Related Research Articles

GNU Hurd is a collection of microkernel servers written as part of GNU, for the GNU Mach microkernel. It has been under development since 1990 by the GNU Project of the Free Software Foundation, designed as a replacement for the Unix kernel, and released as free software under the GNU General Public License. When the Linux kernel proved to be a viable solution, development of GNU Hurd slowed, at times alternating between stasis and renewed activity and interest.

In computer science, a microkernel is the near-minimum amount of software that can provide the mechanisms needed to implement an operating system (OS). These mechanisms include low-level address space management, thread management, and inter-process communication (IPC).
Mach is a kernel developed at Carnegie Mellon University by Richard Rashid and Avie Tevanian to support operating system research, primarily distributed and parallel computing. Mach is often considered one of the earliest examples of a microkernel. However, not all versions of Mach are microkernels. Mach's derivatives are the basis of the operating system kernel in GNU Hurd and of Apple's XNU kernel used in macOS, iOS, iPadOS, tvOS, and watchOS.
The trusted computing base (TCB) of a computer system is the set of all hardware, firmware, and/or software components that are critical to its security, in the sense that bugs or vulnerabilities occurring inside the TCB might jeopardize the security properties of the entire system. By contrast, parts of a computer system that lie outside the TCB must not be able to misbehave in a way that would leak any more privileges than are granted to them in accordance to the system's security policy.
Darwin is the core Unix-like operating system of macOS, iOS, watchOS, tvOS, iPadOS, audioOS, visionOS, and bridgeOS. It previously existed as an independent open-source operating system, first released by Apple Inc. in 2000. It is composed of code derived from NeXTSTEP, FreeBSD, other BSD operating systems, Mach, and other free software projects' code, as well as code developed by Apple. Darwin's official mascot is Hexley the Platypus.

QNX is a commercial Unix-like real-time operating system, aimed primarily at the embedded systems market.
L4 is a family of second-generation microkernels, used to implement a variety of types of operating systems (OS), though mostly for Unix-like, Portable Operating System Interface (POSIX) compliant types.
In the context of hardware and software systems, formal verification is the act of proving or disproving the correctness of a system with respect to a certain formal specification or property, using formal methods of mathematics. Formal verification is a key incentive for formal specification of systems, and is at the core of formal methods. It represents an important dimension of analysis and verification in electronic design automation and is one approach to software verification. The use of formal verification enables the highest Evaluation Assurance Level (EAL7) in the framework of common criteria for computer security certification.
Capability-based security is a concept in the design of secure computing systems, one of the existing security models. A capability is a communicable, unforgeable token of authority. It refers to a value that references an object along with an associated set of access rights. A user program on a capability-based operating system must use a capability to access an object. Capability-based security refers to the principle of designing user programs such that they directly share capabilities with each other according to the principle of least privilege, and to the operating system infrastructure necessary to make such transactions efficient and secure. Capability-based security is to be contrasted with an approach that uses traditional UNIX permissions and Access Control Lists.
K42 is a discontinued open-source research operating system (OS) for cache-coherent 64-bit multiprocessor systems. It was developed primarily at IBM Thomas J. Watson Research Center in collaboration with the University of Toronto and University of New Mexico. The main focus of this OS is to address performance and scalability issues of system software on large-scale, shared memory, non-uniform memory access (NUMA) multiprocessing computers.
KeyKOS is a persistent, pure capability-based operating system for the IBM S/370 mainframe computers. It allows emulating the environments of VM, MVS, and Portable Operating System Interface (POSIX). It is a predecessor of the Extremely Reliable Operating System (EROS), and its successor operating systems, CapROS, and Coyotos. KeyKOS is a nanokernel-based operating system.

Jochen Liedtke was a German computer scientist, noted for his work on microkernel operating systems, especially in creating the L4 microkernel family.
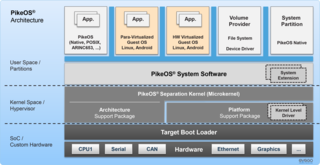
PikeOS is a commercial hard real-time operating system (RTOS) which features a separation kernel-based hypervisor. This hypervisor supports multiple logical partition types for various operating systems (OS) and applications, each referred to as a GuestOS. PikeOS is engineered to support the creation of certifiable smart devices for the Internet of Things (IoT), ensuring compliance with industry standards for quality, safety, and security across various sectors. In instances where memory management units (MMU) are not present but memory protection units (MPU) are available on controller-based systems, PikeOS for MPU is designed for critical real-time applications and provides up-to-standard safety and security.
Capability-based operating system generally refers to an operating system that uses capability-based security.
The object-capability model is a computer security model. A capability describes a transferable right to perform one operations on a given object. It can be obtained by the following combination:

Gernot Heiser is a Scientia Professor and the John Lions Chair for operating systems at UNSW Sydney, where he leads the Trustworthy Systems group (TS).
A separation kernel is a type of security kernel used to simulate a distributed environment. The concept was introduced by John Rushby in a 1981 paper. Rushby proposed the separation kernel as a solution to the difficulties and problems that had arisen in the development and verification of large, complex security kernels that were intended to "provide multilevel secure operation on general-purpose multi-user systems." According to Rushby, "the task of a separation kernel is to create an environment which is indistinguishable from that provided by a physically distributed system: it must appear as if each regime is a separate, isolated machine and that information can only flow from one machine to another along known external communication lines. One of the properties we must prove of a separation kernel, therefore, is that there are no channels for information flow between regimes other than those explicitly provided."

The kernel is a computer program at the core of a computer's operating system and generally has complete control over everything in the system. The kernel is also responsible for preventing and mitigating conflicts between different processes. It is the portion of the operating system code that is always resident in memory and facilitates interactions between hardware and software components. A full kernel controls all hardware resources via device drivers, arbitrates conflicts between processes concerning such resources, and optimizes the utilization of common resources e.g. CPU & cache usage, file systems, and network sockets. On most systems, the kernel is one of the first programs loaded on startup. It handles the rest of startup as well as memory, peripherals, and input/output (I/O) requests from software, translating them into data-processing instructions for the central processing unit.
An embedded hypervisor is a hypervisor that supports the requirements of embedded systems.

Genode is a free and open-source software operating system (OS) framework consisting of a microkernel abstraction layer and a set of user space components. The framework is notable as one of the few open-source operating systems not derived from a proprietary OS, such as Unix. The characteristic design philosophy is that a small trusted computing base is of primary concern in a security-oriented OS.
References
- ↑ Shapiro, Jonathan S.; Weber, Samuel (October 29, 1999). Verifying the EROS Confinement Mechanism (PDF). 2000 IEEE Symposium on Security and Privacy. Berkeley, CA, USA. doi:10.1109/SECPRI.2000.848454.
- ↑ Lee, Peter. "Proof-Carrying Code". Archived from the original on September 22, 2006.
- ↑ Shapiro, Jonathan (April 2, 2006). "Differences Between Coyotos and EROS: A Quick Summary". Archived from the original on 2012-07-31.
- 1 2 Shapiro, Jonathan S. (April 7, 2009). "Status of Coyotos". coyotos-dev (Mailing list). Archived from the original on July 24, 2014. Retrieved 16 March 2022.
Active work on Coyotos stopped several months ago, and is unlikely to resume.
- ↑ Shapiro, Jonathan S.; Vanderburgh, John; Northup, Eric; Chizmadia, David (2004). Design of the EROS Trusted Window System (PDF). 13th USENIX Security Symposium. San Diego, CA, USA.
- ↑ Sinha, Anshumal; Sarat, Sandeep; Shapiro, Jonathan S. (2004). Network Subsystems Reloaded: A High-Performance, Defensible Network Subsystem (PDF). 2004 USENIX Annual Technical Conference. Boston, MA, USA.
- ↑ Chen, Hao; Shapiro, Jonathan S. "Using Build-Integrated Static Checking to Preserve Correctness Invariants" (PDF). Archived from the original (PDF) on March 3, 2016.
- ↑ Shapiro, Jonathan S. (2003). Vulnerabilities in Synchronous IPC Designs (PDF). 2003 Symposium on Security and Privacy. Berkeley, CA, USA. doi:10.1109/SECPRI.2003.1199341.
- ↑ Chakraborty, Pinaki (2010). "Research purpose operating systems – a wide survey". GESJ: Computer Science and Telecommunications. 3 (26). ISSN 1512-1232.
Journals
- Lipton, R. J.; Snyder, L. (July 1977). "A Linear Time Algorithm for Deciding Subject Security". Journal of the ACM. 24 (3): 455–464. doi: 10.1145/322017.322025 . S2CID 291367.
- Harrison, Michael A.; Ruzzo, W. L.; Ullman, Jeffrey D. (August 1976). "Protection in Operating Systems". Communications of the ACM. 19 (8): 461–471. doi: 10.1145/360303.360333 . S2CID 5900205.