Related Research Articles

IEEE 802.11 is part of the IEEE 802 set of local area network (LAN) technical standards, and specifies the set of medium access control (MAC) and physical layer (PHY) protocols for implementing wireless local area network (WLAN) computer communication. The standard and amendments provide the basis for wireless network products using the Wi-Fi brand and are the world's most widely used wireless computer networking standards. IEEE 802.11 is used in most home and office networks to allow laptops, printers, smartphones, and other devices to communicate with each other and access the Internet without connecting wires. IEEE 802.11 is also a basis for vehicle-based communication networks with IEEE 802.11p.

Wi-Fi is a family of wireless network protocols based on the IEEE 802.11 family of standards, which are commonly used for local area networking of devices and Internet access, allowing nearby digital devices to exchange data by radio waves. These are the most widely used computer networks, used globally in home and small office networks to link devices and to provide Internet access with wireless routers and wireless access points in public places such as coffee shops, hotels, libraries, and airports to provide visitors.

In computer networking, a wireless access point, or more generally just access point (AP), is a networking hardware device that allows other Wi-Fi devices to connect to a wired network or wireless network. As a standalone device, the AP may have a wired or wireless connection to a router or router, but, in a wireless router, it can also be an integral component of the networking devices itself. An WAP & AP is differentiated from a Wi-Fi|Mi-Fi)|hotspot, which is a can be a physical location or digital location where Wi-Fi or WAP access is available.
Wi-Fi Protected Access (WPA), Wi-Fi Protected Access 2 (WPA2), and Wi-Fi Protected Access 3 (WPA3) are the three security certification programs developed after 2000 by the Wi-Fi Alliance to secure wireless computer networks. The Alliance defined these in response to serious weaknesses researchers had found in the previous system, Wired Equivalent Privacy (WEP).

The Wi-Fi Alliance is a non-profit organization that owns the Wi-Fi trademark. Manufacturers may use the trademark to brand products certified for Wi-Fi interoperability. It is based in Austin, Texas.
Temporal Key Integrity Protocol is a security protocol used in the IEEE 802.11 wireless networking standard. TKIP was designed by the IEEE 802.11i task group and the Wi-Fi Alliance as an interim solution to replace WEP without requiring the replacement of legacy hardware. This was necessary because the breaking of WEP had left Wi-Fi networks without viable link-layer security, and a solution was required for already deployed hardware. However, TKIP itself is no longer considered secure, and was deprecated in the 2012 revision of the 802.11 standard.
Netgear, Inc., is an American computer networking company based in San Jose, California, with offices in about 22 other countries. It produces networking hardware for consumers, businesses, and service providers. The company operates in three business segments: retail, commercial, and as a service provider.

Ralink Technology, Corp. is a Wi-Fi chipset manufacturer mainly known for their IEEE 802.11 chipsets. Ralink was founded in 2001 in Cupertino, California, then moved its headquarters to Hsinchu, Taiwan. On 5 May 2011, Ralink was acquired by MediaTek.
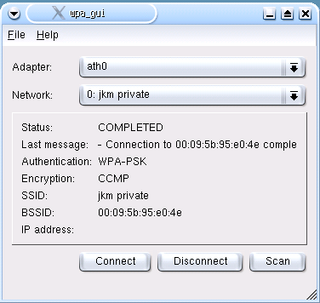
wpa_supplicant is a free software implementation of an IEEE 802.11i supplicant for Linux, FreeBSD, NetBSD, QNX, AROS, Microsoft Windows, Solaris, OS/2 and Haiku. In addition to being a WPA3 and WPA2 supplicant, it also implements WPA and older wireless LAN security protocols.
WPS may refer to:

Orange Livebox is an ADSL wireless router available to customers of Orange's Broadband services in Kenya, Guinea, France, Tunisia, Spain, Jordan, the Netherlands, Switzerland, Poland, Belgium, The United Kingdom (Formerly), Mauritian partner MyT, Lightspeed Communications in Bahrain and Orange Botswana. Depending on the model, it is manufactured by Inventel, Sagecom or ZTE. The Livebox is also known as FunBox in some countries like Poland, Ivory Coast and Senegal.

Wi-Fi Protected Setup (WPS) originally, Wi-Fi Simple Config, is a network security standard to create a secure wireless home network.

Eye-Fi was a company based in Mountain View, California, that produced SD memory cards with Wi-Fi capabilities. Using an Eye-Fi card inside a digital camera, one could wirelessly and automatically upload digital photos to a local computer or a mobile device such as a smartphone or tablet computer. The company ceased business in 2016.

Wi-Fi Direct is a Wi-Fi standard for peer-to-peer wireless connections that allows two devices to establish a direct Wi-Fi connection without an intermediary wireless access point, router, or Internet connection. Wi-Fi Direct is single-hop communication, rather than multi-hop communication like wireless ad hoc networks. The Wi-Fi Direct standard was specified in 2009.
SecureEasySetup, or SES is a proprietary technology developed by Broadcom to easily set up wireless LANs with Wi-Fi Protected Access. A user presses a button on the wireless access point, then a button on the device to be set up and the wireless network is automatically set up.
IEEE 1905.1 is an IEEE standard which defines a network enabler for home networking supporting both wireless and wireline technologies: IEEE 802.11, IEEE 1901 power-line networking, IEEE 802.3 Ethernet and Multimedia over Coax (MoCA).
Miracast is a wireless communications standard created by the Wi-Fi Alliance which is designed to transmit video and sound from devices to display receivers. It uses Wi-Fi Direct to create an ad hoc encrypted wireless connection and can roughly be described as "HDMI over Wi-Fi", replacing cables in favor of wireless. Miracast is utilised in many devices and is used or branded under various names by different manufacturers, including Smart View, SmartShare, screen mirroring, Cast, wireless display and screen casting.
A Wi-Fi deauthentication attack is a type of denial-of-service attack that targets communication between a user and a Wi-Fi wireless access point.

KRACK is a replay attack on the Wi-Fi Protected Access protocol that secures Wi-Fi connections. It was discovered in 2016 by the Belgian researchers Mathy Vanhoef and Frank Piessens of the University of Leuven. Vanhoef's research group published details of the attack in October 2017. By repeatedly resetting the nonce transmitted in the third step of the WPA2 handshake, an attacker can gradually match encrypted packets seen before and learn the full keychain used to encrypt the traffic.
Kr00k is a security vulnerability that allows some WPA2 encrypted WiFi traffic to be decrypted. The vulnerability was originally discovered by security company ESET in 2019 and assigned CVE-2019-15126 on August 17th, 2019. ESET estimates that this vulnerability affects over a billion devices.
References
- ↑ "Get in touch today..." Tactical Network Solutions. Retrieved 23 November 2021.
- ↑ Gallagher, Sean (4 January 2012). "Hands-on: hacking WiFi Protected Setup with Reaver" . Retrieved 6 January 2012.
- ↑ Viebock, Stefan (27 December 2011). "Wi-Fi Protected Setup PIN brute force vulnerability" . Retrieved 6 January 2012.