Related Research Articles

Internet Protocol version 6 (IPv6) is the most recent version of the Internet Protocol (IP), the communications protocol that provides an identification and location system for computers on networks and routes traffic across the Internet. IPv6 was developed by the Internet Engineering Task Force (IETF) to deal with the long-anticipated problem of IPv4 address exhaustion, and was intended to replace IPv4. In December 1998, IPv6 became a Draft Standard for the IETF, which subsequently ratified it as an Internet Standard on 14 July 2017.
In computing, Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts packets of data to provide secure encrypted communication between two computers over an Internet Protocol network. It is used in virtual private networks (VPNs).
Virtual private network (VPN) is a network architecture for virtually extending a private network across one or multiple other networks which are either untrusted or need to be isolated.
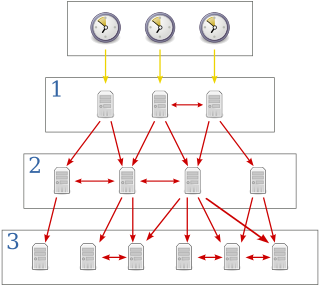
The Network Time Protocol (NTP) is a networking protocol for clock synchronization between computer systems over packet-switched, variable-latency data networks. In operation since before 1985, NTP is one of the oldest Internet protocols in current use. NTP was designed by David L. Mills of the University of Delaware.
In computing, Internet Key Exchange is the protocol used to set up a security association (SA) in the IPsec protocol suite. IKE builds upon the Oakley protocol and ISAKMP. IKE uses X.509 certificates for authentication ‒ either pre-shared or distributed using DNS ‒ and a Diffie–Hellman key exchange to set up a shared session secret from which cryptographic keys are derived. In addition, a security policy for every peer which will connect must be manually maintained.
OpenVPN is a virtual private network (VPN) system that implements techniques to create secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. It implements both client and server applications.
Address space layout randomization (ASLR) is a computer security technique involved in preventing exploitation of memory corruption vulnerabilities. In order to prevent an attacker from reliably redirecting code execution to, for example, a particular exploited function in memory, ASLR randomly arranges the address space positions of key data areas of a process, including the base of the executable and the positions of the stack, heap and libraries.
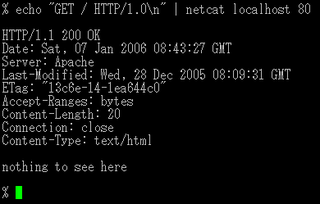
netcat is a computer networking utility for reading from and writing to network connections using TCP or UDP. The command is designed to be a dependable back-end that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and investigation tool, since it can produce almost any kind of connection its user could need and has a number of built-in capabilities.

NDISwrapper is a free software driver wrapper that enables the use of Windows XP network device drivers on Linux operating systems. NDISwrapper works by implementing the Windows kernel and NDIS APIs and dynamically linking Windows network drivers to this implementation. As a result, it only works on systems based on the instruction set architectures supported by Windows, namely IA-32 and x86-64.
ISATAP is an IPv6 transition mechanism meant to transmit IPv6 packets between dual-stack nodes on top of an IPv4 network. It is defined in the informational RFC 5214.
In computer networking, TUN and TAP are kernel virtual network devices. Being network devices supported entirely in software, they differ from ordinary network devices which are backed by physical network adapters.

FreeBSD is a free and open-source Unix-like operating system descended from the Berkeley Software Distribution (BSD). The first version of FreeBSD was released in 1993 developed from 386BSD and the current version runs on IA-32, x86-64, ARM, PowerPC and RISC-V processors. The project is supported and promoted by the FreeBSD Foundation.
A Bluetooth stack is software that is an implementation of the Bluetooth protocol stack.
An IPv6 transition mechanism is a technology that facilitates the transitioning of the Internet from the Internet Protocol version 4 (IPv4) infrastructure in use since 1983 to the successor addressing and routing system of Internet Protocol Version 6 (IPv6). As IPv4 and IPv6 networks are not directly interoperable, transition technologies are designed to permit hosts on either network type to communicate with any other host.
The deployment of IPv6, the latest version of the Internet Protocol (IP), has been in progress since the mid-2000s. IPv6 was designed as the successor protocol for IPv4 with an expanded addressing space. IPv4, which has been in use since 1982, is in the final stages of exhausting its unallocated address space, but still carries most Internet traffic.

OpenBSD is a security-focused, free and open-source, Unix-like operating system based on the Berkeley Software Distribution (BSD). Theo de Raadt created OpenBSD in 1995 by forking NetBSD 1.0. The OpenBSD project emphasizes portability, standardization, correctness, proactive security, and integrated cryptography.
The Stream Control Transmission Protocol (SCTP) is a computer networking communications protocol in the transport layer of the Internet protocol suite. Originally intended for Signaling System 7 (SS7) message transport in telecommunication, the protocol provides the message-oriented feature of the User Datagram Protocol (UDP), while ensuring reliable, in-sequence transport of messages with congestion control like the Transmission Control Protocol (TCP). Unlike UDP and TCP, the protocol supports multihoming and redundant paths to increase resilience and reliability.
The OpenBSD Cryptographic Framework (OCF) is a service virtualization layer for the uniform management of cryptographic hardware by an operating system. It is part of the OpenBSD Project, having been included in the operating system since OpenBSD 2.8. Like other OpenBSD projects such as OpenSSH, it has been ported to other systems based on Berkeley Unix such as FreeBSD and NetBSD, and to Solaris and Linux. One of the Linux ports is supported by Intel for use with its proprietary cryptographic software and hardware to provide hardware-accelerated SSL encryption for the open source Apache HTTP Server.

Open vSwitch (OVS) is an open-source implementation of a distributed virtual multilayer switch. The main purpose of Open vSwitch is to provide a switching stack for hardware virtualization environments, while supporting multiple protocols and standards used in computer networks.
WireGuard is a communication protocol and free and open-source software that implements encrypted virtual private networks (VPNs). It aims to be lighter and better performing than IPsec and OpenVPN, two common tunneling protocols. The WireGuard protocol passes traffic over UDP.
References
- ↑ Hagen, Silvia (May 17, 2006). IPv6 Essentials. O'Reilly Media. ISBN 9780596553418.
- ↑ "The announcement of the conclusion of the KAME project". KAME project. 2005-11-07. Retrieved 2019-03-17.
- ↑ Kazu YAMAMOTO (July 1999). "Page 15: KAME Project". Archived from the original on 2008-07-05.
- ↑ Roy, Vincent (12 October 2004), Benchmarks for Native IPsec in the 2.6 Kernel, Linux Journal , retrieved 2019-03-17
- ↑ "TAHI Project: Test and Verification for IPv6. Since 1998". 2013-01-01. Archived from the original on 2017-01-27.
- ↑ YOSHIFUJI Hideaki (2010-03-07). "USAGI Project - Linux IPv6 Development Project" . Retrieved 2019-03-17.