
The USA PATRIOT Act was a landmark Act of the United States Congress, signed into law by President George W. Bush. The formal name of the statute is the Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism Act of 2001, and the commonly used short name is a contrived acronym that is embedded in the name set forth in the statute.

Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizations, but it may also be carried out by corporations. Depending on each nation's laws and judicial systems, the legality of and the permission required to engage in mass surveillance varies. It is the single most indicative distinguishing trait of totalitarian regimes. It is often distinguished from targeted surveillance.
American Civil Liberties Union v. Ashcroft is a lawsuit filed on behalf of a formerly unknown Internet Service Provider (ISP) company under the pseudonym John Doe, Inc. by the American Civil Liberties Union against the U.S. federal government, by the Department of Justice under former U.S. Attorney General John Ashcroft.

End-to-end encryption (E2EE) is a method of implementing a secure communication system where only communicating users can participate. No one else, including the system provider, telecom providers, Internet providers or malicious actors, can access the cryptographic keys needed to read or send messages.

The Electronic Communications Privacy Act of 1986 (ECPA) was enacted by the United States Congress to extend restrictions on government wire taps of telephone calls to include transmissions of electronic data by computer, added new provisions prohibiting access to stored electronic communications, i.e., the Stored Communications Act, and added so-called pen trap provisions that permit the tracing of telephone communications . ECPA was an amendment to Title III of the Omnibus Crime Control and Safe Streets Act of 1968, which was primarily designed to prevent unauthorized government access to private electronic communications. The ECPA has been amended by the Communications Assistance for Law Enforcement Act (CALEA) of 1994, the USA PATRIOT Act (2001), the USA PATRIOT reauthorization acts (2006), and the FISA Amendments Act (2008).

The following are controversial invocations of the USA PATRIOT Act. The stated purpose of the Act is to "deter and punish terrorist acts in the United States and around the world, to enhance law enforcement investigatory tools, and for other purposes." One criticism of the Act is that "other purposes" often includes the detection and prosecution of non-terrorist alleged future crimes.

A national security letter (NSL) is an administrative subpoena issued by the United States government to gather information for national security purposes. NSLs do not require prior approval from a judge. The Stored Communications Act, Fair Credit Reporting Act, and Right to Financial Privacy Act authorize the United States government to seek such information that is "relevant" to an authorized national security investigation. By law, NSLs can request only non-content information, for example, transactional records and phone numbers dialed, but never the content of telephone calls or e-mails.

Christopher Soghoian is a privacy researcher and activist. He is currently working for Senator Ron Wyden as the senator’s Senior Advisor for Privacy & Cybersecurity. From 2012 to 2016, he was the principal technologist at the American Civil Liberties Union.

The Stored Communications Act is a law that addresses voluntary and compelled disclosure of "stored wire and electronic communications and transactional records" held by third-party Internet service providers (ISPs). It was enacted as Title II of the Electronic Communications Privacy Act of 1986 (ECPA).
The WikiLeaks-related Twitter court orders were United States Department of Justice 2703(d) orders accompanied by gag orders issued to Twitter in relation to ongoing investigations of WikiLeaks issued on 14 December 2010. The U.S. government sent Twitter a subpoena for information about Julian Assange and several other WikiLeaks-related persons, including Chelsea Manning. Twitter appealed against the accompanying gag order in order to be able to disclose its existence to its users, and was ultimately successful in its appeal.

PRISM is a code name for a program under which the United States National Security Agency (NSA) collects internet communications from various U.S. internet companies. The program is also known by the SIGAD US-984XN. PRISM collects stored internet communications based on demands made to internet companies such as Google LLC and Apple under Section 702 of the FISA Amendments Act of 2008 to turn over any data that match court-approved search terms. Among other things, the NSA can use these PRISM requests to target communications that were encrypted when they traveled across the internet backbone, to focus on stored data that telecommunication filtering systems discarded earlier, and to get data that is easier to handle.
Lavabit is an open-source encrypted webmail service, founded in 2004. The service suspended its operations on August 8, 2013, after the U.S. Federal Government ordered it to turn over its Secure Sockets Layer (SSL) private keys, in order to allow the government to spy on Edward Snowden's email.

Proposed reforms of mass surveillance by the United States are a collection of diverse proposals offered in response to the Global surveillance disclosures of 2013.

Former U.S. President Barack Obama favored some levels of mass surveillance. He has received some widespread criticism from detractors as a result. Due to his support of certain government surveillance, some critics have said his support violated acceptable privacy rights, while others dispute or attempt to provide justification for the expansion of surveillance initiatives under his administration.
A transparency report is a statement issued semesterly or annually by a company or government, which discloses a variety of statistics related to requests for user data, records, or content. Transparency reports generally disclose how frequently and under what authority governments have requested or demanded data or records over a certain period of time. This form of corporate transparency allows the public to discern how much user information governments have requested through search warrants, court orders, emergency requests, subpoenas, etc. Additionally, companies report data related to requests for user information regarding national security matters, including national security letters and FISA Requests. In 2010, Google was the first company to release a transparency report, with Twitter following in 2012. Additional companies began releasing transparency reports in light of the Edward Snowden leaks in 2013, and the number of companies issuing them has increased rapidly ever since. Additionally, the United States Intelligence Community began releasing their Annual Statistical Transparency Report in 2013, in an attempt to raise public opinion following the leaks. Today, transparency reports are issued by a variety of technology and communications companies, including Google, Microsoft, Verizon, AT&T, Twitter, Apple, Dropbox, Facebook, Yahoo, Uber, Amazon, T-Mobile, Discord, Reddit, and CloudFlare. As of July 2021, 88 companies have provided transparency reports. Due to the optional nature of transparency reporting, some companies' transparency reports include information related to the government's involvement in copyright takedowns, while others do not. Critics claim that these descrepencies in various companies' reports results in confusion rather than clarification regarding government requesting and censorship practices, and many agree that systematic transparency reporting practices should be implemented across every company that receives requests for user information or takedown notices. Additionally, companies are required by the government to report the number of national security requests they received in bands of 500 or 1000 (0-499) (0-999). Several companies and advocacy groups have lobbied the U.S. government to change this policy and allow the exact number of national security requests to be released, and Twitter is raising this issue in the ongoing legal battle,Twitter v. Garland.
The Calyx Institute is a New York-based 501(c)(3) research and education nonprofit organization formed to make privacy and digital security more accessible. It was founded in 2010 by Nicholas Merrill, Micah Anderson, and Kobi Snitz.
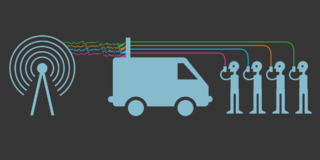
Cellphone surveillance may involve tracking, bugging, monitoring, eavesdropping, and recording conversations and text messages on mobile phones. It also encompasses the monitoring of people's movements, which can be tracked using mobile phone signals when phones are turned on.
Attempts, unofficially dubbed the "Crypto Wars", have been made by the United States (US) and allied governments to limit the public's and foreign nations' access to cryptography strong enough to thwart decryption by national intelligence agencies, especially the National Security Agency (NSA).
Microsoft Corp. v. United States, known on appeal to the U.S. Supreme Court as United States v. Microsoft Corp., 584 U.S. ___, 138 S. Ct. 1186 (2018), was a data privacy case involving the extraterritoriality of law enforcement seeking electronic data under the 1986 Stored Communications Act (SCA), Title II of the Electronic Communications Privacy Act of 1986 (ECPA), in light of modern computing and Internet technologies such as data centers and cloud storage.

Riseup is a volunteer-run social movement organization providing secure email, email lists, a VPN service, online chat, and other online services to support activists engaged in various social justice causes and opposition to capitalism. This organization was launched by activists in Seattle with borrowed equipment and a few users in 1999 or 2000, and quickly grew to millions of accounts.










