Related Research Articles
E is a high-performance theorem prover for full first-order logic with equality. It is based on the equational superposition calculus and uses a purely equational paradigm. It has been integrated into other theorem provers and it has been among the best-placed systems in several theorem proving competitions. E is developed by Stephan Schulz, originally in the Automated Reasoning Group at TU Munich, now at Baden-Württemberg Cooperative State University Stuttgart.

GNUnet is a software framework for decentralized, peer-to-peer networking and an official GNU package. The framework offers link encryption, peer discovery, resource allocation, communication over many transports and various basic peer-to-peer algorithms for routing, multicast and network size estimation.

Code Co-op is the peer-to-peer revision control system made by Reliable Software.

In computer science, model checking or property checking is a method for checking whether a finite-state model of a system meets a given specification. This is typically associated with hardware or software systems, where the specification contains liveness requirements as well as safety requirements.

Graph drawing is an area of mathematics and computer science combining methods from geometric graph theory and information visualization to derive two-dimensional depictions of graphs arising from applications such as social network analysis, cartography, linguistics, and bioinformatics.
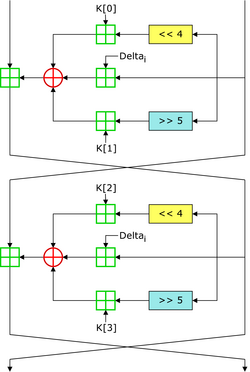
In cryptography, the Tiny Encryption Algorithm (TEA) is a block cipher notable for its simplicity of description and implementation, typically a few lines of code. It was designed by David Wheeler and Roger Needham of the Cambridge Computer Laboratory; it was first presented at the Fast Software Encryption workshop in Leuven in 1994, and first published in the proceedings of that workshop.
In cryptography, the eXtended Sparse Linearization (XSL) attack is a method of cryptanalysis for block ciphers. The attack was first published in 2002 by researchers Nicolas Courtois and Josef Pieprzyk. It has caused some controversy as it was claimed to have the potential to break the Advanced Encryption Standard (AES) cipher, also known as Rijndael, faster than an exhaustive search. Since AES is already widely used in commerce and government for the transmission of secret information, finding a technique that can shorten the amount of time it takes to retrieve the secret message without having the key could have wide implications.
ESC/Java, the "Extended Static Checker for Java," is a programming tool that attempts to find common run-time errors in Java programs at compile time. The underlying approach used in ESC/Java is referred to as extended static checking, which is a collective name referring to a range of techniques for statically checking the correctness of various program constraints. For example, that an integer variable is greater-than-zero, or lies between the bounds of an array. This technique was pioneered in ESC/Java and can be thought of as an extended form of type checking. Extended static checking usually involves the use of an automated theorem prover and, in ESC/Java, the Simplify theorem prover was used.
Provable security refers to any type or level of computer security that can be proved. It is used in different ways by different fields.
Bart Preneel is a Belgian cryptographer and cryptanalyst. He is a professor at Katholieke Universiteit Leuven, in the COSIC group.

Jonathan P. Bowen FBCS FRSA is a British computer scientist and an Emeritus Professor at London South Bank University, where he headed the Centre for Applied Formal Methods. Prof. Bowen is also the Chairman of Museophile Limited and an adjunct professor at Southwest University in Chongqing, China. He has been a Professor of Computer Science at Birmingham City University, Visiting Professor at the Pratt Institute, University of Westminster and King's College London, and a visiting academic at University College London.
SIMBAD is an astronomical database of objects beyond the Solar System. It is maintained by the Centre de données astronomiques de Strasbourg (CDS), France.
The B method is a method of software development based on B, a tool-supported formal method based on an abstract machine notation, used in the development of computer software.

Professor Dines Bjørner is a Danish computer scientist.

Egon Börger is a German-born computer scientist based in Italy.
Software visualization or software visualisation refers to the visualization of information of and related to software systems—either the architecture of its source code or metrics of their runtime behavior—and their development process by means of static, interactive or animated 2-D or 3-D visual representations of their structure, execution, behavior, and evolution.
StegFS is a free steganographic file system for Linux based on the ext2 filesystem. It is licensed under the GPL. It was principally developed by Andrew D. McDonald and Markus G. Kuhn, who developed versions 1.0.0 to 1.1.4.
Nix is a cross-platform package manager for Unix-like systems, and a tool to instantiate and manage those systems, invented in 2003 by Eelco Dolstra.
Douglas C. Schmidt is a computer scientist and author in the fields of object-oriented programming, reactive programming, distributed computing, design patterns and generative AI. He is the inaugural Dean of the School of Computing, Data Sciences & Physics at William & Mary.
PRESENT is a lightweight block cipher, developed by the Orange Labs (France), Ruhr University Bochum (Germany) and the Technical University of Denmark in 2007. PRESENT was designed by Andrey Bogdanov, Lars R. Knudsen, Gregor Leander, Christof Paar, Axel Poschmann, Matthew J. B. Robshaw, Yannick Seurin, and C. Vikkelsoe. The algorithm is notable for its compact size.
References
- ↑ Dolstra, E. (2003). "Integrating Software Construction and Software Deployment" (PDF). Software Configuration Management. ICSE Workshops SCM-11, Portland, OR, USA, May 9–10, 2003. LNCS. Vol. 2649. pp. 102–117. doi:10.1007/3-540-39195-9_8. ISBN 978-3-540-14036-8. ISSN 0302-9743.