In cryptography, a block cipher is a deterministic algorithm that operates on fixed-length groups of bits, called blocks. Block ciphers are the elementary building blocks of many cryptographic protocols. They are ubiquitous in the storage and exchange of data, where such data is secured and authenticated via encryption.

A stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream). In a stream cipher, each plaintext digit is encrypted one at a time with the corresponding digit of the keystream, to give a digit of the ciphertext stream. Since encryption of each digit is dependent on the current state of the cipher, it is also known as state cipher. In practice, a digit is typically a bit and the combining operation is an exclusive-or (XOR).
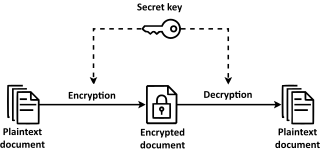
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. The keys may be identical, or there may be a simple transformation to go between the two keys. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. The requirement that both parties have access to the secret key is one of the main drawbacks of symmetric-key encryption, in comparison to public-key encryption. However, symmetric-key encryption algorithms are usually better for bulk encryption. With exception of the one-time pad they have a smaller key size, which means less storage space and faster transmission. Due to this, asymmetric-key encryption is often used to exchange the secret key for symmetric-key encryption.
A chosen-ciphertext attack (CCA) is an attack model for cryptanalysis where the cryptanalyst can gather information by obtaining the decryptions of chosen ciphertexts. From these pieces of information the adversary can attempt to recover the secret key used for decryption.
Articles related to cryptography include:
A5/1 is a stream cipher used to provide over-the-air communication privacy in the GSM cellular telephone standard. It is one of several implementations of the A5 security protocol. It was initially kept secret, but became public knowledge through leaks and reverse engineering. A number of serious weaknesses in the cipher have been identified.

MIFARE is a series of integrated circuit (IC) chips used in contactless smart cards and proximity cards.
Stream ciphers, where plaintext bits are combined with a cipher bit stream by an exclusive-or operation (xor), can be very secure if used properly. However, they are vulnerable to attacks if certain precautions are not followed:

The EasyCard is a contactless smartcard system operated by the EasyCard Corporation, which was previously named the "Taipei Smart Card Corporation", for payment on the Taipei Metro, buses, and other public transport services in Taipei since June 2002, and its usage has since expanded to other public transport services throughout Taiwan, as well as multiple kinds of businesses. Its use has also since been expanded to include convenience stores, department stores, supermarkets, taxis, and other retailers since 1 April 2010. Like conventional electronic fare systems, the card employs RFID technology to operate without physical contact. They are available for purchase at all metro stations and all chain convenience stores.
Java Card OpenPlatform (JCOP) is a smart card operating system for the Java Card platform developed by IBM Zürich Research Laboratory. On 31 January 2006 the development and support responsibilities transferred to the IBM Smart Card Technology team in Böblingen, Germany. Since July 2007 support and development activities for the JCOP operating system on NXP / Philips silicon are serviced by NXP Semiconductors.

VEST (Very Efficient Substitution Transposition) ciphers are a set of families of general-purpose hardware-dedicated ciphers that support single pass authenticated encryption and can operate as collision-resistant hash functions designed by Sean O'Neil, Benjamin Gittins and Howard Landman. VEST cannot be implemented efficiently in software.
Grain is a stream cipher submitted to eSTREAM in 2004 by Martin Hell, Thomas Johansson and Willi Meier. It has been selected for the final eSTREAM portfolio for Profile 2 by the eSTREAM project. Grain is designed primarily for restricted hardware environments. It accepts an 80-bit key and a 64-bit IV. The specifications do not recommend a maximum length of output per pair. A number of potential weaknesses in the cipher have been identified and corrected in Grain 128a which is now the recommended cipher to use for hardware environments providing both 128bit security and authentication.
The Texas Instruments digital signature transponder (DST) is a cryptographically enabled radio-frequency identification (RFID) device used in a variety of wireless authentication applications. The largest deployments of the DST include the Exxon-Mobil Speedpass payment system, as well as a variety of vehicle immobilizer systems used in many late model Ford, Lincoln, Mercury, Toyota, Nissan, Kia, Hyundai and Tesla vehicles.

Rejsekort is an electronic ticket system for public transport in Denmark. The system is a collaborative work between DSB, HUR, Ørestadsselskabet, and various regional bus companies, and work on it started on August 18, 2003. In June 2005, Thales Group and Accenture were chosen as suppliers.

The Breeze Card is an American stored value smart card that passengers use as part of an automated fare collection system which the Metropolitan Atlanta Rapid Transit Authority (MARTA) introduced to the general public in early October 2006. The card automatically debits the cost of the passenger’s ride when placed on or near the Breeze Target at the fare gate. Transit riders are able to add value or time-based passes to the card at Breeze Vending Machines (BVM) located at all MARTA stations. The major phases of MARTA's Breeze transformation took place before July 1, 2007 when customers were still able to purchase TransCards from ridestores or their employers. They were also able to obtain paper transfers from bus drivers to access the train. As of July 1, 2007 the TransCard and the paper transfers were discontinued and patrons now use a Breeze Card or ticket to access the system, and all transfers are loaded on the card. Breeze Vending Machines (BVM) distribute regional transit provider passes The Breeze Card employs passive RFID technology currently in use in many transit systems around the world.
Massachusetts Bay Transportation Authority v. Anderson, et al., Civil Action No. 08-11364, was a challenge brought by the Massachusetts Bay Transportation Authority (MBTA) to prevent three Massachusetts Institute of Technology (MIT) students from publicly presenting a security vulnerability they discovered in the MBTA's CharlieCard automated fare collection system. The case concerns the extent to which the disclosure of a computer security flaw is a form of free speech protected by the First Amendment to the United States Constitution.

The TFI Leap Card is a contactless smart card for automated fare collection overseen by Transport for Ireland (TFI). It was introduced in the Greater Dublin area in 2011 for Luas, DART, Iarnród Éireann and Dublin Bus, but acceptance has significantly expanded, and it is now accepted in cities nationwide and on some longer distance commuter routes. Initially, Leap Cards offered only a pre-paid electronic wallet system for single-trip fares; since May 2014, it has also been possible to load it with weekly, monthly and annual subscriptions. In September 2017, there were over 2.5 million Leap Card users according to the National Transport Authority. The Leap Card is the result of many years' work by the Railway Procurement Agency and the National Transport Authority as part of the rollout of an integrated ticketing scheme for public transport in Dublin city. Fares are generally discounted compared to cash prices, and integrated ticketing is offered in the Dublin area via a flat fare system across all modes of transport. The minimum top-up for the card is currently €5, and it can be topped up via iPhone/Android app, at LUAS or DART ticketing machines, and in convenience stores offering Payzone services.

Simon is a family of lightweight block ciphers publicly released by the National Security Agency (NSA) in June 2013. Simon has been optimized for performance in hardware implementations, while its sister algorithm, Speck, has been optimized for software implementations.

Karsten Nohl is a German cryptography expert and hacker. His areas of research include Global System for Mobile Communications (GSM) security, radio-frequency identification (RFID) security, and privacy protection.

Proxmark3 is a multi-purpose hardware tool for radio-frequency identification (RFID) security analysis, research and development. It supports both high frequency and low frequency proximity cards and allows users to read, emulate, fuzz, and brute force the majority of RFID protocols.











