A broadcast domain is a logical division of a computer network, in which all nodes can reach each other by broadcast at the data link layer. A broadcast domain can be within the same LAN segment or it can be bridged to other LAN segments.
A network switch is networking hardware that connects devices on a computer network by using packet switching to receive and forward data to the destination device.
Proxy ARP is a technique by which a proxy server on a given network answers the Address Resolution Protocol (ARP) queries for an IP address that is not on that network. The proxy is aware of the location of the traffic's destination and offers its own MAC address as the destination. The traffic directed to the proxy address is then typically routed by the proxy to the intended destination via another interface or via a tunnel.
The Spanning Tree Protocol (STP) is a network protocol that builds a loop-free logical topology for Ethernet networks. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree also allows a network design to include backup links providing fault tolerance if an active link fails.
A virtual local area network (VLAN) is any broadcast domain that is partitioned and isolated in a computer network at the data link layer. In this context, virtual refers to a physical object recreated and altered by additional logic, within the local area network. VLANs work by applying tags to network frames and handling these tags in networking systems – creating the appearance and functionality of network traffic that is physically on a single network but acts as if it is split between separate networks. In this way, VLANs can keep network applications separate despite being connected to the same physical network, and without requiring multiple sets of cabling and networking devices to be deployed.
A virtual private network (VPN) is a mechanism for creating a secure connection between a computing device and a computer network, or between two networks, using an insecure communication medium such as the public Internet.
A multilayer switch (MLS) is a computer networking device that switches on OSI layer 2 like an ordinary network switch and provides extra functions on higher OSI layers. The MLS was invented by engineers at Digital Equipment Corporation.

A digital subscriber line access multiplexer is a network device, often located in telephone exchanges, that connects multiple customer digital subscriber line (DSL) interfaces to a high-speed digital communications channel using multiplexing techniques. Its cable internet (DOCSIS) counterpart is the cable modem termination system.
In telecommunications, trunking is a technology for providing network access to multiple clients simultaneously by sharing a set of circuits, carriers, channels, or frequencies, instead of providing individual circuits or channels for each client. This is reminiscent to the structure of a tree with one trunk and many branches. Trunking in telecommunication originated in telegraphy, and later in telephone systems where a trunk line is a communications channel between telephone exchanges.
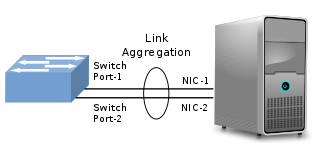
In computer networking, link aggregation is the combining of multiple network connections in parallel by any of several methods. Link aggregation increases total throughput beyond what a single connection could sustain, and provides redundancy where all but one of the physical links may fail without losing connectivity. A link aggregation group (LAG) is the combined collection of physical ports.

EtherChannel is a port link aggregation technology or port-channel architecture used primarily on Cisco switches. It allows grouping of several physical Ethernet links to create one logical Ethernet link for the purpose of providing fault-tolerance and high-speed links between switches, routers and servers. An EtherChannel can be created from between two and eight active Fast, Gigabit or 10-Gigabit Ethernet ports, with an additional one to eight inactive (failover) ports which become active as the other active ports fail. EtherChannel is primarily used in the backbone network, but can also be used to connect end user machines.
Cisco Inter-Switch Link (ISL) is a Cisco proprietary link layer protocol that maintains VLAN information in Ethernet frames as traffic flows between switches and routers, or switches and switches. ISL is Cisco's VLAN encapsulation protocol and is supported only on some Cisco equipment over the Fast and Gigabit Ethernet links. It is offered as an alternative to the IEEE 802.1Q standard, a widely used VLAN tagging protocol, although the use of ISL for new sites is deprecated by Cisco.
The Multiple Spanning Tree Protocol (MSTP) and algorithm, provides both simple and full connectivity assigned to any given virtual LAN (VLAN) throughout a bridged local area network. MSTP uses bridge protocol data unit (BPDUs) to exchange information between spanning-tree compatible devices, to prevent loops in each Multiple Spanning Tree instance (MSTI) and in the common and internal spanning tree (CIST), by selecting active and blocked paths. This is done as well as in Spanning Tree Protocol (STP) without the need of manually enabling backup links and getting rid of switching loop danger.
A switch virtual interface (SVI) represents a logical layer-3 interface on a switch.

In systems management, out-of-band management is a process for accessing and managing devices and infrastructure at remote locations through a separate management plane from the production network. OOB allows a system administrator to monitor and manage servers and other network-attached equipment by remote control regardless of whether the machine is powered on or whether an OS is installed or functional. It is contrasted to in-band management which requires the managed systems to be powered on and available over their operating system's networking facilities.

Private VLAN, also known as port isolation, is a technique in computer networking where a VLAN contains switch ports that are restricted such that they can only communicate with a given uplink. The restricted ports are called private ports. Each private VLAN typically contains many private ports, and a single uplink. The uplink will typically be a port connected to a router, firewall, server, provider network, or similar central resource.
VLAN hopping is a computer security exploit, a method of attacking networked resources on a virtual LAN (VLAN). The basic concept behind all VLAN hopping attacks is for an attacking host on a VLAN to gain access to traffic on other VLANs that would normally not be accessible. There are two primary methods of VLAN hopping: switch spoofing and double tagging. Both attack vectors can be mitigated with proper switch port configuration.
Data center bridging (DCB) is a set of enhancements to the Ethernet local area network communication protocol for use in data center environments, in particular for use with clustering and storage area networks.
IEEE 802.1ad is an amendment to the IEEE 802.1Q-1998 networking standard which adds support for provider bridges. It was incorporated into the base 802.1Q standard in 2011. The technique specified by the standard is known informally as stacked VLANs or QinQ.
Virtual Link Trunking (VLT) is a name that has been used for at least two proprietary network protocols. A link aggregation protocol developed by Force10 and an early VLAN tagging capability from 3Com.






