Related Research Articles

GNU GRUB is a boot loader package from the GNU Project. GRUB is the reference implementation of the Free Software Foundation's Multiboot Specification, which provides a user the choice to boot one of multiple operating systems installed on a computer or select a specific kernel configuration available on a particular operating system's partitions.

Unified Extensible Firmware Interface is a specification that defines the architecture of the platform firmware used for booting the computer hardware and its interface for interaction with the operating system. Examples of firmware that implement the specification are AMI Aptio, Phoenix SecureCore, TianoCore EDK II, InsydeH2O. UEFI replaces the BIOS which was present in the boot ROM of all personal computers that are IBM PC compatible, although it can provide backwards compatibility with the BIOS using CSM booting. Intel developed the original Extensible Firmware Interface (EFI) specification. Some of the EFI's practices and data formats mirror those of Microsoft Windows. In 2005, UEFI deprecated EFI 1.10.

The GUID Partition Table (GPT) is a standard for the layout of partition tables of a physical computer storage device, such as a hard disk drive or solid-state drive, using universally unique identifiers, which are also known as globally unique identifiers (GUIDs). Forming a part of the Unified Extensible Firmware Interface (UEFI) standard, it is nevertheless also used for some BIOSs, because of the limitations of master boot record (MBR) partition tables, which use 32 bits for logical block addressing (LBA) of traditional 512-byte disk sectors.
In Linux systems, initrd is a scheme for loading a temporary root file system into memory, to be used as part of the Linux startup process. initrd and initramfs refer to two different methods of achieving this. Both are commonly used to make preparations before the real root file system can be mounted.
The boot ROM is a type of ROM that is used for booting a computer system. There are two types: a mask boot ROM that cannot be changed afterwards and a boot EEPROM, which can contain an UEFI implementation.

Das U-Boot is an open-source boot loader used in embedded devices to perform various low-level hardware initialization tasks and boot the device's operating system kernel. It is available for a number of computer architectures, including 68k, ARM, Blackfin, MicroBlaze, MIPS, Nios, SuperH, PPC, RISC-V and x86.

The EFIsystem partition or ESP is a partition on a data storage device that is used by computers that have the Unified Extensible Firmware Interface (UEFI). When a computer is booted, UEFI firmware loads files stored on the ESP to start operating systems and various utilities.
The Linux booting process involves multiple stages and is in many ways similar to the BSD and other Unix-style boot processes, from which it derives. Although the Linux booting process depend very much on the computer architecture, those architectures share similar stages and software components, including system startup, bootloader execution, loading and startup of a Linux kernel image, and execution of various startup scripts and daemons. Those are grouped into 4 steps: system startup, bootloader stage, kernel stage, and init process. When a Linux system is powered up or reset, its processor will execute a specific firmware/program for system initialization, such as Power-on self-test, invoking the reset vector to start a program at a known address in flash/ROM, then load the bootloader into RAM for later execution. In personal computer (PC), not only limited to Linux-distro PC, this firmware/program is called BIOS, which is stored in the mainboard. In embedded Linux system, this firmware/program is called boot ROM. After being loaded into RAM, bootloader will execute to load the second-stage bootloader. The second-stage bootloader will load the kernel image into memory, decompress and initialize it then pass control to this kernel image. Second-stage bootloader also performs several operation on the system such as system hardware check, mounting the root device, loading the necessary kernel modules,... Finally, the very first user-space process starts, and other high-level system initializations are performed.
Android is a mobile operating system based on a modified version of the Linux kernel and other open-source software, designed primarily for touchscreen mobile devices such as smartphones and tablets. Android is developed by a consortium of developers known as the Open Handset Alliance, though its most widely used version is primarily developed by Google. It was unveiled in November 2007, with the first commercial Android device, the HTC Dream, being launched in September 2008.
A mobile operating system is an operating system for smartphones, tablets, smartwatches, smartglasses, or other non-laptop personal mobile computing devices. While computers such as typical/mobile laptops are "mobile", the operating systems used on them are generally not considered mobile ones, as they were originally designed for desktop computers that historically did not have or need specific mobile features. This line distinguishing mobile and other forms has become blurred in recent years, due to the fact that newer devices have become smaller and more mobile unlike hardware of the past. Key notabilities blurring this line are the introduction of tablet computers and light-weight laptops and the hybridization of the two in 2-in-1 PCs.
Rooting is the process by which users of Android devices can attain privileged control over various subsystems of the device, usually smartphones. Because Android is based on a modified version of the Linux kernel, rooting an Android device gives similar access to administrative (superuser) permissions as on Linux or any other Unix-like operating system such as FreeBSD or macOS.
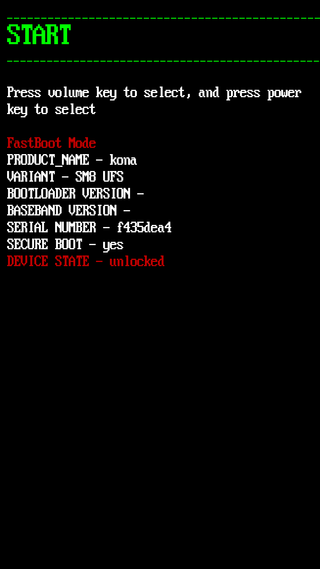
Fastboot is a communication protocol used primarily with Android devices. It is implemented in a command-line interface tool of the same name and as a mode of the bootloader of Android devices. The tool is included with the Android SDK package and used primarily to modify the flash filesystem via a USB connection from a host computer. It requires that the device be started in Fastboot mode. If the mode is enabled, it will accept a specific set of commands, sent through USB bulk transfers. Fastboot on some devices allows unlocking the bootloader, and subsequently, enables installing custom recovery image and custom ROM on the device. Fastboot does not require USB debugging to be enabled on the device. To use fastboot, a specific combination of keys must be held during boot.
The hacking of consumer electronics is an increasingly common practice that users perform to customize and modify their devices beyond what is typically possible. This activity has a long history, dating from the days of early computer, programming, and electronics hobbyists.
Samsung Knox is a proprietary security and management framework pre-installed on most Samsung mobile devices. Its primary purpose is to provide organizations with a toolset for managing work devices, such as employee mobile phones or interactive kiosks. Samsung Galaxy hardware, as well as software such as Secure Folder and Samsung Wallet, make use of the Knox framework.

The Xiaomi Redmi 1S, code-named armani HM 1S, is a smartphone released in May 2014, developed by the Chinese company Xiaomi Inc. It is a part of the Redmi series of smartphones, and succeeded the Redmi 1. Visually similar to its predecessor, it comes with a 4.7-inch screen, a quad-core 1.6 GHz Cortex-A7 processor and runs Android version 4.3 (Jellybean), bundled with the proprietary MIUI v5 user interface, which can be upgraded to MIUI v9 based on Android 4.4.4 KTU84P.
iBoot is the stage 2 bootloader for all Apple products. It replaces the old bootloader, BootX. Compared with its predecessor, iBoot improves authentication performed in the boot chain.

postmarketOS is an operating system primarily for smartphones, based on the Alpine Linux distribution.

Bootloader unlocking is the process of disabling the bootloader security that makes secure boot possible. It can make advanced customizations possible, such as installing a custom firmware. On smartphones this can be a custom Android distribution or another mobile operating system. Some bootloaders are not locked at all, others can be unlocked using a standard command, others need assistance from the manufacturer. Some do not include an unlocking method and can only be unlocked through a software exploit.

The Android recovery mode is a mode of Android used for installing updates and wipe data. It consists of a Linux kernel with ramdisk on a separate partition from the main Android system.

The PinePhone Pro is a smartphone developed by Hong Kong-based computer manufacturer Pine64. The phone is the successor to the PinePhone released in 2019. The default operating system is Manjaro ARM, with Plasma Mobile as the user interface. The device is a developer platform with open hardware specifications but with unfinished software. The target group of the device is free and open-source software developers who will develop the software. The device was first shipped to developers in December 2021, and in February 2022 devices were made available to consumers.
References
- 1 2 Garri, Khireddine; Kenaza, Tayeb; Aissani, Mohamed (October 2018). "A Novel approach for bootkit detection in Android Platform". 2018 International Conference on Smart Communications in Network Technologies (SaCoNeT). IEEE. pp. 277–282. doi:10.1109/saconet.2018.8585583. ISBN 978-1-5386-9493-0. S2CID 56718094.
- ↑ "Android Verified Boot [LWN.net]". LWN.net . Archived from the original on 2015-04-22. Retrieved 2021-09-25.
- ↑ Yuan, Pengfei; Guo, Yao; Chen, Xiangqun; Mei, Hong (March 2018). "Device-Specific Linux Kernel Optimization for Android Smartphones". 2018 6th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud). pp. 65–72. doi:10.1109/MobileCloud.2018.00018. ISBN 978-1-5386-4879-7. S2CID 13742883.
- 1 2 Hay, Roee (2017-08-14). "fastboot oem vuln: android bootloader vulnerabilities in vendor customizations". Proceedings of the 11th USENIX Conference on Offensive Technologies. WOOT'17. Vancouver, BC, Canada: USENIX Association: 22.
- ↑ Alendal, Gunnar; Dyrkolbotn, Geir Olav; Axelsson, Stefan (2018-03-01). "Forensics acquisition — Analysis and circumvention of samsung secure boot enforced common criteria mode". Digital Investigation. 24: S60–S67. doi:10.1016/j.diin.2018.01.008. hdl: 11250/2723051 . ISSN 1742-2876.
- ↑ "Exploiting Qualcomm EDL Programmers (1): Gaining Access & PBL Internals". alephsecurity.com. 2018-01-22. Retrieved 2021-09-13.
- 1 2 Yuan, Pengfei; Guo, Yao; Chen, Xiangqun; Mei, Hong (March 2018). "Device-Specific Linux Kernel Optimization for Android Smartphones". 2018 6th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud). IEEE. pp. 65–72. doi:10.1109/mobilecloud.2018.00018. ISBN 978-1-5386-4879-7. S2CID 13742883.
- 1 2 Kanonov, Uri; Wool, Avishai (2016-10-24). "Secure Containers in Android". Proceedings of the 6th Workshop on Security and Privacy in Smartphones and Mobile Devices. SPSM '16. New York, NY, USA: ACM. pp. 3–12. doi:10.1145/2994459.2994470. ISBN 9781450345644. S2CID 8510729.
- ↑ Tao, Chen, Yue Zhang, Yulong Wang, Zhi Wei (2017-07-17). Downgrade Attack on TrustZone. OCLC 1106269801.
{{cite book}}: CS1 maint: multiple names: authors list (link) - ↑ Tang, Qinghao (2021). Internet of things security: principles and practice. Fan Du. Singapore. p. 166. ISBN 978-981-15-9942-2. OCLC 1236261208.
{{cite book}}: CS1 maint: location missing publisher (link) - ↑ Alendal, Gunnar; Dyrkolbotn, Geir Olav; Axelsson, Stefan (March 2018). "Forensics acquisition — Analysis and circumvention of samsung secure boot enforced common criteria mode". Digital Investigation. 24: S60–S67. doi:10.1016/j.diin.2018.01.008. hdl: 11250/2723051 . ISSN 1742-2876.
- ↑ Zhao, Longze; Xi, Bin; Wu, Shunxiang; Aizezi, Yasen; Ming, Daodong; Wang, Fulin; Yi, Chao (2018). "Physical Mirror Extraction on Qualcomm-based Android Mobile Devices". Proceedings of the 2nd International Conference on Computer Science and Application Engineering. Csae '18. New York, New York, USA: ACM Press. pp. 1–5. doi:10.1145/3207677.3278046. ISBN 9781450365123. S2CID 53038902.
