The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the German military. The Enigma machine was considered so secure that it was used to encipher the most top-secret messages.

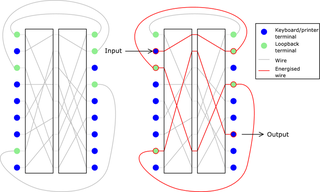
In the history of cryptography, Typex machines were British cipher machines used from 1937. It was an adaptation of the commercial German Enigma with a number of enhancements that greatly increased its security. The cipher machine was used until the mid-1950s when other more modern military encryption systems came into use.

In the history of cryptography, the ECM Mark II was a cipher machine used by the United States for message encryption from World War II until the 1950s. The machine was also known as the SIGABA or Converter M-134 by the Army, or CSP-888/889 by the Navy, and a modified Navy version was termed the CSP-2900.

William Frederick Friedman was a US Army cryptographer who ran the research division of the Army's Signal Intelligence Service (SIS) in the 1930s, and parts of its follow-on services into the 1950s. In 1940, subordinates of his led by Frank Rowlett broke Japan's PURPLE cipher, thus disclosing Japanese diplomatic secrets before America's entrance into World War II.
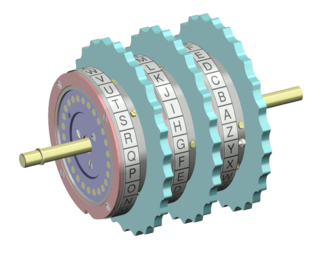
In cryptography, a rotor machine is an electro-mechanical stream cipher device used for encrypting and decrypting messages. Rotor machines were the cryptographic state-of-the-art for much of the 20th century; they were in widespread use in the 1920s–1970s. The most famous example is the German Enigma machine, the output of which was deciphered by the Allies during World War II, producing intelligence code-named Ultra.
Articles related to cryptography include:

Crypto AG was a Swiss company specialising in communications and information security founded by Boris Hagelin in 1952. The company was secretly purchased for US $5.75 million and jointly owned by the American Central Intelligence Agency (CIA) and West German Federal Intelligence Service (BND) from 1970 until about 1993, with the CIA continuing as sole owner until about 2018. The mission of breaking encrypted communication using a secretly owned company was known as "Operation Rubikon". With headquarters in Steinhausen, the company was a long-established manufacturer of encryption machines and a wide variety of cipher devices.
Cryptography was used extensively during World War II because of the importance of radio communication and the ease of radio interception. The nations involved fielded a plethora of code and cipher systems, many of the latter using rotor machines. As a result, the theoretical and practical aspects of cryptanalysis, or codebreaking, were much advanced.

The TSEC/KL-7, also known as Adonis was an off-line non-reciprocal rotor encryption machine. The KL-7 had rotors to encrypt the text, most of which moved in a complex pattern, controlled by notched rings. The non-moving rotor was fourth from the left of the stack. The KL-7 also encrypted the message indicator.

In the history of cryptography, the Kryha machine was a device for encryption and decryption, appearing in the early 1920s and used until the 1950s. The machine was the invention of Alexander von Kryha. During the Second World War, Kryha worked as an officer for the German Wehrmacht. There were several versions; the standard Kryha machine weighed around five kilograms, and was totally mechanical. A scaled down pocket version was introduced later on, termed the "Lilliput" model. There was also a more bulky electrical version.

JADE was the codename given by US codebreakers to a Japanese World War II cipher machine. The Imperial Japanese Navy used the machine for communications from late 1942 until 1944. JADE was similar to another cipher machine, CORAL, with the main difference that JADE was used to encipher messages in katakana using an alphabet of 50 symbols.

Arvid Gerhard Damm was a Swedish engineer and inventor. He designed a number of cipher machines, and was one of the early inventors of the wired rotor principle for machine encipherment. The company, AB Cryptograph, was an early predecessor of Crypto AG.

The HC-9 was a mechanical cipher device manufactured by the Swedish company AB Transvertex. It was designed in the early 1950's for the Swedish Armed Forces and in use from 1963 to 1995 as Krypteringsapparat 301. This machine was used for low-level communications such as platoon, company, up to battalion levels and in regimental and brigade staffs.The machine dimensions are 18 x 15 x 7 cm.

The (Hagelin) CD-57 was a portable, mechanical cipher machine manufactured by Crypto AG, first produced in 1957. It was derived from the earlier CD-55, and was designed to be compatible with the larger C-52 machines. Compact, the CD-57 measured merely 5 1/8in × 3 1/8in × 1 1/2in and weighed 1.5 pounds. The CD-57 used six wheels.

The (Hagelin) C-52 and CX-52 were cipher machines manufactured by Crypto AG starting 1951/1952. These pin-and-lug type cipher machines were advanced successors of the C-38/M-209. The machine measures 8+1⁄2 by 5+3⁄8 by 4+3⁄8 inches. The device is mechanical, but when combined with an electric keyboard attachment, the B-52, the resultant system is termed the BC-52. The B-52 is larger, measuring 12+1⁄2 by 8+1⁄2 by 6+3⁄8 inches.

In cryptography, a pinwheel was a device for producing a short pseudorandom sequence of bits, as a component in a cipher machine. A pinwheel consisted of a rotating wheel with a certain number of positions on its periphery. Each position had a "pin", "cam" or "lug" which could be either "set" or "unset". As the wheel rotated, each of these pins would in turn affect other parts of the machine, producing a series of "on" or "off" pulses which would repeat after one full rotation of the wheel. If the machine contained more than one wheel, usually their periods would be relatively prime to maximize the combined period. Pinwheels might be turned through a purely mechanical action or electromechanically.
Below is a timeline of notable events related to cryptography.

The OMI cryptograph was a rotor cipher machine produced and sold by Italian firm Ottico Meccanica Italiana (OMI) in Rome.
The following outline is provided as an overview of and topical guide to cryptography:

The Schlüsselgerät 41, also known as the SG-41 or Hitler mill, was a rotor cipher machine, first produced in 1941 in Nazi Germany, that was designed as a potential successor for the Enigma machine. It saw limited use by the Abwehr towards the end of World War II.