Related Research Articles

The Advanced Encryption Standard (AES), also known by its original name Rijndael, is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001.

The Data Encryption Standard is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits makes it too insecure for modern applications, it has been highly influential in the advancement of cryptography.
Elliptic-curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. ECC allows smaller keys compared to non-EC cryptography to provide equivalent security.

The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA has the task of globally monitoring, collecting, and processing information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in the discipline of signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and of information systems. The NSA relies on a variety of methods to accomplish its mission, the majority of which are clandestine. The NSA has roughly 32,000 employees.
Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. Phil Zimmermann developed PGP in 1991.
A cypherpunk is any individual advocating widespread use of strong cryptography and privacy-enhancing technologies as a route to social and political change. Originally communicating through the Cypherpunks electronic mailing list, informal groups aimed to achieve privacy and security through proactive use of cryptography. Cypherpunks have been engaged in an active movement since at least the late 1980s.

A secure cryptoprocessor is a dedicated computer-on-a-chip or microprocessor for carrying out cryptographic operations, embedded in a packaging with multiple physical security measures, which give it a degree of tamper resistance. Unlike cryptographic processors that output decrypted data onto a bus in a secure environment, a secure cryptoprocessor does not output decrypted data or decrypted program instructions in an environment where security cannot always be maintained.
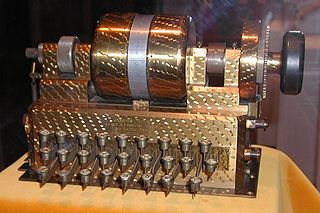
The Hebern Rotor Machine was an electro-mechanical encryption machine built by combining the mechanical parts of a standard typewriter with the electrical parts of an electric typewriter, connecting the two through a scrambler. It is the first example of a class of machines known as rotor machines that would become the primary form of encryption during World War II and for some time after, and which included such famous examples as the German Enigma.
Articles related to cryptography include:

RSA Security LLC, formerly RSA Security, Inc. and trade name RSA, is an American computer and network security company with a focus on encryption and encryption standards. RSA was named after the initials of its co-founders, Ron Rivest, Adi Shamir and Leonard Adleman, after whom the RSA public key cryptography algorithm was also named. Among its products is the SecurID authentication token. The BSAFE cryptography libraries were also initially owned by RSA. RSA is known for incorporating backdoors developed by the NSA in its products. It also organizes the annual RSA Conference, an information security conference.

Kryptos is a distributed sculpture by the American artist Jim Sanborn located on the grounds of the Central Intelligence Agency (CIA) headquarters, the George Bush Center for Intelligence in Langley, Virginia. Since its dedication on November 3, 1990, there has been much speculation about the meaning of the four encrypted messages it bears. Of these four messages, the first three have been solved, while the fourth message remains one of the most famous unsolved codes in the world. The sculpture continues to be of interest to cryptanalysts, both amateur and professional, who are attempting to decipher the fourth passage. The artist has so far given four clues to this passage.
Herbert James Sanborn, Jr. is an American sculptor. He is best known for creating the encrypted Kryptos sculpture at CIA headquarters in Langley, Virginia.
CCM mode is a mode of operation for cryptographic block ciphers. It is an authenticated encryption algorithm designed to provide both authentication and confidentiality. CCM mode is only defined for block ciphers with a block length of 128 bits.
Below is a timeline of notable events related to cryptography.

Kim Zetter is an American investigative journalist and author who has covered cybersecurity and national security since 1999. She has broken numerous stories over the years about NSA surveillance, WikiLeaks, and the hacker underground, including an award-winning series about the security problems with electronic voting machines. She has three times been voted one of the top ten security journalists in the U.S. by her journalism peers and security professionals. She is considered one of the world's experts on Stuxnet, a malicious computer worm used to sabotage Iran's nuclear program, and published a book on the topic called Countdown to Zero Day: Stuxnet and the Launch of the World's First Digital Weapon.
James J. Gillogly is an American computer scientist and cryptographer.
The Cyrillic Projector is a sculpture created by American artist Jim Sanborn in the early 1990s, and purchased by the University of North Carolina at Charlotte in 1997. It is currently installed between the campus's Friday and Fretwell Buildings.

Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications.

The George Bush Center for Intelligence is the headquarters of the Central Intelligence Agency, located in the unincorporated community of Langley in Fairfax County, Virginia, United States, near Washington, D.C.

Elonka Dunin is an American video game developer and cryptologist. Dunin worked at Simutronics Corp. in St. Louis, Missouri from 1990–2014, and in 2015 was Senior Producer at Black Gate Games in Nashville, Tennessee. She is Chairperson Emerita and one of the founders of the International Game Developers Association's Online Games group, has contributed or been editor in chief on multiple IGDA State of the Industry white papers, and was one of the Directors of the Global Game Jam from 2011–2014. As of 2020 she works as a management consultant at Accenture.
References
- 1 2 "California Birth Index" . Retrieved 2023-07-21.
- 1 2 3 "Mary J. Shope, Edward Scheidt Exchange Vows". Altoona Mirror. Altoona, PA. July 5, 1974. p. 18.
- ↑ "First Child Born To Edward Scheidts". Altoona Mirror. Altoona, PA. July 24, 1975. p. 26.
- ↑ "H Obituaries Orleans Parish Louisiana". USGenWeb Archives. Retrieved 2023-07-18.
- ↑ "Edward Scheidt". MyHeritage. Retrieved 2023-07-18.
- 1 2 Schaeffer, Jonathan (2008). One Jump Ahead (2nd ed.). Springer. p. 178. ISBN 9780387765761 . Retrieved 16 August 2021.
Note: This source incorrectly identifies Edward M. Scheidt's father as FBI agent Edward F. Scheidt. The correct information is given in the other references.
- ↑ Different sources cite different middle names. See Altoona Mirror (Michael) and California Birth Index (Micheal).
- ↑ "Even the Teacher Can't Decipher It". Crimson Shield. October 2010. Retrieved 2023-07-21.
- 1 2 "The People of the CIA: Edward Scheidt". Central Intelligence Agency. 2008. Archived from the original on 2009-01-14. Retrieved May 23, 2011.
- ↑ Department of State Newsletter. 1963. p. 63. Retrieved 2023-07-18.
- ↑ Department of State Newsletter. 1966. p. 63. Retrieved 2023-07-18.
- ↑ Department of State Newsletter. 1967. p. 62. Retrieved 2023-07-18.
- ↑ Department of State Newsletter. 1968. p. 55. Retrieved 2023-07-18.
- ↑ Department of State Newsletter. 1971. p. 78. Retrieved 2023-07-18.
- ↑ Department of State Newsletter. 1973. p. 63. Retrieved 2023-07-18.
- ↑ Department of State Newsletter. 1978. p. 45. Retrieved 2023-07-18.
- ↑ Department of State Newsletter. 1980. p. 29. Retrieved 2023-07-18.
- ↑ Foreign Service Classification List. Department of State. 1978. p. 38. Retrieved 2023-07-18.
- ↑ "Cracking the Code of a CIA Sculpture", John Schwartz, July 19, 1999, Page A01, Washington Post
- ↑ "Interest grows in solving cryptic CIA puzzle after link toDa Vinci Code", June 11, 2005, The Guardian , by Julian Borger
- ↑ "Inside Info on Kryptos Codes, January 21, 2005, Wired News
- ↑ "Solving the Enigma of Kryptos", January 26, 2005, Wired News , by Kim Zetter
- ↑ "Sanborn: 'Kryptos' sculpture was 'an obsession'", June 21, 2005, CNN
- ↑ "A Break for Code-Breakers on a C.I.A. Mystery", April 22, 2006, The New York Times
- ↑ Gertz, Bill (8 April 1991). "Cryptic sculpture spooks CIA employees". Washington Times.
Mr. Sanborn told the AP the message was written by a retired CIA cryptographer, which would seem to rule out Mr. Clancy. The sculptor and the Deep Throat of codes conducted business only at secret locations, never by telephone or in writing.
- ↑ Wilson, John (2009-02-02). "Kryptos hints". Archived from the original on 2009-02-02. Retrieved 2023-07-21.
Note: The source refers to notes from Elonka Dunin in 2003.
{{cite web}}: CS1 maint: bot: original URL status unknown (link) - ↑ "TecSec About". Archived from the original on 2015-04-21. Retrieved 16 August 2021.
- ↑ "X9 Seeks Participants for New Research into Bank-held Crypto Asset Risks" (Press release). 2023-03-08. Retrieved 2023-07-18.
- ↑ "Google Patents" . Retrieved 2023-07-18.
- ↑ "Encryption vendor files patent lawsuit against tech giants". ComputerWorld Inc. 9 February 2010. Retrieved 9 February 2010.
- ↑ Scott Graham (2019-06-21). "Latham whittles long running patent case down to zero" . Retrieved 2023-07-18.
- ↑ "Public Key Cryptography for the Financial Services Industry—The Elliptic Curve Digital Signature Algorithm" (PDF). Retrieved 12 November 2020.
- ↑ "ISO/TC 68/SC 2 Financial Services, security" . Retrieved 12 November 2020.
- ↑ "The Virginia Knights of Columbus Ecumenical Chalice" (PDF). Knights of Columbus. 2001. Archived from the original (PDF) on 2023-02-04. Retrieved 2023-07-18.