Wiretapping, also known as wire tapping or telephone tapping, is the monitoring of telephone and Internet-based conversations by a third party, often by covert means. The wire tap received its name because, historically, the monitoring connection was an actual electrical tap on an analog telephone or telegraph line. Legal wiretapping by a government agency is also called lawful interception. Passive wiretapping monitors or records the traffic, while active wiretapping alters or otherwise affects it.
Computer and network surveillance is the monitoring of computer activity and data stored locally on a computer or data being transferred over computer networks such as the Internet. This monitoring is often carried out covertly and may be completed by governments, corporations, criminal organizations, or individuals. It may or may not be legal and may or may not require authorization from a court or other independent government agencies. Computer and network surveillance programs are widespread today and almost all Internet traffic can be monitored.

Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizations, but it may also be carried out by corporations. Depending on each nation's laws and judicial systems, the legality of and the permission required to engage in mass surveillance varies. It is the single most indicative distinguishing trait of totalitarian regimes. It is often distinguished from targeted surveillance.
The Communications Assistance for Law Enforcement Act (CALEA), also known as the "Digital Telephony Act," is a United States wiretapping law passed in 1994, during the presidency of Bill Clinton.

Carnivore, later renamed DCS1000, was a system implemented by the Federal Bureau of Investigation (FBI) that was designed to monitor email and electronic communications. It used a customizable packet sniffer that could monitor all of a target user's Internet traffic. Carnivore was implemented in October 1997. By 2005 it had been replaced with improved commercial software.
Lawful interception (LI) refers to the facilities in telecommunications and telephone networks that allow law enforcement agencies with court orders or other legal authorization to selectively wiretap individual subscribers. Most countries require licensed telecommunications operators to provide their networks with Legal Interception gateways and nodes for the interception of communications. The interfaces of these gateways have been standardized by telecommunication standardization organizations. As with many law enforcement tools, LI systems may be subverted for illicit purposes.
The System for Operative Investigative Activities is the technical specification for lawful interception interfaces of telecommunications and telephone networks operating in Russia. The current form of the specification enables the targeted surveillance of both telephone and Internet communications. Initially implemented in 1995 to allow access to surveillance data for the FSB, in subsequent years the access has been widened to other law enforcement agencies.

MAINWAY is a database maintained by the United States' National Security Agency (NSA) containing metadata for hundreds of billions of telephone calls made through the largest telephone carriers in the United States, including AT&T, Verizon, and T-Mobile.

The Digital Collection System Network (DCSNet) is the Federal Bureau of Investigation (FBI)'s point-and-click surveillance system that can perform instant wiretaps on almost any telecommunications device in the United States.

"Stellar Wind" was the code name of a warrantless surveillance program begun under the George W. Bush administration's President's Surveillance Program (PSP). The National Security Agency (NSA) program was approved by President Bush shortly after the September 11, 2001 attacks and was revealed by Thomas Tamm to The New York Times in 2004. Stellar Wind was a prelude to new legal structures that allowed President Bush and President Barack Obama to reproduce each of those programs and expand their reach.

The Office of Tailored Access Operations (TAO), now Computer Network Operations, and structured as S32, is a cyber-warfare intelligence-gathering unit of the National Security Agency (NSA). It has been active since at least 1998, possibly 1997, but was not named or structured as TAO until "the last days of 2000," according to General Michael Hayden.

PRISM is a code name for a program under which the United States National Security Agency (NSA) collects internet communications from various U.S. internet companies. The program is also known by the SIGAD US-984XN. PRISM collects stored internet communications based on demands made to internet companies such as Google LLC and Apple under Section 702 of the FISA Amendments Act of 2008 to turn over any data that match court-approved search terms. Among other things, the NSA can use these PRISM requests to target communications that were encrypted when they traveled across the internet backbone, to focus on stored data that telecommunication filtering systems discarded earlier, and to get data that is easier to handle.

XKeyscore is a secret computer system used by the United States National Security Agency (NSA) for searching and analyzing global Internet data, which it collects in real time. The NSA has shared XKeyscore with other intelligence agencies, including the Australian Signals Directorate, Canada's Communications Security Establishment, New Zealand's Government Communications Security Bureau, Britain's Government Communications Headquarters, Japan's Defense Intelligence Headquarters, and Germany's Bundesnachrichtendienst.

The practice of mass surveillance in the United States dates back to wartime monitoring and censorship of international communications from, to, or which passed through the United States. After the First and Second World Wars, mass surveillance continued throughout the Cold War period, via programs such as the Black Chamber and Project SHAMROCK. The formation and growth of federal law-enforcement and intelligence agencies such as the FBI, CIA, and NSA institutionalized surveillance used to also silence political dissent, as evidenced by COINTELPRO projects which targeted various organizations and individuals. During the Civil Rights Movement era, many individuals put under surveillance orders were first labelled as integrationists, then deemed subversive, and sometimes suspected to be supportive of the communist model of the United States' rival at the time, the Soviet Union. Other targeted individuals and groups included Native American activists, African American and Chicano liberation movement activists, and anti-war protesters.

During the 2010s, international media reports revealed new operational details about the Anglophone cryptographic agencies' global surveillance of both foreign and domestic nationals. The reports mostly relate to top secret documents leaked by ex-NSA contractor Edward Snowden. The documents consist of intelligence files relating to the U.S. and other Five Eyes countries. In June 2013, the first of Snowden's documents were published, with further selected documents released to various news outlets through the year.
This is a category of disclosures related to global surveillance.

Global mass surveillance can be defined as the mass surveillance of entire populations across national borders.

This timeline of global surveillance disclosures from 2013 to the present day is a chronological list of the global surveillance disclosures that began in 2013. The disclosures have been largely instigated by revelations from the former American National Security Agency contractor Edward Snowden.
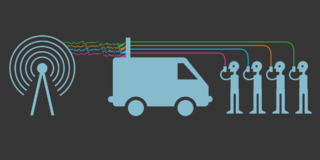
Cellphone surveillance may involve tracking, bugging, monitoring, eavesdropping, and recording conversations and text messages on mobile phones. It also encompasses the monitoring of people's movements, which can be tracked using mobile phone signals when phones are turned on.







