
A telephone card, calling card or phone card for short, is a credit card-size plastic or paper card used to pay for telephone services. It is not necessary to have the physical card except with a stored-value system; knowledge of the access telephone number to dial and the PIN is sufficient. Standard cards which can be purchased and used without any sort of account facility give a fixed amount of credit and are discarded when used up; rechargeable cards can be topped up, or collect payment in arrears. The system for payment and the way in which the card is used to place a telephone call vary from card to card.

In physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.

A smart card (SC), chip card, or integrated circuit card, is a card used to control access to a resource. It is typically a plastic credit card-sized card with an embedded integrated circuit (IC) chip. Many smart cards include a pattern of metal contacts to electrically connect to the internal chip. Others are contactless, and some are both. Smart cards can provide personal identification, authentication, data storage, and application processing. Applications include identification, financial, public transit, computer security, schools, and healthcare. Smart cards may provide strong security authentication for single sign-on (SSO) within organizations. Numerous nations have deployed smart cards throughout their populations.

A proximity card or prox card also known as a key card or keycard is a contactless smart card which can be read without inserting it into a reader device, as required by earlier magnetic stripe cards such as credit cards and contact type smart cards. The proximity cards are part of the contactless card technologies. Held near an electronic reader for a moment they enable the identification of an encoded number. The reader usually produces a beep or other sound to indicate the card has been read.

EMV is a payment method based on a technical standard for smart payment cards and for payment terminals and automated teller machines which can accept them. EMV stands for "Europay, Mastercard, and Visa", the three companies that created the standard.
ISO/IEC 7813 is an international standard codified by the International Organization for Standardization and International Electrotechnical Commission that defines properties of financial transaction cards, such as ATM or credit cards.
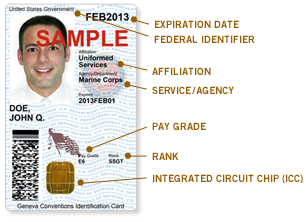
The common access card, also commonly referred to as the CAC, is the standard identification for active duty United States defense personnel. The card itself is a smart card about the size of a credit card. Defense personnel that use the CAC include the Selected Reserve and National Guard, United States Department of Defense (DoD) civilian employees, United States Coast Guard (USCG) civilian employees and eligible DoD and USCG contractor personnel. It is also the principal card used to enable physical access to buildings and controlled spaces, and it provides access to defense computer networks and systems. It also serves as an identification card under the Geneva Conventions. In combination with a personal identification number, a CAC satisfies the requirement for two-factor authentication: something the user knows combined with something the user has. The CAC also satisfies the requirements for digital signature and data encryption technologies: authentication, integrity and non-repudiation.
HID Global is an American manufacturer of secure identity products. The company is an independent subsidiary of Assa Abloy, a multinational door and access control conglomerate. Björn Lidefelt was appointed CEO on 27 January 2020. He succeeded Stefan Widing, who led HID Global for over four years.
The Wiegand interface is a de facto wiring standard which arose from the popularity of Wiegand effect card readers in the 1980s. It is commonly used to connect a card swipe mechanism to the rest of an access control system. The sensor in such a system is often a "Wiegand wire", based on the Wiegand effect, discovered by John R. Wiegand. A Wiegand-compatible reader is normally connected to a Wiegand-compatible security panel.

Payment cards are part of a payment system issued by financial institutions, such as a bank, to a customer that enables its owner to access the funds in the customer's designated bank accounts, or through a credit account and make payments by electronic transfer with a payment terminal and access automated teller machines (ATMs). Such cards are known by a variety of names, including bank cards, ATM cards, client cards, key cards or cash cards.

The Transportation Worker Identification Credential program is a Transportation Security Administration (TSA) and U.S. Coast Guard initiative in the United States. The TWIC program provides a tamper-resistant biometric credential to maritime workers requiring unescorted access to secure areas of port facilities, outer continental shelf facilities, certain manufacturing facilities, and vessels regulated under the Maritime Transportation Security Act of 2002, or MTSA, and all U.S. Coast Guard credentialed merchant mariners. As of May 2014, there were 2,999,058 people enrolled in the program. Those seeking unescorted access to secure areas aboard affected vessels, and all Coast Guard credentialed merchant mariners, must obtain a TWIC. The new measures were fully implemented on April 15, 2009. To obtain a TWIC, an individual must provide biographic and biometric information such as fingerprints, sit for a digital photograph and successfully pass a security threat assessment conducted by TSA.
A card reader is a data input device that reads data from a card-shaped storage medium and provides the data to a computer. Card readers can acquire data from a card via a number of methods, including: optical scanning of printed text or barcodes or holes on punched cards, electrical signals from connections made or interrupted by a card's punched holes or embedded circuitry, or electronic devices that can read plastic cards embedded with either a magnetic strip, computer chip, RFID chip, or another storage medium.
A contactless smart card is a contactless credential whose dimensions are credit card size. Its embedded integrated circuits can store data and communicate with a terminal via NFC. Commonplace uses include transit tickets, bank cards and passports.
A keycard lock is a lock operated by a keycard, a flat, rectangular plastic card. The card typically, but not always, has identical dimensions to that of a credit card, that is ID-1 format. The card stores a physical or digital pattern that the door mechanism accepts before disengaging the lock.

Touch Memory is an electronic identification device packaged in a coin-shaped stainless steel container. Touch memory is accessed when a touch probe comes into contact with a memory button.
An MM code is a "machine-readable modulated" feature that has been added to German debit cards during manufacture as an anti-counterfeiting measure since 1979. It was developed by "Gesellschaft für Automation und Organisation" in Munich for the German ec-Card system and MM verification devices have been added to German ATMs from 1982 onwards. If a payment card contains an MM code as well as a magnetic stripe, any fraudster who counterfeits the card but fails to read and duplicate the MM code onto the copy will be detected when trying to use the counterfeit in a German automated teller machine.

The Wiegand effect is a nonlinear magnetic effect, named after its discoverer John R. Wiegand, produced in specially annealed and hardened wire called Wiegand wire.

A card security code is a series of numbers that, in addition to the bank card number, is printed on a credit or debit card. The CSC is used as a security feature for card not present transactions, where a personal identification number (PIN) cannot be manually entered by the cardholder. It was instituted to reduce the incidence of credit card fraud. Unlike the card number, the CSC is deliberately not embossed, so that it is not read when using a mechanical credit card imprinter which will only pick up embossed numbers.

A campus credential, more commonly known as a campus card or a campus ID card is an identification document certifying the status of students, faculty, staff or other constituents as members of the institutional community and eligible for access to services and resources. Campus credentials are typically valid for the duration of a student's enrollment or an employee's service.
The term digital card can refer to a physical item, such as a memory card on a camera, or, increasingly since 2017, to the digital content hosted as a virtual card or cloud card, as a digital virtual representation of a physical card. They share a common purpose: Identity Management, Credit card, Debit card or driver license. A non-physical digital card, unlike a Magnetic stripe card can emulate (imitate) any kind of card.














