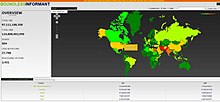
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The existence of the NSA was not revealed until 1975. The NSA has roughly 32,000 employees.

The Gulf of Tonkin incident was an international confrontation that led to the United States engaging more directly in the Vietnam War. It consisted of a confrontation on August 2, 1964, when United States forces were carrying out covert operations close to North Vietnamese territorial waters and North Vietnamese forces responded. The United States government falsely claimed that a second incident occurred on August 4, 1964, between North Vietnamese and United States ships in the waters of the Gulf of Tonkin. Originally, US military claims blamed North Vietnam for the confrontation and the ostensible, but in fact imaginary, incident on August 4. Later investigation revealed that the second attack never happened; the official American claim is that it was based mostly on erroneously interpreted communications intercepts. The National Security Agency, a subsidiary of the US Defense Department, deliberately skewed intelligence to create the impression that an attack had been carried out.

USS Pueblo (AGER-2) is a Banner-class environmental research ship, initially in service during World War II, then converted to a spy ship in 1967 by the United States Navy. She gathered intelligence and oceanographic information, in particular monitoring electronic and radio signals from North Korea. On 23 January 1968, the ship was attacked and captured by a North Korean vessel, in what became known as the "Pueblo incident", or alternatively, as the "Pueblo crisis".

The President's Daily Brief, sometimes referred to as the President's Daily Briefing or the President's Daily Bulletin, is a top-secret document produced and given each morning to the president of the United States; it is also distributed to a small number of top-level US officials who are approved by the president. It includes highly classified intelligence analysis, information about covert operations, and reports from the most sensitive US sources or those shared by allied intelligence agencies. At the discretion of the president, the PDB may also be provided to the president-elect of the United States, between election day and inauguration, and to former presidents on request.

The Central Security Service (CSS) is a combat support agency of the United States Department of Defense which was established in 1972 to integrate the National Security Agency (NSA) and the Service Cryptologic Components (SCC) of the United States Armed Forces in the field of signals intelligence, cryptology, and information assurance at the tactical level. In 2002, the CSS had approximately 25,000 uniformed members. It is part of the United States Intelligence Community.

Technical research ships were used by the United States Navy during the 1960s to gather intelligence by monitoring, recording and analyzing wireless electronic communications of nations in various parts of the world. At the time these ships were active, the mission of the ships was covert and discussion of the true mission was prohibited. The mission of the ships was publicly given as conducting research into atmospheric and communications phenomena. However, the true mission was more or less an open secret and the ships were commonly referred to as "spy ships".

A spy ship or reconnaissance vessel is a dedicated ship intended to gather intelligence, usually by means of sophisticated electronic eavesdropping. In a wider sense, any ship intended to gather information could be considered a spy ship.

DESOTO patrols were patrols conducted by U.S. Navy destroyers equipped with a mobile "van" of signals-intelligence equipment used for intelligence collection in hostile waters. The USS De Haven became the namesake for these patrols. De Haven performed the first patrol off the coast of China in April 1962. The USS Agerholm carried out the first patrol to target North Vietnam in the Gulf of Tonkin in December 1962.

The United States Army Security Agency (ASA) was the United States Army's signals intelligence branch from 1945 to 1976. The Latin motto of the Army Security Agency was Semper Vigilis, which echoes the declaration, often mistakenly attributed to Thomas Jefferson, that "The price of liberty is eternal vigilance."
Unit 8200 is an Israeli Intelligence Corps unit of the Israel Defense Forces responsible for clandestine operation, collecting signal intelligence (SIGINT) and code decryption, counterintelligence, cyberwarfare, military intelligence, and surveillance. Military publications include references to Unit 8200 as the Central Collection Unit of the Intelligence Corps, and it is sometimes referred to as Israeli SIGINT National Unit (ISNU). It is subordinate to Aman, the military intelligence directorate.

USS Jamestown (AGTR-3/AG-166) was an Oxford-class technical research ship acquired by the U.S. Navy for the task of "conducting research in the reception of electromagnetic propagations" (SIGINT).

Signals intelligence operational platforms are employed by nations to collect signals intelligence, which is intelligence-gathering by interception of signals, whether between people or between machines, or mixtures of the two. As sensitive information is often encrypted, signals intelligence often involves the use of cryptanalysis. However, traffic analysis—the study of who is signalling whom and in what quantity—can often produce valuable information, even when the messages themselves cannot be decrypted.
After the end of World War II, all the Western allies began a rapid drawdown of military forces, including those of signals intelligence. At the time, the US still had a COMINT organization split between the Army and Navy. A 1946 plan listed Russia, China, and a [redacted] country as high-priority targets.

Initially established as the Air Force (USAF) Security Group in June, 1948, the USAF Security Service (USAFSS) was activated as a major command on Oct 20, 1948

Turbulence is a United States National Security Agency (NSA) information-technology project started c. 2005. It was developed in small, inexpensive "test" pieces rather than one grand plan like its failed predecessor, the Trailblazer Project. It also includes offensive cyberwarfare capabilities, like injecting malware into remote computers. The U.S. Congress criticized the project in 2007 for having similar bureaucratic problems as the Trailblazer Project.
Monitoring Station Designators were used by the United States Army Signals Intelligence Service to designate a specific signal intelligence monitoring station in order to allow analysts to understand the source and type of SIGINT they were analyzing. These were used as shorthand rather than writing or typing out the PLA, which consisted of the formal unit name and location of the unit who performed the signals collection.

OAKSTAR is a secret internet surveillance program of the National Security Agency (NSA) of the United States. It was disclosed in 2013 as part of the leaks by former NSA contractor Edward Snowden.
Digital Network Intelligence or DNI is a term used in the United States Intelligence Community that refers to "intelligence from intercepted digital data communications transmitted between, or resident on, networked computers."
This is a category of disclosures related to global surveillance.
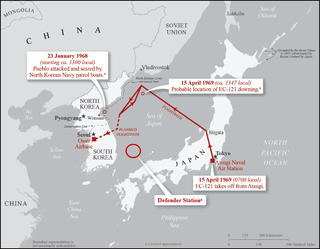
Operation Formation Star was the code name for the emergency re-deployment of U.S. Seventh Fleet warships to the Sea of Japan off the eastern coast of North Korea following that country's seizure of the USS Pueblo (AGER-2) in international waters on 23 January 1968.