Related Research Articles
Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. Phil Zimmermann developed PGP in 1991.
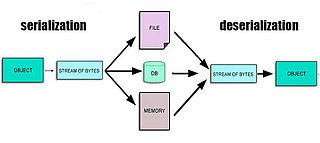
In computing, serialization is the process of translating a data structure or object state into a format that can be stored or transmitted and reconstructed later. When the resulting series of bits is reread according to the serialization format, it can be used to create a semantically identical clone of the original object. For many complex objects, such as those that make extensive use of references, this process is not straightforward. Serialization of objects does not include any of their associated methods with which they were previously linked.
Abstract Syntax Notation One (ASN.1) is a standard interface description language (IDL) for defining data structures that can be serialized and deserialized in a cross-platform way. It is broadly used in telecommunications and computer networking, and especially in cryptography.
vCard, also known as VCF, is a file format standard for electronic business cards. vCards can be attached to e-mail messages, sent via Multimedia Messaging Service (MMS), on the World Wide Web, instant messaging, NFC or through QR code. They can contain name and address information, phone numbers, e-mail addresses, URLs, logos, photographs, and audio clips.
JSON is an open standard file format and data interchange format that uses human-readable text to store and transmit data objects consisting of name–value pairs and arrays. It is a commonly used data format with diverse uses in electronic data interchange, including that of web applications with servers.
In computing, logging is the act of keeping a log of events that occur in a computer system, such as problems, errors or just information on current operations. These events may occur in the operating system or in other software. A message or log entry is recorded for each such event. These log messages can then be used to monitor and understand the operation of the system, to debug problems, or during an audit. Logging is particularly important in multi-user software, to have a central overview of the operation of the system.

WebFinger is a protocol specified by the Internet Engineering Task Force IETF in RFC 7033 that allows for discovery of information about people and things identified by a URI. Information about a person might be discovered via an acct: URI, for example, which is a URI that looks like an email address.
HTTP/2 is a major revision of the HTTP network protocol used by the World Wide Web. It was derived from the earlier experimental SPDY protocol, originally developed by Google. HTTP/2 was developed by the HTTP Working Group of the Internet Engineering Task Force (IETF). HTTP/2 is the first new version of HTTP since HTTP/1.1, which was standardized in RFC 2068 in 1997. The Working Group presented HTTP/2 to the Internet Engineering Steering Group (IESG) for consideration as a Proposed Standard in December 2014, and IESG approved it to publish as Proposed Standard on February 17, 2015. The initial HTTP/2 specification was published as on May 14, 2015.
WAMP is a WebSocket subprotocol registered at IANA, specified to offer routed RPC and PubSub. Its design goal is to provide an open standard for soft, real-time message exchange between application components and ease the creation of loosely coupled architectures based on microservices. Because of this, it is a suitable enterprise service bus (ESB), fit for developing responsive web applications or coordinating multiple connected IoT devices.
JSON Web Token is a proposed Internet standard for creating data with optional signature and/or optional encryption whose payload holds JSON that asserts some number of claims. The tokens are signed either using a private secret or a public/private key.
The Registration Data Access Protocol (RDAP) is a computer network communications protocol standardized by a working group at the Internet Engineering Task Force in 2015, after experimental developments and thorough discussions. It is a successor to the WHOIS protocol, used to look up relevant registration data from such Internet resources as domain names, IP addresses, and autonomous system numbers.
Web API security entails authenticating programs or users who are invoking a web API.

A well-known URI is a Uniform Resource Identifier for URL path prefixes that start with /.well-known/. They are implemented in webservers so that requests to the servers for well-known services or information are available at URLs consistent well-known locations across servers.
Token Binding is a proposed standard for a Transport Layer Security (TLS) extension that aims to increase TLS security by using cryptographic certificates on both ends of the TLS connection. Current practice often depends on bearer tokens, which may be lost or stolen. Bearer tokens are also vulnerable to man-in-the-middle attacks or replay attacks. In contrast, bound tokens are established by a user agent that generates a private-public key pair per target server, providing the public key to the server, and thereafter proving possession of the corresponding private key on every TLS connection to the server.
The Web Cryptography API is the World Wide Web Consortium’s (W3C) recommendation for a low-level interface that would increase the security of web applications by allowing them to perform cryptographic functions without having to access raw keying material. This agnostic API would perform basic cryptographic operations, such as hashing, signature generation and verification and encryption as well as decryption from within a web application.
JSON Web Encryption (JWE) is an IETF standard providing a standardised syntax for the exchange of encrypted data, based on JSON and Base64. It is defined by RFC 7516. Along with JSON Web Signature (JWS), it is one of the two possible formats of a JWT. JWE forms part of the JavaScript Object Signing and Encryption (JOSE) suite of protocols.
The JSON Meta Application Protocol (JMAP) is a set of related open Internet Standard protocols for handling email. JMAP is implemented using JSON APIs over HTTP and has been developed as an alternative to IMAP/SMTP and proprietary email APIs such as Google's Gmail and Microsoft's MAPI . Additional protocols and data models being built on top of the core of JMAP for handling contacts and calendar synchronization are meant to be potential replacements for CardDAV and CalDAV, and other support is currently in the works.
In computer security, macaroons are authorization credentials that support decentralized delegation between principals.
The Thing Description (TD) (or W3C WoT Thing Description (TD)) is a royalty-free, open information model with a JSON based representation format for the Internet of Things (IoT). A TD provides a unified way to describe the capabilities of an IoT device or service with its offered data model and functions, protocol usage, and further metadata. Using Thing Descriptions help reduce the complexity of integrating IoT devices and their capabilities into IoT applications.
In computing, a personal access token is a string of characters that can be used to authenticate a user when accessing a computer system instead of the usual password. Though associated with a single account, multiple PATs may be created, and can be manipulated independently of the password associated with that account, including creation and revocation of PATs without altering the password. The PAT is usually generated automatically by the remote system — for example, as a string of 52 alphanumeric characters. Typically, permissions may also be adjusted for each PAT individually, allowing or restricting access to certain classes of data or functions on the remote system. These permissions can usually be adjusted only after authenticating with the password. This can be a useful form of delegation of authorization, for example, when creating programs that will access the remote system. The PAT will typically be stored in a location accessible to the program, and therefore not typically as secure as a password. If the program or PAT is compromised, the damage will be limited by the permissions available to that PAT, and the PAT itself can easily be revoked to prevent further exploitation.
References
- ↑ Jones, Michael B.; Bradley, John; Sakimura, Nat (May 2015). "JSON Web Signature (JWS) [RFC7515]".
- ↑ Jones, Michael B.; Bradley, John; Sakimura, Nat (May 2015). "JWS Compact Serialization Overview".
- ↑ "JSON Object Signing and Encryption (JOSE)". Internet Assigned Numbers Authority. 2015-01-23. Retrieved 2018-11-19.
- ↑ Jones, Michael B.; Hildebrand, Joe (May 2015). "JSON Web Encryption (JWE) [RFC7516]". ietf.org. Retrieved 13 May 2015.
- ↑ Jones, Michael B. (May 2015). "JSON Web Key (JWK) [RFC7517]". ietf.org. Retrieved 13 May 2015.
- ↑ "google/google-oauth-java-client". GitHub. Retrieved 13 May 2015.
- ↑ "JSON Web Tokens - jwt.io". jwt.io. Retrieved 13 May 2015.