
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. It often uses a computer network to spread itself, relying on security failures on the target computer to access it. It will use this machine as a host to scan and infect other computers. When these new worm-invaded computers are controlled, the worm will continue to scan and infect other computers using these computers as hosts, and this behaviour will continue. Computer worms use recursive methods to copy themselves without host programs and distribute themselves based on exploiting the advantages of exponential growth, thus controlling and infecting more and more computers in a short time. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer.
In computing terminology, a macro virus is a virus that is written in a macro language: a programming language which is embedded inside a software application. Some applications, such as Microsoft Office, Excel, PowerPoint allow macro programs to be embedded in documents such that the macros are run automatically when the document is opened, and this provides a distinct mechanism by which malicious computer instructions can spread. This is one reason it can be dangerous to open unexpected attachments in e-mails. Many antivirus programs can detect macro viruses; however, the macro virus' behavior can still be difficult to detect.
Klez is a computer worm that propagates via e-mail. It first appeared in October 2001 and was originated in China. A number of variants of the worm exist.
Sircam is a computer worm that first propagated in 2001 by e-mail in Microsoft Windows systems. It affected computers running Windows 95, Windows 98, and Windows Me (Millennium). It began with one of the following lines of text and had an attachment consisting of the worm's executable with some file from the infected computer appended:

This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.
The Melissa virus is a mass-mailing macro virus released on or around March 26, 1999. It targets Microsoft Word and Outlook-based systems and created considerable network traffic. The virus infects computers via email; the email is titled "Important Message From," followed by the current username. Upon clicking the message, the body reads, "Here's that document you asked for. Don't show anyone else ;)." Attached is a Word document titled "list.doc," containing a list of pornographic sites and accompanying logins for each. It then mass-mails itself to the first fifty people in the user's contact list and disables multiple safeguard features on Microsoft Word and Microsoft Outlook.

Mydoom was a computer worm that targeted computers running Microsoft Windows. It was first sighted on January 26, 2004. It became the fastest-spreading e-mail worm ever, exceeding previous records set by the Sobig worm and ILOVEYOU, a record which as of 2024 has yet to be surpassed.
Bagle was a mass-mailing computer worm affecting Microsoft Windows. The first strain, Bagle.A, did not propagate widely. A second variant, Bagle.B, was considerably more virulent.
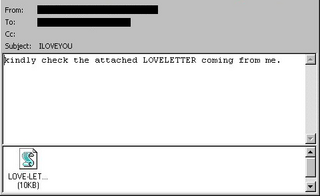
ILOVEYOU, sometimes referred to as the Love Bug or Loveletter, was a computer worm that infected over ten million Windows personal computers on and after 5 May 2000. It started spreading as an email message with the subject line "ILOVEYOU" and the attachment "LOVE-LETTER-FOR-YOU.TXT.vbs". At the time, Windows computers often hid the latter file extension by default because it is an extension for a file type that Windows knows, leading unwitting users to think it was a normal text file. Opening the attachment activates the Visual Basic script. First, the worm inflicts damage on the local machine, overwriting random files, then, it copies itself to all addresses in the Windows Address Book used by Microsoft Outlook, allowing it to spread much faster than any other previous email worm.
Zotob is a computer worm which exploits security vulnerabilities in Microsoft operating systems like Windows 2000, including the MS05-039 plug-and-play vulnerability. This worm has been known to spread on Microsoft-ds or TCP port 445.
The Sober worm is a family of computer worms that was discovered on October 24, 2003. Like many worms, Sober sends itself as an e-mail attachment, fake webpages, fake pop-up ads, and fake advertisements.
CTX is a computer virus created in Spain in 1999. CTX was initially discovered as part of the Cholera worm, with which the author intentionally infected with CTX. Although the Cholera worm had the capability to send itself via email, the CTX worm quickly surpassed it in prevalence. Cholera is now considered obsolete, while CTX remains in the field, albeit with only rare discoveries.
W32.Navidad is a mass-mailing worm program or virus, discovered in December 2000 that ran on Windows 95, Windows 98, Windows NT, and Windows 2000 systems. It was designed to spread through email clients such as Microsoft Outlook while masquerading as an executable electronic Christmas card. Infected computers can be identified by blue eye icons which appear in the Windows system tray.
ExploreZip is a destructive computer worm that attacks machines running Microsoft Windows. It was first discovered in Israel on June 6, 1999. The worm contains a malicious payload, and utilizes Microsoft Outlook, Outlook Express, or Exchange to mail itself out by replying to unread messages in the user's inbox. The worm also searches mapped drives and networked computers for Windows installations. If found, it copies itself to the Windows folder of the remote computer and then modifies the Win.ini file of the infected computer. On January 8, 2003, Symantec discovered a packed variant of this threat which exhibits the same characteristics.
Stration is a family of computer worms that can affect computers running Microsoft Windows, disabling security features and propagating itself to other computers via e-mail attachments. This family of worms is unusual in that new variants are being produced at an unprecedented rate, estimated to be up to one every 30 minutes at its peak, and downloaded from remote servers by infected machines to speed propagation. This makes detection and removal a particular challenge for anti-virus software vendors, because new signature files for each variant need to be issued to allow their software to detect them.

A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses.
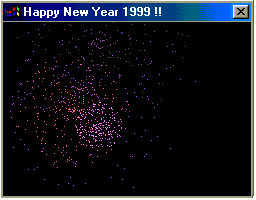
Happy99 is a computer worm for Microsoft Windows. It first appeared in mid-January 1999, spreading through email and usenet. The worm installs itself and runs in the background of a victim's machine, without their knowledge. It is generally considered the first virus to propagate by email, and has served as a template for the creation of other self-propagating viruses. Happy99 has spread on multiple continents, including North America, Europe, and Asia.
Swen is a mass mailing computer worm written in C++. It sends an email which contains the installer for the virus, disguised as a Microsoft Windows update, although it also works on P2P filesharing networks, IRC and newsgroups' websites. It was first analyzed on September 18, 2003, however, it might have infected computers before then. It disables firewalls and antivirus programs.
Sality is the classification for a family of malicious software (malware), which infects Microsoft Windows systems files. Sality was first discovered in 2003 and has advanced to become a dynamic, enduring and full-featured form of malicious code. Systems infected with Sality may communicate over a peer-to-peer (P2P) network to form a botnet to relay spam, proxying of communications, exfiltrating sensitive data, compromising web servers and/or coordinating distributed computing tasks to process intensive tasks. Since 2010, certain variants of Sality have also incorporated rootkit functions as part of an ongoing evolution of the malware family. Because of its continued development and capabilities, Sality is considered one of the most complex and formidable forms of malware to date.
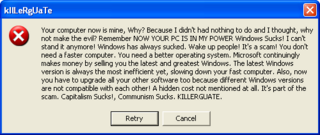
Gruel, also referred to by F-Secure as Fakerr, was a worm first surfacing in 2003 targeting Microsoft Windows platforms such as Windows 9x, Windows ME, Windows 2000 and Windows XP. It spread via email and file sharing networks.




