and systems that can be connected directly or indirectly to networks.
The following article details governmental and other organizations from around the world who are in the process of evaluating the suitability of using (adopting) OpenDocument, an open document file format for saving and exchanging office documents that may be edited.
Software asset management (SAM) is a business practice that involves managing and optimizing the purchase, deployment, maintenance, utilization, and disposal of software applications within an organization. According to ITIL, SAM is defined as “…all of the infrastructure and processes necessary for the effective management, control, and protection of the software assets…throughout all stages of their lifecycle.” Fundamentally intended to be part of an organization's information technology business strategy, the goals of SAM are to reduce information technology (IT) costs and limit business and legal risk related to the ownership and use of software, while maximizing IT responsiveness and end-user productivity. SAM is particularly important for large corporations regarding redistribution of licenses and managing legal risks associated with software ownership and expiration. SAM technologies track license expiration, thus allowing the company to function ethically and within software compliance regulations. This can be important for both eliminating legal costs associated with license agreement violations and as part of a company's reputation management strategy. Both are important forms of risk management and are critical for large corporations' long-term business strategies.
Security controls or security measures are safeguards or countermeasures to avoid, detect, counteract, or minimize security risks to physical property, information, computer systems, or other assets. In the field of information security, such controls protect the confidentiality, integrity and availability of information.
Information technology risk, IT risk, IT-related risk, or cyber risk is any risk relating to information technology. While information has long been appreciated as a valuable and important asset, the rise of the knowledge economy and the Digital Revolution has led to organizations becoming increasingly dependent on information, information processing and especially IT. Various events or incidents that compromise IT in some way can therefore cause adverse impacts on the organization's business processes or mission, ranging from inconsequential to catastrophic in scale.
The Office Open XML file formats, also known as OOXML, were standardised between December 2006 and November 2008, first by the Ecma International consortium, and subsequently, after a contentious standardization process, by the ISO/IEC's Joint Technical Committee 1.

The .NET Framework is a proprietary software framework developed by Microsoft that runs primarily on Microsoft Windows. It was the predominant implementation of the Common Language Infrastructure (CLI) until being superseded by the cross-platform .NET project. It includes a large class library called Framework Class Library (FCL) and provides language interoperability across several programming languages. Programs written for .NET Framework execute in a software environment named the Common Language Runtime (CLR). The CLR is an application virtual machine that provides services such as security, memory management, and exception handling. As such, computer code written using .NET Framework is called "managed code". FCL and CLR together constitute the .NET Framework.
HITRUST is a privately held for-profit company located in Frisco, Texas, United States. It is solely owned by Daniel S. Nutkis who is the President and CEO. HITRUST in collaboration with healthcare, technology and information security organizations, established the HITRUST CSF. The company claims CSF is a comprehensive, prescriptive, and certifiable framework, that can be used by all organizations that create, access, store or exchange sensitive and/or regulated data.
Long-term support (LTS) is a product lifecycle management policy in which a stable release of computer software is maintained for a longer period of time than the standard edition. The term is typically reserved for open-source software, where it describes a software edition that is supported for months or years longer than the software's standard edition.
ISO/IEC JTC 1/SC 29, entitled Coding of audio, picture, multimedia and hypermedia information, is a standardization subcommittee of the Joint Technical Committee ISO/IEC JTC 1 of the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It develops and facilitates international standards, technical reports, and technical specifications within the field of audio, picture, multimedia, and hypermedia information coding. SC 29 includes the well-known JPEG and MPEG experts groups, and the standards developed by SC 29 have been recognized by nine Emmy Awards.

ISO/TC 292 Security and resilience is a technical committee of the International Organization for Standardization formed in 2015 to develop standards in the area of security and resilience.
ISO 22301:2019, Security and resilience – Business continuity management systems – Requirements, is a management system standard published by International Organization for Standardization that specifies requirements to plan, establish, implement, operate, monitor, review, maintain and continually improve a documented management system to protect against, reduce the likelihood of occurrence, prepare for, respond to, and recover from disruptive incidents when they arise. It is intended to be applicable to all organizations, or parts thereof, regardless of type, size and nature of the organization.


