Related Research Articles

Cryptanalysis is the study of analyzing information systems in order to study the hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown.
In cryptography, SHA-1 is a cryptographic hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered as a hexadecimal number, 40 digits long. It was designed by the United States National Security Agency, and is a U.S. Federal Information Processing Standard.

Ronald Linn Rivest is a cryptographer and an Institute Professor at MIT. He is a member of MIT's Department of Electrical Engineering and Computer Science (EECS) and a member of MIT's Computer Science and Artificial Intelligence Laboratory (CSAIL). His work has spanned the fields of algorithms and combinatorics, cryptography, machine learning, and election integrity.
The Advanced Encryption Standard (AES), the symmetric block cipher ratified as a standard by National Institute of Standards and Technology of the United States (NIST), was chosen using a process lasting from 1997 to 2000 that was markedly more open and transparent than its predecessor, the Data Encryption Standard (DES). This process won praise from the open cryptographic community, and helped to increase confidence in the security of the winning algorithm from those who were suspicious of backdoors in the predecessor, DES.

In cryptography, RC6 is a symmetric key block cipher derived from RC5. It was designed by Ron Rivest, Matt Robshaw, Ray Sidney, and Yiqun Lisa Yin to meet the requirements of the Advanced Encryption Standard (AES) competition. The algorithm was one of the five finalists, and also was submitted to the NESSIE and CRYPTREC projects. It was a proprietary algorithm, patented by RSA Security.
Articles related to cryptography include:

A cryptographic hash function (CHF) is a mathematical algorithm that maps data of arbitrary size to a bit array of a fixed size. It is a one-way function, that is, a function which is practically infeasible to invert. Ideally, the only way to find a message that produces a given hash is to attempt a brute-force search of possible inputs to see if they produce a match, or use a rainbow table of matched hashes. Cryptographic hash functions are a basic tool of modern cryptography.
Cryptography, the use of codes and ciphers to protect secrets, began thousands of years ago. Until recent decades, it has been the story of what might be called classic cryptography — that is, of methods of encryption that use pen and paper, or perhaps simple mechanical aids. In the early 20th century, the invention of complex mechanical and electromechanical machines, such as the Enigma rotor machine, provided more sophisticated and efficient means of encryption; and the subsequent introduction of electronics and computing has allowed elaborate schemes of still greater complexity, most of which are entirely unsuited to pen and paper.
Joan Daemen is a Belgian cryptographer who co-designed with Vincent Rijmen the Rijndael cipher, which was selected as the Advanced Encryption Standard (AES) in 2001. More recently, he co-designed the Keccak cryptographic hash, which was selected as the new SHA-3 hash by NIST in October 2012. He has also designed or co-designed the MMB, Square, SHARK, NOEKEON, 3-Way, and BaseKing block ciphers. In 2017 he won the Levchin Prize for Real World Cryptography "for the development of AES and SHA3". He describes his development of encryption algorithms as creating the bricks which are needed to build the secure foundations online.
CRYPTREC is the Cryptography Research and Evaluation Committees set up by the Japanese Government to evaluate and recommend cryptographic techniques for government and industrial use. It is comparable in many respects to the European Union's NESSIE project and to the Advanced Encryption Standard process run by National Institute of Standards and Technology in the U.S..

Lars Ramkilde Knudsen is a Danish researcher in cryptography, particularly interested in the design and analysis of block ciphers, hash functions and message authentication codes (MACs).
In cryptography, nothing-up-my-sleeve numbers are any numbers which, by their construction, are above suspicion of hidden properties. They are used in creating cryptographic functions such as hashes and ciphers. These algorithms often need randomized constants for mixing or initialization purposes. The cryptographer may wish to pick these values in a way that demonstrates the constants were not selected for a nefarious purpose, for example, to create a backdoor to the algorithm. These fears can be allayed by using numbers created in a way that leaves little room for adjustment. An example would be the use of initial digits from the number π as the constants. Using digits of π millions of places after the decimal point would not be considered trustworthy because the algorithm designer might have selected that starting point because it created a secret weakness the designer could later exploit.
Wang Xiaoyun is a Chinese cryptographer, mathematician, and computer scientist. She is a professor in the Department of Mathematics and System Science of Shandong University and an academician of the Chinese Academy of Sciences.
ECRYPT was a 4-year European research initiative launched on 1 February 2004 with the stated objective of promoting the collaboration of European researchers in information security, and especially in cryptology and digital watermarking.
Institute of Electrical and Electronics Engineers (IEEE) standardization project for encryption of stored data, but more generically refers to the Security in Storage Working Group (SISWG), which includes a family of standards for protection of stored data and for the corresponding cryptographic key management.
Burton S. "Burt" Kaliski, Jr. is a cryptographer, who is currently the chief technology officer (CTO) and senior vice president at Verisign. Before joining Verisign in 2011, he was the founding director of the EMC Innovation Network at EMC Corporation since its 2006 acquisition of RSA Security where he was Chief Scientist for RSA Laboratories. His notable work includes the development of such public key cryptography standards as PKCS and IEEE P1363, the extension of linear cryptanalysis to use multiple approximations, and the design of the block cipher Crab.

Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of third parties called adversaries. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages; various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation are central to modern cryptography. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, electrical engineering, communication science, and physics. Applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications.
The following outline is provided as an overview of and topical guide to cryptography:
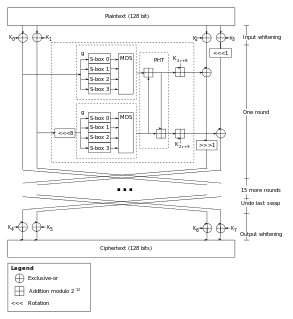
In cryptography, Twofish is a symmetric key block cipher with a block size of 128 bits and key sizes up to 256 bits. It was one of the five finalists of the Advanced Encryption Standard contest, but it was not selected for standardization. Twofish is related to the earlier block cipher Blowfish.
References
- 1 2 3 Yin, Lisa, Biography , retrieved 2019-10-03
- ↑ Yiqun Lisa Yin at the Mathematics Genealogy Project
- ↑ Kaliski, Burt (July 1997), IEEE P1363: A Comprehensive Standard for Public-Key Cryptography (PDF). See "Officers", p. 37.
- ↑ Schneier, Bruce; Whiting, Doug (2000), "A performance comparison of the five AES finalists" (PDF), AES Candidate Conference
- ↑ Greene, Thomas C. (February 17, 2005), "Crypto researchers break SHA-1", The Register
- ↑ Thomson, Iain (November 21, 2016), "Microsoft plans St Valentine's Day massacre for SHA‑1: End of the line for weak hash as web giants finally act", The Register