
The Global System for Mobile Communications (GSM) is a standard developed by the European Telecommunications Standards Institute (ETSI) to describe the protocols for second-generation (2G) digital cellular networks used by mobile devices such as mobile phones and tablets. GSM is also a trade mark owned by the GSM Association. GSM may also refer to the Full Rate voice codec.
DEF CON is a hacker convention held annually in Las Vegas, Nevada. The first DEF CON took place in June 1993 and today many attendees at DEF CON include computer security professionals, journalists, lawyers, federal government employees, security researchers, students, and hackers with a general interest in software, computer architecture, hardware modification, conference badges, and anything else that can be "hacked". The event consists of several tracks of speakers about computer- and hacking-related subjects, as well as cyber-security challenges and competitions. Contests held during the event are extremely varied and can range from creating the longest Wi-Fi connection to finding the most effective way to cool a beer in the Nevada heat.

T-Mobile is the brand name used by some of the mobile communications subsidiaries of the German telecommunications company Deutsche Telekom AG in the Czech Republic, Poland and the United States.

A SIMcard is an integrated circuit (IC) intended to securely store an international mobile subscriber identity (IMSI) number and its related key, which are used to identify and authenticate subscribers on mobile telephone devices. Technically the actual physical card is known as a universal integrated circuit card (UICC); this smart card is usually made of PVC with embedded contacts and semiconductors, with the SIM as its primary component. In practice the term "SIM card" is still used to refer to the entire unit and not simply the IC.

Roaming is a wireless telecommunication term typically used with mobile devices, such as mobile phones. It refers to a mobile phone being used outside the range of its native network and connecting to another available cell network.

The base station subsystem (BSS) is the section of a traditional cellular telephone network which is responsible for handling traffic and signaling between a mobile phone and the network switching subsystem. The BSS carries out transcoding of speech channels, allocation of radio channels to mobile phones, paging, transmission and reception over the air interface and many other tasks related to the radio network.

A cellular network or mobile network is a telecommunications network where the link to and from end nodes is wireless and the network is distributed over land areas called cells, each served by at least one fixed-location transceiver. These base stations provide the cell with the network coverage which can be used for transmission of voice, data, and other types of content. A cell typically uses a different set of frequencies from neighboring cells, to avoid interference and provide guaranteed service quality within each cell.
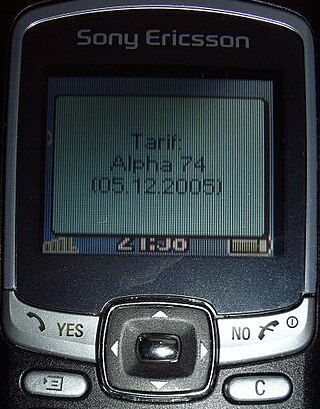
Unstructured Supplementary Service Data (USSD), sometimes referred to as "quick codes" or "feature codes", is a communications protocol used by GSM cellular telephones to communicate with the mobile network operator's computers. USSD can be used for WAP browsing, prepaid callback service, mobile-money services, location-based content services, menu-based information services, and as part of configuring the phone on the network. The service does not require a messaging app, and does not incur charges.
A microcell is a cell in a mobile phone network served by a low power cellular base station (tower), covering a limited area such as a mall, a hotel, or a transportation hub. A microcell is usually larger than a picocell, though the distinction is not always clear. A microcell uses power control to limit the radius of its coverage area.
An international mobile subscriber identity-catcher, or IMSI-catcher, is a telephone eavesdropping device used for intercepting mobile phone traffic and tracking location data of mobile phone users. Essentially a "fake" mobile tower acting between the target mobile phone and the service provider's real towers, it is considered a man-in-the-middle (MITM) attack. The 3G wireless standard offers some risk mitigation due to mutual authentication required from both the handset and the network. However, sophisticated attacks may be able to downgrade 3G and LTE to non-LTE network services which do not require mutual authentication.
A cellular repeater is a type of bi-directional amplifier used to improve cell phone reception. A cellular repeater system commonly consists of a donor antenna that receives and transmits signal from nearby cell towers, coaxial cables, a signal amplifier, and an indoor rebroadcast antenna.

Wi-Fi calling, also called VoWiFi, refers to mobile phone voice calls and data that are made over IP networks using Wi-Fi, instead of the cell towers provided by cellular networks. Using this feature, compatible handsets are able to route regular cellular calls through a wireless LAN (Wi-Fi) network with broadband Internet, while seamlessly change connections between the two where necessary. This feature makes use of the Generic Access Network (GAN) protocol, also known as Unlicensed Mobile Access (UMA).

In telecommunications, a femtocell is a small, low-power cellular base station, typically designed for use in a home or small business. A broader term which is more widespread in the industry is small cell, with femtocell as a subset. It typically connects to the service provider's network via the Internet through a wired broadband link ; current designs typically support four to eight simultaneously active mobile phones in a residential setting depending on version number and femtocell hardware, and eight to sixteen mobile phones in enterprise settings. A femtocell allows service providers to extend service coverage indoors or at the cell edge, especially where access would otherwise be limited or unavailable. Although much attention is focused on WCDMA, the concept is applicable to all standards, including GSM, CDMA2000, TD-SCDMA, WiMAX and LTE solutions.
Phone cloning is the copying of identity from one cellular device to another.

OpenBTS is a software-based GSM access point, allowing standard GSM-compatible mobile phones to be used as SIP endpoints in Voice over IP (VoIP) networks. OpenBTS is open-source software developed and maintained by Range Networks. The public release of OpenBTS is notable for being the first free-software implementation of the lower three layers of the industry-standard GSM protocol stack. It is written in C++ and released as free software under the terms of version 3 of the GNU Affero General Public License.

A computer security conference is a convention for individuals involved in computer security. They generally serve as meeting places for system and network administrators, hackers, and computer security experts.

Dave Buchwald, is a filmmaker and former phone phreak, hacker, and leader of the Legion of Doom in the mid-1980s, then known as Bill From RNOC.

ip.access Limited is a multinational corporation that designs, manufactures, and markets small cells technologies and infrastructure equipment for GSM, GPRS, EDGE, 3G, 4G and 5G. The company was acquired by Mavenir in September 2020.

The HTC One V is a smartphone designed and manufactured by HTC as part of the HTC One series which runs Android 4.0.3 with an HTC Sense 4.0 overlay. This phone is constructed from an aluminum unibody. Its design resembles the HTC Legend released in 2010. It features a 5-megapixel camera, 3.7-inch touchscreen, 512 MB RAM, a 1 GHz processor, and Beats audio. Officially announced by HTC on 26 February 2012, the HTC One V was released on 26 April 2012 in the UK.

Iftach Ian Amit is an Israeli Hacker/computer security researcher and practitioner. He is one of the co-founders of the Tel Aviv DEF CON Group DC9723, the Penetration Testing Execution Standard, and presented at hacker conventions such as DEF CON, Black Hat, BlueHat, RSA Conference. He has been named SC Magazine's top experts and featured at Narratively's cover piece on Attack of the Superhackers and is frequently quoted and interviewed



















