In cryptography, a block cipher is a deterministic algorithm operating on fixed-length groups of bits, called blocks. They are specified elementary components in the design of many cryptographic protocols and are widely used to the encryption of large amounts of data, including data exchange protocols. It uses blocks as an unvarying transformation.
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. The keys may be identical, or there may be a simple transformation to go between the two keys. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. The requirement that both parties have access to the secret key is one of the main drawbacks of symmetric-key encryption, in comparison to public-key encryption .However, symmetric-key encryption are usually better for bulk encryption. They have a smaller file size which allows for less storage space and faster transmission. Due to this, asymmetric-encryption is often used to exchange the secret key for symmetric-key encryption.
In cryptography, a block cipher mode of operation is an algorithm that uses a block cipher to provide information security such as confidentiality or authenticity. A block cipher by itself is only suitable for the secure cryptographic transformation of one fixed-length group of bits called a block. A mode of operation describes how to repeatedly apply a cipher's single-block operation to securely transform amounts of data larger than a block.

In cryptography, RC6 is a symmetric key block cipher derived from RC5. It was designed by Ron Rivest, Matt Robshaw, Ray Sidney, and Yiqun Lisa Yin to meet the requirements of the Advanced Encryption Standard (AES) competition. The algorithm was one of the five finalists, and also was submitted to the NESSIE and CRYPTREC projects. It was a proprietary algorithm, patented by RSA Security.
In cryptography, a message authentication code (MAC), sometimes known as a tag, is a short piece of information used for authenticating a message. In other words, to confirm that the message came from the stated sender and has not been changed. The MAC value protects a message's data integrity, as well as its authenticity, by allowing verifiers to detect any changes to the message content.
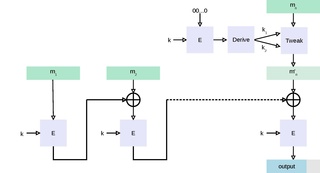
One-key MAC (OMAC) is a message authentication code constructed from a block cipher much like the CBC-MAC algorithm.
Offset codebook mode is an authenticated encryption mode of operation for cryptographic block ciphers. OCB mode was designed by Phillip Rogaway, who credits Mihir Bellare, John Black, and Ted Krovetz with assistance and comments on the designs. It is based on the integrity-aware parallelizeable mode (IAPM) of authenticated encryption by Charanjit S. Jutla. The OCB2 version was proven insecure, while the original OCB1 as well as OCB3 from 2011 are still considered secure.
CCM mode is a mode of operation for cryptographic block ciphers. It is an authenticated encryption algorithm designed to provide both authentication and confidentiality. CCM mode is only defined for block ciphers with a block length of 128 bits.
Authenticated encryption (AE) and authenticated encryption with associated data (AEAD) are forms of encryption which simultaneously assure the confidentiality and authenticity of data.

In cryptography, a cipher block chaining message authentication code (CBC-MAC) is a technique for constructing a message authentication code from a block cipher. The message is encrypted with some block cipher algorithm in CBC mode to create a chain of blocks such that each block depends on the proper encryption of the previous block. This interdependence ensures that a change to any of the plaintext bits will cause the final encrypted block to change in a way that cannot be predicted or counteracted without knowing the key to the block cipher.
The Data Authentication Algorithm (DAA) is a former U.S. government standard for producing cryptographic message authentication codes. DAA is defined in FIPS PUB 113, which was withdrawn on September 1, 2008. The algorithm is not considered secure by today's standards. According to the standard, a code produced by the DAA is called a Data Authentication Code (DAC). The algorithm chain encrypts the data, with the last cipher block truncated and used as the DAC.
Disk encryption is a special case of data at rest protection when the storage medium is a sector-addressable device. This article presents cryptographic aspects of the problem. For an overview, see disk encryption. For discussion of different software packages and hardware devices devoted to this problem, see disk encryption software and disk encryption hardware.
EAX mode (encrypt-then-authenticate-then-translate) is a mode of operation for cryptographic block ciphers. It is an Authenticated Encryption with Associated Data (AEAD) algorithm designed to simultaneously provide both authentication and privacy of the message with a two-pass scheme, one pass for achieving privacy and one for authenticity for each block.
In cryptography, Galois/Counter Mode (GCM) is a mode of operation for symmetric-key cryptographic block ciphers which is widely adopted for its performance. GCM throughput rates for state-of-the-art, high-speed communication channels can be achieved with inexpensive hardware resources. The operation is an authenticated encryption algorithm designed to provide both data authenticity (integrity) and confidentiality. GCM is defined for block ciphers with a block size of 128 bits. Galois Message Authentication Code (GMAC) is an authentication-only variant of the GCM which can form an incremental message authentication code. Both GCM and GMAC can accept initialization vectors of arbitrary length.

In cryptography, a nonce is an arbitrary number that can be used just once in a cryptographic communication. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused in replay attacks. They can also be useful as initialization vectors and in cryptographic hash functions.
In cryptography, key wrap constructions are a class of symmetric encryption algorithms designed to encapsulate (encrypt) cryptographic key material.the Key Wrap algorithms are intended for applications such as protecting keys while in untrusted storage or transmitting keys over untrusted communications networks. The constructions are typically built from standard primitives such as block ciphers and cryptographic hash functions.
In cryptography, format-preserving encryption (FPE), refers to encrypting in such a way that the output is in the same format as the input. The meaning of "format" varies. Typically only finite sets of characters are used; numeric, alphabetic or alphanumeric. For example:
The following outline is provided as an overview of and topical guide to cryptography:
Integrity-aware parallelizable mode (IAPM) is a mode of operation for cryptographic block ciphers. As its name implies, it allows for a parallel mode of operation for higher throughput.
ISO/IEC 9797-1Information technology – Security techniques – Message Authentication Codes (MACs) – Part 1: Mechanisms using a block cipher is an international standard that defines methods for calculating a message authentication code (MAC) over data.



