
Computer memory stores information, such as data and programs, for immediate use in the computer. The term memory is often synonymous with the terms RAM,main memory, or primary storage. Archaic synonyms for main memory include core and store.

The Microvision is the first handheld game console that used interchangeable cartridges and in that sense is reprogrammable. It was released by the Milton Bradley Company in November 1979 for a retail price of $49.99, equivalent to $212.00 in 2023.
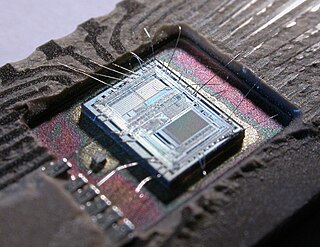
A microcontroller or microcontroller unit (MCU) is a small computer on a single integrated circuit. A microcontroller contains one or more CPUs along with memory and programmable input/output peripherals. Program memory in the form of NOR flash, OTP ROM, or ferroelectric RAM is also often included on the chip, as well as a small amount of RAM. Microcontrollers are designed for embedded applications, in contrast to the microprocessors used in personal computers or other general-purpose applications consisting of various discrete chips.

In microelectronics, a dual in-line package is an electronic component package with a rectangular housing and two parallel rows of electrical connecting pins. The package may be through-hole mounted to a printed circuit board (PCB) or inserted in a socket. The dual-inline format was invented by Don Forbes, Rex Rice and Bryant Rogers at Fairchild R&D in 1964, when the restricted number of leads available on circular transistor-style packages became a limitation in the use of integrated circuits. Increasingly complex circuits required more signal and power supply leads ; eventually microprocessors and similar complex devices required more leads than could be put on a DIP package, leading to development of higher-density chip carriers. Furthermore, square and rectangular packages made it easier to route printed-circuit traces beneath the packages.

The Intel 8085 ("eighty-eighty-five") is an 8-bit microprocessor produced by Intel and introduced in March 1976. It is the last 8-bit microprocessor developed by Intel.

The KIM-1, short for Keyboard Input Monitor, is a small 6502-based single-board computer developed and produced by MOS Technology, Inc. and launched in 1976. It was very successful in that period, due to its low price and easy-access expandability.

The MSP430 is a mixed-signal microcontroller family from Texas Instruments, first introduced on 14 February 1992. Built around a 16-bit CPU, the MSP430 was designed for low power consumption, embedded applications and low cost.
In-circuit emulation (ICE) is the use of a hardware device or in-circuit emulator used to debug the software of an embedded system. It operates by using a processor with the additional ability to support debugging operations, as well as to carry out the main function of the system. Particularly for older systems, with limited processors, this usually involved replacing the processor temporarily with a hardware emulator: a more powerful although more expensive version. It was historically in the form of bond-out processor which has many internal signals brought out for the purpose of debugging. These signals provide information about the state of the processor.
JTAG is an industry standard for verifying designs of and testing printed circuit boards after manufacture.

A security token is a peripheral device used to gain access to an electronically restricted resource. The token is used in addition to, or in place of, a password. Examples of security tokens include wireless key cards used to open locked doors, a banking token used as a digital authenticator for signing in to online banking, or signing transactions such as wire transfers.

The Fairchild F8 is an 8-bit microprocessor system from Fairchild Semiconductor, announced in 1974 and shipped in 1975. The original processor family includes four main 40-pin integrated circuits (ICs); the 3850 CPU which is the arithmetic logic unit, the 3851 Program Storage Unit (PSU) which contains 1 KB of program ROM and handles instruction decoding, and the optional 3852 Dynamic Memory Interface (DMI) or 3853 Static Memory Interface (SMI) to control additional RAM or ROM holding the user programs or data. The 3854 DMA is another optional system that adds direct memory access into the RAM controlled by the 3852.

A mobile phone feature is a capability, service, or application that a mobile phone offers to its users. Mobile phones are often referred to as feature phones, and offer basic telephony. Handsets with more advanced computing ability through the use of native code try to differentiate their own products by implementing additional functions to make them more attractive to consumers. This has led to great innovation in mobile phone development over the past 20 years.

A keypad is a block or pad of buttons set with an arrangement of digits, symbols, or alphabetical letters. Pads mostly containing numbers and used with computers are numeric keypads. Keypads are found on devices which require mainly numeric input such as calculators, television remotes, push-button telephones, vending machines, ATMs, point of sale terminals, combination locks, safes, and digital door locks. Many devices follow the E.161 standard for their arrangement.
A card reader is a data input device that reads data from a card-shaped storage medium and provides the data to a computer. Card readers can acquire data from a card via a number of methods, including: optical scanning of printed text or barcodes or holes on punched cards, electrical signals from connections made or interrupted by a card's punched holes or embedded circuitry, or electronic devices that can read plastic cards embedded with either a magnetic strip, computer chip, RFID chip, or another storage medium.
A contactless smart card is a contactless credential whose dimensions are credit card size. Its embedded integrated circuits can store data and communicate with a terminal via NFC. Commonplace uses include transit tickets, bank cards and passports.

Tamperproofing is a methodology used to hinder, deter or detect unauthorised access to a device or circumvention of a security system. Since any device or system can be foiled by a person with sufficient knowledge, equipment, and time, the term "tamperproof" is a misnomer unless some limitations on the tampering party's resources is explicit or assumed.
The maximum random access memory (RAM) installed in any computer system is limited by hardware, software and economic factors. The hardware may have a limited number of address bus bits, limited by the processor package or design of the system. Some of the address space may be shared between RAM, peripherals, and read-only memory. In the case of a microcontroller with no external RAM, the size of the RAM array is limited by the size of the integrated circuit die. In a packaged system, only enough RAM may be provided for the system's required functions, with no provision for addition of memory after manufacture.
Each time Intel launched a new microprocessor, they simultaneously provided a system development kit (SDK) allowing engineers, university students, and others to familiarise themselves with the new processor's concepts and features. The SDK single-board computers allowed the user to enter object code from a keyboard or upload it through a communication port, and then test run the code. The SDK boards provided a system monitor ROM to operate the keyboard and other interfaces. Kits varied in their specific features but generally offered optional memory and interface configurations, a serial terminal link, audio cassette storage, and EPROM program memory. Intel's Intellec development system could download code to the SDK boards.

A push-button telephone is a telephone that has buttons or keys for dialing a telephone number, in contrast to a rotary dial used in earlier telephones.

In electronics, a chip carrier is one of several kinds of surface-mount technology packages for integrated circuits. Connections are made on all four edges of a square package; compared to the internal cavity for mounting the integrated circuit, the package overall size is large.














