Malware is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types.
Ransomware is a type of cryptovirological malware that permanently blocks access to the victim's personal data unless a "ransom" is paid. While some simple ransomware may lock the system without damaging any files, more advanced malware uses a technique called cryptoviral extortion. It encrypts the victim's files, making them inaccessible, and demands a ransom payment to decrypt them. In a properly implemented cryptoviral extortion attack, recovering the files without the decryption key is an intractable problem, and difficult-to-trace digital currencies such as paysafecard or Bitcoin and other cryptocurrencies are used for the ransoms, making tracing and prosecuting the perpetrators difficult.
PGPCoder or GPCode is a trojan that encrypts files on the infected computer and then asks for a ransom in order to release these files, a type of behavior dubbed ransomware or cryptovirology.
Cryptovirology refers to the study of cryptography use in malware, such as ransomware and asymmetric backdoors. Traditionally, cryptography and its applications are defensive in nature, and provide privacy, authentication, and security to users. Cryptovirology employs a twist on cryptography, showing that it can also be used offensively. It can be used to mount extortion based attacks that cause loss of access to information, loss of confidentiality, and information leakage, tasks which cryptography typically prevents.
The CryptoLocker ransomware attack was a cyberattack using the CryptoLocker ransomware that occurred from 5 September 2013 to late May 2014. The attack utilized a trojan that targeted computers running on Microsoft Windows, and was believed to have first been posted to the Internet on 5 September 2013. It propagated via infected email attachments, and via an existing Gameover ZeuS botnet. When activated, the malware encrypted certain types of files stored on local and mounted network drives using RSA public-key cryptography, with the private key stored only on the malware's control servers. The malware then displayed a message which offered to decrypt the data if a payment was made by a stated deadline, and it threatened to delete the private key if the deadline passes. If the deadline was not met, the malware offered to decrypt data via an online service provided by the malware's operators, for a significantly higher price in bitcoin. There was no guarantee that payment would release the encrypted content.
TeslaCrypt was a ransomware trojan. It is now defunct, and its master key was released by the developers.
Linux.Encoder is considered to be the first ransomware Trojan targeting computers running Linux. There are additional variants of this Trojan that target other Unix and Unix-like systems. Discovered on November 5, 2015, by Dr. Web, this malware affected at least tens of Linux users.

KeRanger is a ransomware trojan horse targeting computers running macOS. Discovered on March 4, 2016, by Palo Alto Networks, it affected more than 7,000 Mac users.
TorrentLocker is a ransomware trojan targeting Microsoft Windows. It was first observed in February 2014, with at least five of its major releases made available by December 2014. The malware encrypts the victim's files in a similar manner to CryptoLocker by implementing symmetric block cipher AES where the key is encrypted with an asymmetric cipher.
macOS malware includes viruses, trojan horses, worms and other types of malware that affect macOS, Apple's current operating system for Macintosh computers. macOS is said to rarely suffer malware or virus attacks, and has been considered less vulnerable than Windows. There is a frequent release of system software updates to resolve vulnerabilities. Utilities are also available to find and remove malware.

Locky is ransomware malware released in 2016. It is delivered by email with an attached Microsoft Word document that contains malicious macros. When the user opens the document, it appears to be full of gibberish, and includes the phrase "Enable macro if data encoding is incorrect," a social engineering technique. If the user does enable macros, they save and run a binary file that downloads the actual encryption Trojan, which will encrypt all files that match particular extensions. Filenames are converted to a unique 16 letter and number combination. Initially, only the .locky file extension was used for these encrypted files. Subsequently, other file extensions have been used, including .zepto, .odin, .aesir, .thor, and .zzzzz. After encryption, a message instructs them to download the Tor browser and visit a specific criminal-operated Web site for further information.

Petya is a family of encrypting malware that was first discovered in 2016. The malware targets Microsoft Windows–based systems, infecting the master boot record to execute a payload that encrypts a hard drive's file system table and prevents Windows from booting. It subsequently demands that the user make a payment in Bitcoin in order to regain access to the system.
Hitler-Ransomware, or Hitler-Ransonware [sic], is a form of ransomware created in 2016 originating in Germany. It requests payment within one hour; otherwise, it will delete files from the infected computer.

Kirk Ransomware, or Kirk, is malware. It encrypts files on an infected computer and demands payment for decryption in the cryptocurrency Monero. The ransomware was first discovered in 2017, by Avast researcher Jakub Kroustek.
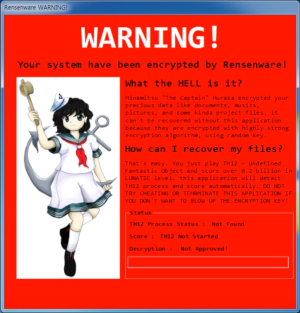
Rensenware is ransomware that infects Windows computers. It was created as a joke by Kangjun Heo and first appeared in 2017. Rensenware is unusual as an example of ransomware in that it does not request the user pay the creator of the virus to decrypt their files, instead requiring the user to achieve a required number of points in the bullet hell game Touhou Seirensen ~ Undefined Fantastic Object before any decryption can take place. The main window displays Minamitsu Murasa, a character from the game. Heo released a patch that neutralizes Rensenware after the malware gained attention.
Ryuk is a type of ransomware known for targeting large, public-entity Microsoft Windows cybersystems. It typically encrypts data on an infected system, rendering the data inaccessible until a ransom is paid in untraceable bitcoin. Ryuk is believed to be used by two or more criminal groups, most likely Russian or Ukrainian, who target organizations rather than individual consumers.
Thanos is a malicious ransomware. According to the FBI, it was created by Venezuelan-French cardiologist Moises Luis Zagala Gonzalez. The malware first appeared around February 2020, and is written in the programming language C#. It works by fully encrypting the victim's files and asking for a specific sum of money, usually via CryptoCurrency such as Bitcoin. The ransomware is known to be highly advanced; evading antivirus software by rebooting the computer on safeboot. It also has a customisable interface where the attacker can modify the ransomware message, choose whether the malware will self-delete after attacking, and more. Zagala advertised the ransomware on various darknet marketplaces, where Cybercriminals are known to meet. Zagala also created Jigsaw v.2., a successor to the Jigsaw ransomware, which worked similarly to Thanos by encrypting the victim's files and asking for a ransom. This time, however, if the user tried to remove the malware from their computer or tried to reboot it, the software would "punish" the victim by erasing the entire harddrive. Emisoft released a decryptor key for Jigsaw v.2. in 2019.
Hive was a ransomware as a service (RaaS) operation carried out by the eponymous cybercrime organization between June 2021 and January 2023. The group's purpose was to attack mainly public institutions to subsequently demand ransom for release of hijacked data.

LockBit is a cybercriminal group proposing ransomware as a service (RaaS). Software developed by the group enables malicious actors who are willing to pay for using it to carry out attacks in two tactics where they not only encrypt the victim's data and demand payment of a ransom, but also threaten to leak it publicly if their demands are not met.
BlackCat, also known as ALPHV and Noberus, is a ransomware family written in Rust. It made its first appearance in November 2021. By extension, it is also the name of the threat actor(s) who exploit it.






