Implementation

The Critical Nodes application is a Free Open-Source implementation for the LASCNN algorithm. The application was developed in 2013 using Programming Without Coding Technology software. [8]
In graph theory, LASCNN is a Localized Algorithm for Segregation of Critical/Non-critical Nodes [1] The algorithm works on the principle of distinguishing between critical and non-critical nodes for network connectivity based on limited topology information. [2] The algorithm finds the critical nodes with partial information within a few hops. [3]
This algorithm can distinguish the critical nodes of the network with high precision, indeed, accuracy can reach 100% when identifying non-critical nodes. [4] The performance of LASCNN is scalable and quite competitive compared to other schemes. [5]
The LASCNN algorithm establishes a k-hop neighbor list and a duplicate free pair wise connection list based on k-hop information. If the neighbors stay connected then the node is non-critical. [6] [7]
Function LASCNN(MAHSN) For ∀ A ∈ MAHSN If (A->ConnList.getSize() == 1) then A->SetNonCritical() = LEAF Else Continue = TRUE While (Continue == TRUE) Continue = FALSE For ∀ ActiveConn ∈ ConnList If (A∉ActiveConn) then If (A->ConnNeighbors.getSize() == 0) A->ConnNeighbors.add(ActiveConn) Continue = TRUE else If (ActiveConn ∩ ConnNeighbors == TRUE) ActiveConn ∪ ConnNeighbors Continue = TRUE Endif Endif Endif End For End While Endif If (A->ConnNeighbors.getSize() < A->Neighbors.getSize()) A->SetCritical() = TRUE else A->SetNonCritical() = INTERMEDIATE Endif End For End Function

The Critical Nodes application is a Free Open-Source implementation for the LASCNN algorithm. The application was developed in 2013 using Programming Without Coding Technology software. [8]
In general, a node is a localized swelling or a point of intersection.
Link-state routing protocols are one of the two main classes of routing protocols used in packet switching networks for computer communications, the others being distance-vector routing protocols. Examples of link-state routing protocols include Open Shortest Path First (OSPF) and Intermediate System to Intermediate System (IS-IS).
Zigbee is an IEEE 802.15.4-based specification for a suite of high-level communication protocols used to create personal area networks with small, low-power digital radios, such as for home automation, medical device data collection, and other low-power low-bandwidth needs, designed for small scale projects which need wireless connection. Hence, Zigbee is a low-power, low-data-rate, and close proximity wireless ad hoc network.

A wireless mesh network (WMN) is a communications network made up of radio nodes organized in a mesh topology. It can also be a form of wireless ad hoc network.

A mesh network is a local area network topology in which the infrastructure nodes connect directly, dynamically and non-hierarchically to as many other nodes as possible and cooperate with one another to efficiently route data to and from clients.

The Optimized Link State Routing Protocol (OLSR) is an IP routing protocol optimized for mobile ad hoc networks, which can also be used on other wireless ad hoc networks. OLSR is a proactive link-state routing protocol, which uses hello and topology control (TC) messages to discover and then disseminate link state information throughout the mobile ad hoc network. Individual nodes use this topology information to compute next hop destinations for all nodes in the network using shortest hop forwarding paths.
Wireless sensor networks (WSNs) refer to networks of spatially dispersed and dedicated sensors that monitor and record the physical conditions of the environment and forward the collected data to a central location. WSNs can measure environmental conditions such as temperature, sound, pollution levels, humidity and wind.

In telecommunications, received signal strength indicator or received signal strength indication (RSSI) is a measurement of the power present in a received radio signal.
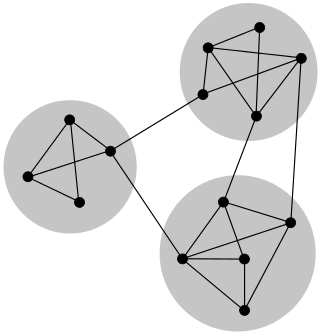
In mathematics and computer science, connectivity is one of the basic concepts of graph theory: it asks for the minimum number of elements that need to be removed to separate the remaining nodes into two or more isolated subgraphs. It is closely related to the theory of network flow problems. The connectivity of a graph is an important measure of its resilience as a network.
A wireless ad hoc network (WANET) or mobile ad hoc network (MANET) is a decentralized type of wireless network. The network is ad hoc because it does not rely on a pre-existing infrastructure, such as routers or wireless access points. Instead, each node participates in routing by forwarding data for other nodes. The determination of which nodes forward data is made dynamically on the basis of network connectivity and the routing algorithm in use.
Geographic routing is a routing principle that relies on geographic position information. It is mainly proposed for wireless networks and based on the idea that the source sends a message to the geographic location of the destination instead of using the network address. In the area of packet radio networks, the idea of using position information for routing was first proposed in the 1980s for interconnection networks. Geographic routing requires that each node can determine its own location and that the source is aware of the location of the destination. With this information, a message can be routed to the destination without knowledge of the network topology or a prior route discovery.
In distributed computing, leader election is the process of designating a single process as the organizer of some task distributed among several computers (nodes). Before the task has begun, all network nodes are either unaware which node will serve as the "leader" of the task, or unable to communicate with the current coordinator. After a leader election algorithm has been run, however, each node throughout the network recognizes a particular, unique node as the task leader.
Key distribution is an important issue in wireless sensor network (WSN) design. WSNs are networks of small, battery-powered, memory-constraint devices named sensor nodes, which have the capability of wireless communication over a restricted area. Due to memory and power constraints, they need to be well arranged to build a fully functional network.
Routing in delay-tolerant networking concerns itself with the ability to transport, or route, data from a source to a destination, which is a fundamental ability all communication networks must have. Delay- and disruption-tolerant networks (DTNs) are characterized by their lack of connectivity, resulting in a lack of instantaneous end-to-end paths. In these challenging environments, popular ad hoc routing protocols such as AODV and DSR fail to establish routes. This is due to these protocols trying to first establish a complete route and then, after the route has been established, forward the actual data. However, when instantaneous end-to-end paths are difficult or impossible to establish, routing protocols must take to a "store and forward" approach, where data is incrementally moved and stored throughout the network in hopes that it will eventually reach its destination. A common technique used to maximize the probability of a message being successfully transferred is to replicate many copies of the message in hopes that one will succeed in reaching its destination.
Reference Broadcast Synchronization (RBS) is a synchronization method in which the receiver uses the physical layer broadcasts for comparing the clocks. This slightly differs from traditional methods which synchronize the sender's with the receiver's clock.
Topology control is a technique used in distributed computing to alter the underlying network to reduce the cost of distributed algorithms if run over the resulting graphs. It is a basic technique in distributed algorithms. For instance, a (minimum) spanning tree is used as a backbone to reduce the cost of broadcast from O(m) to O(n), where m and n are the number of edges and vertices in the graph, respectively.

OCARI is a low-rate wireless personal area networks (LR-WPAN) communication protocol that derives from the IEEE 802.15.4 standard. It was developed by the following consortium during the OCARI project that is funded by the French National Research Agency (ANR):
Zebra Media Access Control (Z-MAC) is a network protocol for wireless sensor networks. It controls how a Media Access Control (MAC) accesses a common communication medium of a network.

KHOPCA is an adaptive clustering algorithm originally developed for dynamic networks. KHOPCA provides a fully distributed and localized approach to group elements such as nodes in a network according to their distance from each other. KHOPCA operates proactively through a simple set of rules that defines clusters, which are optimal with respect to the applied distance function.

Mahmoud Samir Fayed is a computer programmer, known as the creator of the PWCT programming language. PWCT is a free open source visual programming language for software development. He also created or designed Ring. He is a researcher at King Saud University. Prior to that, he worked at the Riyadh Techno Valley in the Information and Communication Technology Incubator.