External links
| | This cryptography-related article is a stub. You can help Wikipedia by expanding it. |
ORYX is an encryption algorithm used in cellular communications in order to protect data traffic. It is a stream cipher designed to have a very strong 96-bit key strength with a way to reduce the strength to 32-bits for export. However, due to mistakes the actual strength is a trivial 16-bits and any signal can be cracked after the first 25–27 bytes. [1]
It is one of the four cryptographic primitives standardized by TIA's for use in their digital cellular communications standards TDMA and CDMA. [1]
ORYX is a simple stream cipher based on binary linear-feedback shift registers (LFSRs) to protect cellular data transmissions (for wireless data services).
The cipher ORYX has four components: three 32-bit LFSRs which labeled as LFSRA, LFSRB and LFSRK, and an S-box containing a known permutation P of the integer values 0 to 255.
The feedback function for LFSRK is defined as:
Lt + 32 = Lt + 28 ⊕ Lt + 19 ⊕ Lt + 18 ⊕ Lt + 16 ⊕ Lt + 14 ⊕ Lt + 11 ⊕ Lt + 10 ⊕ Lt + 9 ⊕ Lt + 6 ⊕ Lt + 5 ⊕ Lt + 1 ⊕ Lt
The feedback functions for LFSRA are defined as:
Lt + 32 = Lt + 26 ⊕ Lt + 23 ⊕ Lt + 22 ⊕ Lt + 16 ⊕ Lt + 12 ⊕ Lt + 11 ⊕ Lt + 10 ⊕ Lt + 8 ⊕ Lt + 7 ⊕ Lt + 5 ⊕ Lt + 4 ⊕ Lt + 2 ⊕ Lt + 1 ⊕ Lt
and
Lt + 32 = Lt + 27 ⊕ Lt + 26 ⊕ Lt + 25 ⊕ Lt + 24 ⊕ Lt + 23 ⊕ Lt + 22 ⊕ Lt + 17 ⊕ Lt + 13 ⊕ Lt + 11 ⊕ Lt + 10 ⊕ Lt + 9 ⊕ Lt + 8 ⊕ Lt + 7 ⊕ Lt + 2 ⊕ Lt + 1 ⊕ Lt
The feedback function for LFSRB is:
Lt + 32 = Lt + 31 ⊕ Lt + 21 ⊕ Lt + 20 ⊕ Lt + 16 ⊕ Lt + 15 ⊕ Lt + 6 ⊕ Lt + 3 ⊕ Lt + 1 ⊕ Lt
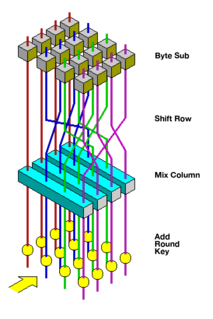
The Advanced Encryption Standard (AES), also known by its original name Rijndael, is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001.
Blowfish is a symmetric-key block cipher, designed in 1993 by Bruce Schneier and included in many cipher suites and encryption products. Blowfish provides a good encryption rate in software, and no effective cryptanalysis of it has been found to date. However, the Advanced Encryption Standard (AES) now receives more attention, and Schneier recommends Twofish for modern applications.
In cryptography, a block cipher is a deterministic algorithm operating on fixed-length groups of bits, called blocks. They are specified elementary components in the design of many cryptographic protocols and are widely used to the encryption of large amounts of data, including data exchange protocols. It uses blocks as an unvarying transformation.

The Data Encryption Standard is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits makes it too insecure for applications, it has been highly influential in the advancement of cryptography.

In cryptography, the International Data Encryption Algorithm (IDEA), originally called Improved Proposed Encryption Standard (IPES), is a symmetric-key block cipher designed by James Massey of ETH Zurich and Xuejia Lai and was first described in 1991. The algorithm was intended as a replacement for the Data Encryption Standard (DES). IDEA is a minor revision of an earlier cipher Proposed Encryption Standard (PES).

A stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream). In a stream cipher, each plaintext digit is encrypted one at a time with the corresponding digit of the keystream, to give a digit of the ciphertext stream. Since encryption of each digit is dependent on the current state of the cipher, it is also known as state cipher. In practice, a digit is typically a bit and the combining operation is an exclusive-or (XOR).
The Advanced Encryption Standard (AES), the symmetric block cipher ratified as a standard by National Institute of Standards and Technology of the United States (NIST), was chosen using a process lasting from 1997 to 2000 that was markedly more open and transparent than its predecessor, the Data Encryption Standard (DES). This process won praise from the open cryptographic community, and helped to increase confidence in the security of the winning algorithm from those who were suspicious of backdoors in the predecessor, DES.
Articles related to cryptography include:
In cryptography, an S-box (substitution-box) is a basic component of symmetric key algorithms which performs substitution. In block ciphers, they are typically used to obscure the relationship between the key and the ciphertext, thus ensuring Shannon's property of confusion. Mathematically, an S-box is a vectorial Boolean function.
In cryptography, Skipjack is a block cipher—an algorithm for encryption—developed by the U.S. National Security Agency (NSA). Initially classified, it was originally intended for use in the controversial Clipper chip. Subsequently, the algorithm was declassified.

The GOST block cipher (Magma), defined in the standard GOST 28147-89, is a Soviet and Russian government standard symmetric key block cipher with a block size of 64 bits. The original standard, published in 1989, did not give the cipher any name, but the most recent revision of the standard, GOST R 34.12-2015, specifies that it may be referred to as Magma. The GOST hash function is based on this cipher. The new standard also specifies a new 128-bit block cipher called Kuznyechik.
In cryptography, the Cellular Message Encryption Algorithm (CMEA) is a block cipher which was used for securing mobile phones in the United States. CMEA is one of four cryptographic primitives specified in a Telecommunications Industry Association (TIA) standard, and is designed to encrypt the control channel, rather than the voice data. In 1997, a group of cryptographers published attacks on the cipher showing it had several weaknesses which give it a trivial effective strength of a 24-bit to 32-bit cipher. Some accusations were made that the NSA had pressured the original designers into crippling CMEA, but the NSA has denied any role in the design or selection of the algorithm. The ECMEA and SCEMA ciphers are derived from CMEA.
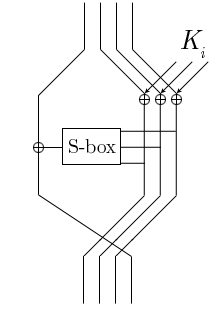
In cryptography, MacGuffin is a block cipher created in 1994 by Bruce Schneier and Matt Blaze at a Fast Software Encryption workshop. It was intended as a catalyst for analysis of a new cipher structure, known as Generalized Unbalanced Feistel Networks (GUFNs). The cryptanalysis proceeded very quickly, so quickly that the cipher was broken at the same workshop by Vincent Rijmen and Bart Preneel.
In cryptography, nothing-up-my-sleeve numbers are any numbers which, by their construction, are above suspicion of hidden properties. They are used in creating cryptographic functions such as hashes and ciphers. These algorithms often need randomized constants for mixing or initialization purposes. The cryptographer may wish to pick these values in a way that demonstrates the constants were not selected for a nefarious purpose, for example, to create a backdoor to the algorithm. These fears can be allayed by using numbers created in a way that leaves little room for adjustment. An example would be the use of initial digits from the number π as the constants. Using digits of π millions of places after the decimal point would not be considered trustworthy because the algorithm designer might have selected that starting point because it created a secret weakness the designer could later exploit.
Strong cryptography or cryptographically strong are general terms applied to cryptographic systems or components that are considered highly resistant to cryptanalysis.

Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages; various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation are central to modern cryptography. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, electrical engineering, communication science, and physics. Applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications.
The following outline is provided as an overview of and topical guide to cryptography:
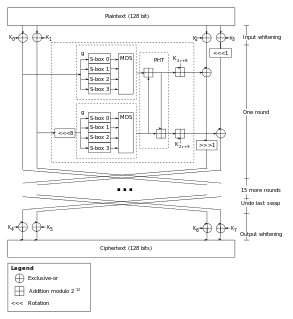
In cryptography, Twofish is a symmetric key block cipher with a block size of 128 bits and key sizes up to 256 bits. It was one of the five finalists of the Advanced Encryption Standard contest, but it was not selected for standardization. Twofish is related to the earlier block cipher Blowfish.

Simon is a family of lightweight block ciphers publicly released by the National Security Agency (NSA) in June 2013. Simon has been optimized for performance in hardware implementations, while its sister algorithm, Speck, has been optimized for software implementations.