
An embedded system is a computer system—a combination of a computer processor, computer memory, and input/output peripheral devices—that has a dedicated function within a larger mechanical or electronic system. It is embedded as part of a complete device often including electrical or electronic hardware and mechanical parts. Because an embedded system typically controls physical operations of the machine that it is embedded within, it often has real-time computing constraints. Embedded systems control many devices in common use. In 2009, it was estimated that ninety-eight percent of all microprocessors manufactured were used in embedded systems.

A secure cryptoprocessor is a dedicated computer-on-a-chip or microprocessor for carrying out cryptographic operations, embedded in a packaging with multiple physical security measures, which give it a degree of tamper resistance. Unlike cryptographic processors that output decrypted data onto a bus in a secure environment, a secure cryptoprocessor does not output decrypted data or decrypted program instructions in an environment where security cannot always be maintained.

A smart card (SC), chip card, or integrated circuit card, is a card used to control access to a resource. It is typically a plastic credit card-sized card with an embedded integrated circuit (IC) chip. Many smart cards include a pattern of metal contacts to electrically connect to the internal chip. Others are contactless, and some are both. Smart cards can provide personal identification, authentication, data storage, and application processing. Applications include identification, financial, public transit, computer security, schools, and healthcare. Smart cards may provide strong security authentication for single sign-on (SSO) within organizations. Numerous nations have deployed smart cards throughout their populations.
The Common Scrambling Algorithm (CSA) is the encryption algorithm used in the DVB digital television broadcasting for encrypting video streams.
Pirate decryption is the decryption, or decoding, of pay TV or pay radio signals without permission from the original broadcaster. The term "pirate" is used in the sense of copyright infringement. The MPAA and other groups which lobby in favour of intellectual property regulations have labelled such decryption as "signal theft" even though there is no direct tangible loss on the part of the original broadcaster, arguing that losing out on a potential chance to profit from a consumer's subscription fees counts as a loss of actual profit.
Data security means protecting digital data, such as those in a database, from destructive forces and from the unwanted actions of unauthorized users, such as a cyberattack or a data breach.
Secure communication is when two entities are communicating and do not want a third party to listen in. For this to be the case, the entities need to communicate in a way that is unsusceptible to eavesdropping or interception. Secure communication includes means by which people can share information with varying degrees of certainty that third parties cannot intercept what is said. Other than spoken face-to-face communication with no possible eavesdropper, it is probable that no communication is guaranteed to be secure in this sense, although practical obstacles such as legislation, resources, technical issues, and the sheer volume of communication serve to limit surveillance.
VideoGuard, produced by NDS, is a digital encryption system for use with conditional access television broadcasting. It is used on digital satellite television systems - some of which are operated by News Corporation, which owned about half (49%) of NDS until its sale to Cisco in 2012. Since 2018 VideoGuard is improved and maintained by Synamedia. Its two most widely used implementations are Sky in the United Kingdom and Ireland and DirecTV in the United States, the former of which launched the digital version of the system in 1998.

VideoCipher is a brand name of analog scrambling and de-scrambling equipment for cable and satellite television invented primarily to enforce Television receive-only (TVRO) satellite equipment to only receive TV programming on a subscription basis.
Television encryption, often referred to as scrambling, is encryption used to control access to pay television services, usually cable, satellite, or Internet Protocol television (IPTV) services.
Conditional access (CA) is a term commonly used in relation to software and to digital television systems. Conditional access is that 'just-in-time' evaluation to ensure the person who is seeking access to content is authorized to access the content. Said another way, conditional access is a type of access management. Access is managed by requiring certain criteria to be met before granting access to the content.
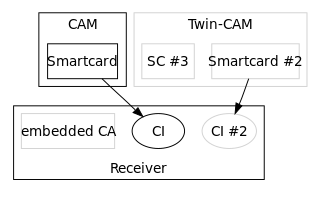
In Digital Video Broadcasting, the Common Interface is a technology which allows decryption of pay TV channels. Pay TV stations want to choose which encryption method to use. The Common Interface allows TV manufacturers to support many different pay TV stations, by allowing to plug in exchangeable conditional-access modules (CAM) for various encryption schemes.

VideoCrypt is a cryptographic, smartcard-based conditional access television encryption system that scrambles analogue pay-TV signals. It was introduced in 1989 by News Datacom and was used initially by Sky TV and subsequently by several other broadcasters on SES' Astra satellites at 19.2° east.
KeyFly is a conditional access (CA) system developed by SIDSA which is compatible with the DVB-CSA platform. The system is based on SIDSA MACtsp processors, and conditional-access modules for it can integrate the card directly into the CAM.

Tamperproofing, conceptually, is a methodology used to hinder, deter or detect unauthorised access to a device or circumvention of a security system. Since any device or system can be foiled by a person with sufficient knowledge, equipment, and time, the term "tamperproof" is a misnomer unless some limitations on the tampering party's resources is explicit or assumed.
Card sharing, also known as control word sharing, is a method of allowing multiple clients or digital television receivers to access a subscription television network with only one valid subscription card. This is achieved by electronically sharing a part of the legitimate conditional access smart card's output data, enabling all recipients to gain simultaneous access to scrambled DVB streams, held on the encrypted television network.
Multi-Choice TV (MCTV) is a television service provider in Barbados. It is a Multichannel Multipoint Distribution Service (MMDS) or DVB-C wireless microwave-based broadcast subscription television provider. They offer a variety of packages which can be considered as comparatively priced to similar providers throughout the world.

A free-to-air or FTA Receiver is a satellite television receiver designed to receive unencrypted broadcasts. Modern decoders are typically compliant with the MPEG-2/DVB-S and more recently the MPEG-4/DVB-S2 standard for digital television, while older FTA receivers relied on analog satellite transmissions which have declined rapidly in recent years.
Private biometrics is a form of encrypted biometrics, also called privacy-preserving biometric authentication methods, in which the biometric payload is a one-way, homomorphically encrypted feature vector that is 0.05% the size of the original biometric template and can be searched with full accuracy, speed and privacy. The feature vector's homomorphic encryption allows search and match to be conducted in polynomial time on an encrypted dataset and the search result is returned as an encrypted match. One or more computing devices may use an encrypted feature vector to verify an individual person or identify an individual in a datastore without storing, sending or receiving plaintext biometric data within or between computing devices or any other entity. The purpose of private biometrics is to allow a person to be identified or authenticated while guaranteeing individual privacy and fundamental human rights by only operating on biometric data in the encrypted space. Some private biometrics including fingerprint authentication methods, face authentication methods, and identity-matching algorithms according to bodily features. Private biometrics are constantly evolving based on the changing nature of privacy needs, identity theft, and biotechnology.
LastPass is a password manager application. The standard version of LastPass comes with a web interface, but also includes plugins for various web browsers and apps for many smartphones. It also includes support for bookmarklets.







